Photo Gallery

|

|
Interset


Additional Info
| Company size | 50 employees |
| Website | https://www.interset.com/ |
NOMINATION HIGHLIGHTS
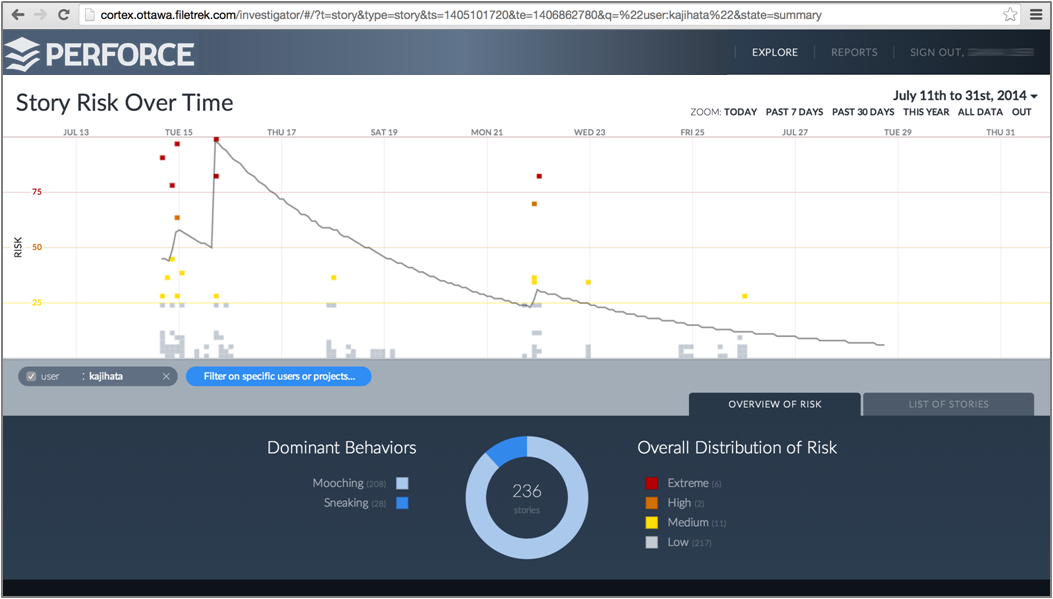
Interset was recently selected in a large government RFP as the most complete User Behavior Analytics product. This category has emerged as arguably the most competitive innovation technology in info security for its ability to solve the false positives problem. Our approach is unique in connecting accounts, files, machines and applications and tying them to risk scores. These scores change with each new activity; stages of an attack are defined with risk growing as stages progress. This “connect the dots” approach surfaces attacks earlier and removes noise and false positives. Interset is the only behavior analytics product that can scale to collect, process and analyze very large amounts of data from endpoints ,directories, servers, relational database logs, source code management, product lifecycle applications, finance/HR systems, and SharePoint.
We jointly created with Perforce Software the only IP threat detection product integrated with a source code and content management system.
How we are different
* Customers include several leading security companies themselves as our patent has been proven highly effective in detecting and surfacing compromised-account and insider attacks while reducing false positives. The Interset Threat Analytics Cloud (I-TAC) is industry’s only big-data, behavior-analytics, threat- detection platform delivered as a cloud service.
* integration between the Interset Advanced Threat Detection Platform and the FireEye Threat Analytics Platform (TAP) correlates high-risk inside threats detected and surfaced by Interset with perimeter threats uncovered by FireEye TAP. The integration will deliver unprecedented insight into how enterprises are being attacked, what stage the attack is in, and the actions needed to stop an attack before it compromises data.
* Interset’s integration with McAfee ESM enables ESM customers to take advantage of Interset’s threat analytics by viewing predicted behavioral threats with ESM for further investigation and incident response.

