Virtru
Photo Gallery
 |
 |
Virtru

Additional Info
| Company | Virtru |
| Website | https://www.virtru.com/ |
| Company size (employees) | 40 |
| Type of solution | Software |
Overview
Virtru is built on the Trusted Data Format (TDF), invented by Virtru’s co-founder and CTO, Will Ackerly. The solution gives organizations digital privacy tools that enable them to easily share information securely using popular email programs and apps. TDF is now used by the US Intelligence community to protect data in transit.
In 21st century business dealings, organizations require the ability to protect the privacy of its most sensitive information while also selectively and securely sharing that same information with partners, customers and consumers. When organizations exchange sensitive information over standard email platforms, there is no mechanism to prevent unintended access or unwanted forwards. Ultimately this leads to to a weak business privacy stance, undermines trust, and puts businesses, its customers, and partners, at risk.
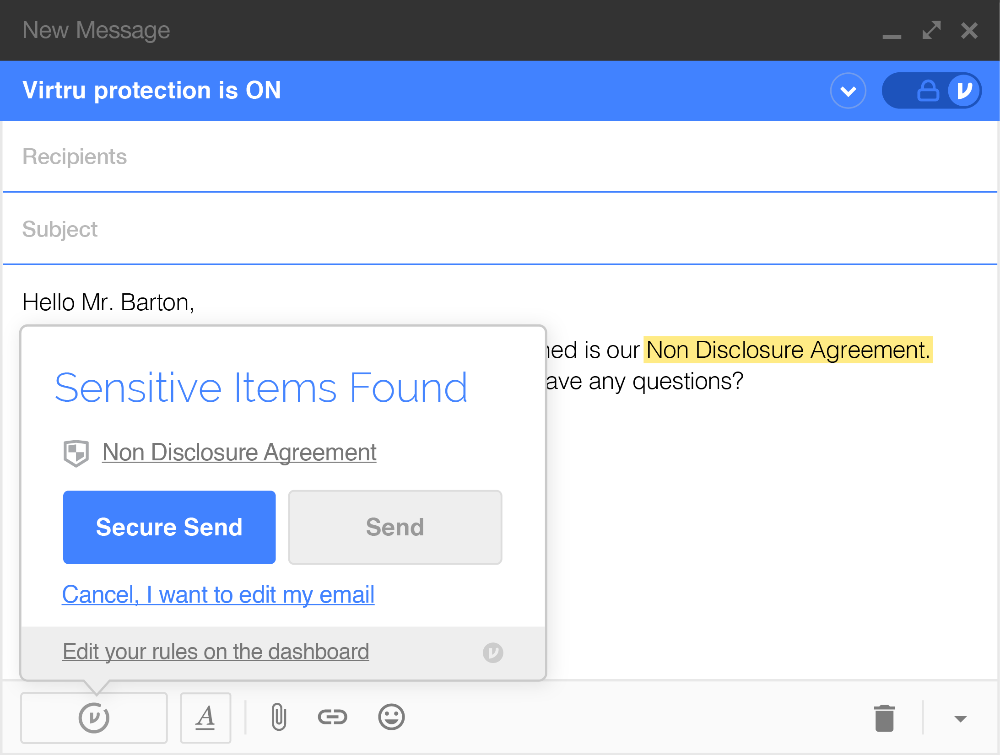
Virtru affords organizations a simple, powerful and trustworthy way to secure sensitive data by wrapping email and digital files in a protected envelope. Message bodies and attachments are end-to-end encrypted, and senders retain the ability to revoke or change access even after messages have been opened or forwarded. Virtru offers Encrypted Search, a feature that enables Virtru senders to search the full email message bodies of the encrypted content that they send from any Virtru platform.
Virtru is a part of the Google Recommended for G Suite program as a provider of the control of data stored and shared in the cloud. Virtru’s Customer Key Server (CKS), allows enterprises to maintain exclusive access to the encryption keys used to secure their data ensuring that only explicitly authorized parties have access to unencrypted content and encryption keys. CKS allows for maximum security, privacy, and control. Virtru customers can change access privileges at any time. Data protection and encryption can be enforced on end-user devices, on the network, or in both places to ensure complete coverage.
How we are different
Virtru is a part of the Google Recommended for G Suite program as a provider of the control of data stored and shared in the cloud. Virtru is the first company to combine extreme ease-of-use with powerful controls to protect emails and attachments. Virtru customers use their existing email service, like Gmail or Outlook to encrypt and protect their messages.
Virtru’s Customer Key Server (CKS) enables enterprises to maintain exclusive access to the encryption keys used to secure their data. As business privacy becomes a top priority for organizations across all industries, the Virtru CKS ensures that only explicitly authorized parties have access to unencrypted content and encryption keys allowing for maximum security, privacy, and control.
Virtru protections travel with customer data throughout its lifespan, regardless of where it’s shared. Individual users and administrators can exert finely tuned control over their data by disabling the option to forward, setting an expiration time, revoking emails or watermarking PDF’s. In October, Virtru announced their partnership with the State of Maryland to secure sensitive information like client names, employee social security numbers, case files, benefit information, etc., in the cloud for more than 15,000 state employees.



