Photo Gallery
 |

 |
Elastic SOC


Additional Info
| Company | Trusted Metrics |
| Website | http://www.trustedmetrics.com |
| Company size (employees) | 10 |
| Type of solution | Hybrid |
Overview
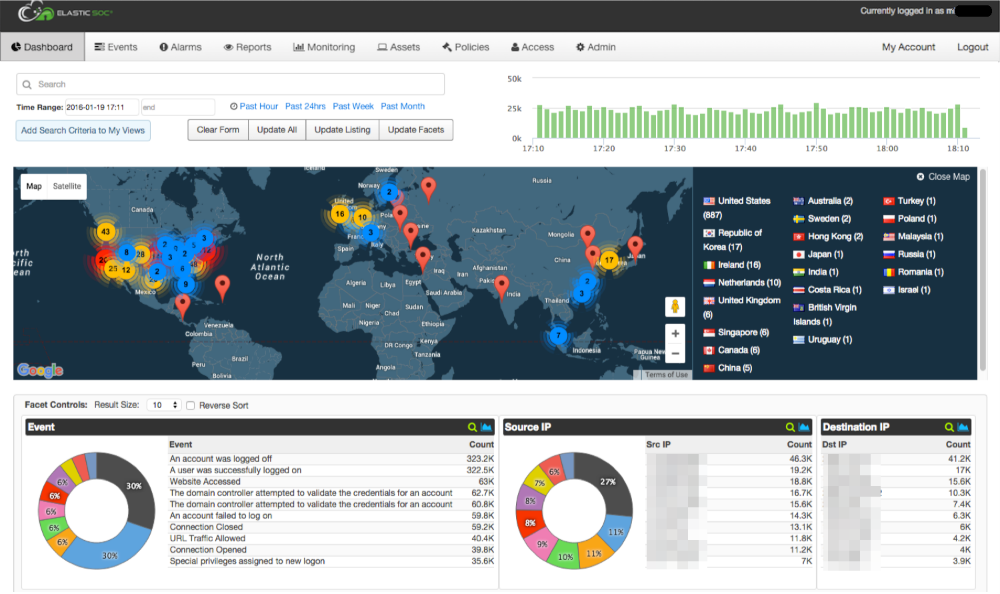
The Elastic Security Operations Center (Elastic SOC®) is a cloud-based platform that collects security event logs, correlates them against threat intelligence and provides actionable analytics via alarms, dashboards and reports. It combines event correlation and real-time alerting with long-term data retention in an easy-to-use web portal.
Elastic SOC® offers the detection, prevention and awareness capabilities necessary for providing real-time statistics on critical business functions, while providing the tools needed for routine troubleshooting of events and making informed response decisions.
The platform provides superior security monitoring by unifying the following functions:
Event Aggregation: aggregates log data from any source, including network and security devices, servers, databases, and applications; thereby, providing the ability to correlate event data in a single console.
Intrusion Detection: by monitoring strategically placed network taps and/or switch monitoring ports, IDS Collectors analyze all inbound and outbound traffic for known patterns that indicate a security-related event, such as a protocol violation, virus infection or inbound attack.
Real-time Alerting: based on pre-canned and custom, multi-level Alarm Policies, undesirable correlated event activities generate real-time alerts that trigger an investigation. Alarm notifications can be integrated with a client’s pre-existing trouble ticketing systems.
Reporting: On-demand or scheduled reports can be configured to summarize event types and provide high-level or detailed operational views into events, such as configuration changes, file integrity changes, malware infections, top offenders, etc.
Custom Dashboards: providing graphical, high-level summary of collected events and alarms, users can configure their own dashboards and event views allowing quick access to specific events of interest.
Forensic Archival: Logs and Events are permanently archived to local NAS or SAN storage for historical retrieval and compliance purposes.
Vulnerability Management: Elastic SOC® integrates with Nessus and Qualys vulnerability assessment APIs to give added insight into assets and provide additional data modeling and trending activity for vulnerability assessment activities.
How we are different
- Elastic SOC® is a SaaS-based security monitoring/visibility platform built on a SIEM foundation, unifying multiple monitoring capabilities. It has reduced the need for disparate, redundant and costly technologies. It currently serves both the SMB market and large enterprise network environments.
- Elastic SOC® supports multi-tenancy and can be white-labeled. This allows Managed Service Providers (MSP) and Managed Security Services Providers (MSSP) to offer their clients that same level of enterprise security monitoring only seen in large-scale network environments, via a distributed cost model. Elastic SOC® is “Elastic” at it’s core. There is no concept of having to distribute clients across multiple SQL-based databases, file stores or UI consoles.
- Elastic SOC® Collector can be deployed to a client in as little as 20 minutes on either a physical server or virtual machine, immediately integrate with existing threat protection packages, and directly connect with a client’s Active Directory for added contextual data and immediate event flows. It is a true SOC-as-a-Service platform.



