Preempt Behavioral Firewall
Photo Gallery
 |
 |
Preempt Behavioral Firewall

Additional Info
| Company | Preempt |
| Website | http://www.preempt.com |
| Company size (employees) | 30 |
| Type of solution | Software |
Overview
Today’s security breaches and insider threats have morphed dramatically in frequency and sophistication, leading to the hyper-focus on monitoring who and what is on an organization’s network. As a result, security teams are overwhelmed by chasing security alerts, many of which are false positives or of unconfirmed severity. To improve security team efficiency, the Preempt Behavioral Firewall deploys real-time automated response mechanisms when abnormal or risky behavior is detected in order to preempt potential threats from malicious attackers or insiders. This improves the team’s productivity and provides more efficient incident resolution, enabling them to gather relevant breach information in a matter of minutes rather than hours or days.
Preempt’s policy-based approach combines User and Entity Behavior Analytics (UEBA) with adaptive response to act like an internal firewall, allowing security teams to detect and prevent attacks and high-risk incidents, saving critical time when mitigating today’s growing network complexities. It protects the very sensitive Directory Services infrastructure, which allows access to services in the network (file servers, Sharepoint and other machines).
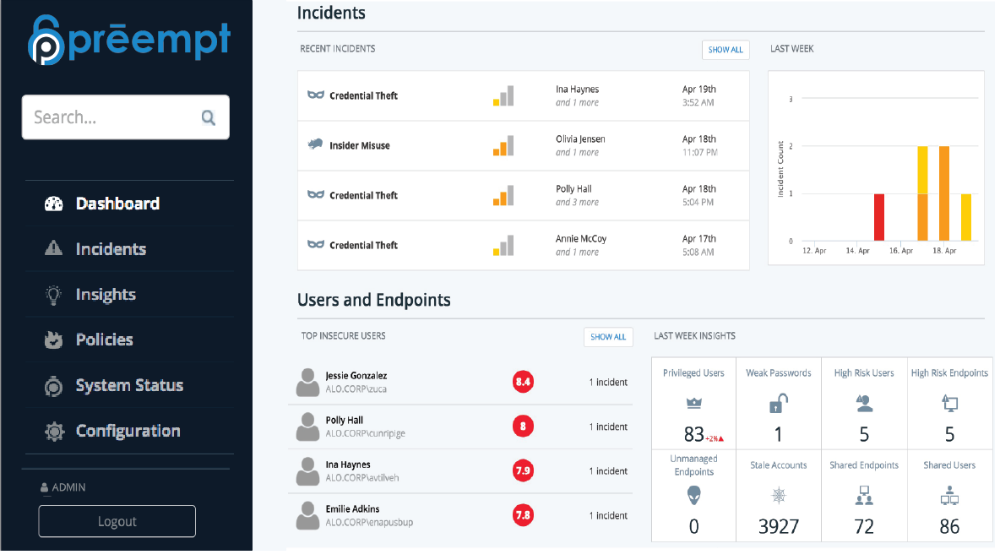
The Preempt Behavioral Firewall offers security teams the insights necessary to account for transitioning user roles within an organization, delineating between definite or probable attacks, and knowing which users are compromised or those at high risk.
With an innovative policy engine, the Preempt Behavioral Firewall also facilitates smart adaptive security controls that are context-aware. It incorporates ongoing user behavior so security teams don’t have to keep updating it as users change, their roles change, their projects change, etc. When a suspicious activity occurs, Preempt automatically responds. It engages directly with the user to verify their identity and can automatically apply a policy to block, notify, force re-authentication or challenge users with multi-factor authentication, allowing security teams to focus more on real threats and less on chasing alerts.
How we are different
The Preempt Behavioral Firewall stands out from the competition in three significant ways:
- It introduces an entirely new class of firewall focused on the inside of the network. Although next gen firewalls are good on the perimeter and for network segmentation, the Preempt Behavioral Firewall identifies insider threats and breaches, so they are solving different problems. There are some that think you can use a next gen firewall for this purpose, but they provide limited value, as they cannot analyze user behavior and their blunt response capabilities interrupt business processes.
- It also differs from traditional UEBA solutions, which only do detection, by delivering the first solution that combines user behavior analysis with adaptive response in order to automatically respond in real-time to and prevent threats before data is lost or reputation is harmed.
- It delivers the most proactive solution for protecting the Directory Services infrastructure. Only the Preempt Behavioral Firewall protects sensitive directory services by detecting and preventing attacks that could disrupt an organization’s operations. The innovative adaptive policy engine is able to assign and enforce policies that govern access to all internal resources.



