ThreatMatrix Deception and Response Platform
Photo Gallery
 |

 |
ThreatMatrix Deception and Response Platform


Additional Info
| Company | Attivo Networks |
| Website | http://www.attivonetworks.com |
| Company size (employees) | 99 |
| Type of solution | Hybrid |
Overview
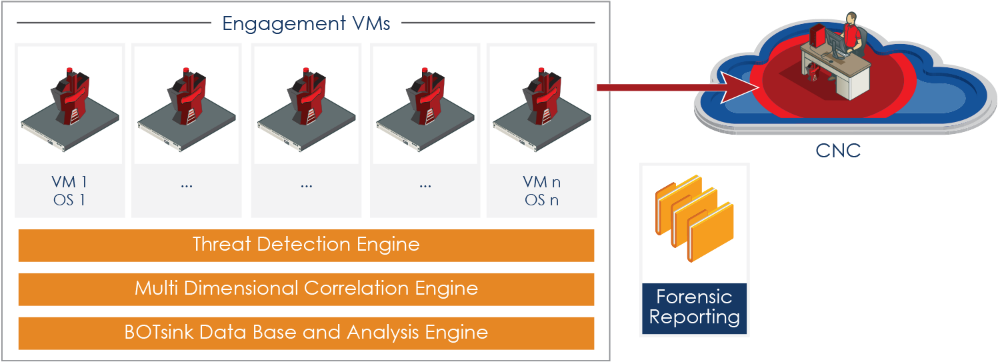
Lack of standards and security controls have left IoT solutions ripe for the advanced attacker. The ThreatMatrix Platform closes the gaps in IoT Security with efficient, real-time threat detection and attack forensics for accelerated incident response.
The Platform is designed to efficiently detect all forms of attacks on IOT systems and is not reliant on knowing attack signatures or on unreliable pattern matching. Instead, Attivo provides deception decoys and lures so that customers can set up traps that look identical to IoT systems based on XMPP, COAP, MQTT, HL7 and DICOM based PACS servers in their networks. Customized to appear as production IoT sensors and servers, the solution deceives the attacker into engaging and revealing themselves. Once the attacker is engaged, the attack can be studied and alerts raised so that the infected system can be quarantined and the attack blocked. Detailed forensics reporting is provided to accelerate remediation and future attack prevention.
The ThreatMatrix platform also provides ThreatPath to assess likely attack paths and attack time-lapsed reply so that organizations can understand configuration and credential vulnerabilities and the lateral movement of attacks . This information can then be used for attack prediction and strengthening of their security posture.
How we are different
The ThreatMatrix platform is truly a unique offering that closes the gap for early detection of attacks targeting IoT devices.
With the broad variety of IoT security devices, this solution provides accurate detection of threats and their lateral movement. The alerts are based on engagement so the security team won't be chasing false positives and endless logs.
Third party integrations with major prevention, endpoint, SIEM devices automate incident response with automated blocking and quarantine saving security teams time and energy in quarantine and remediation.



