Photo Gallery
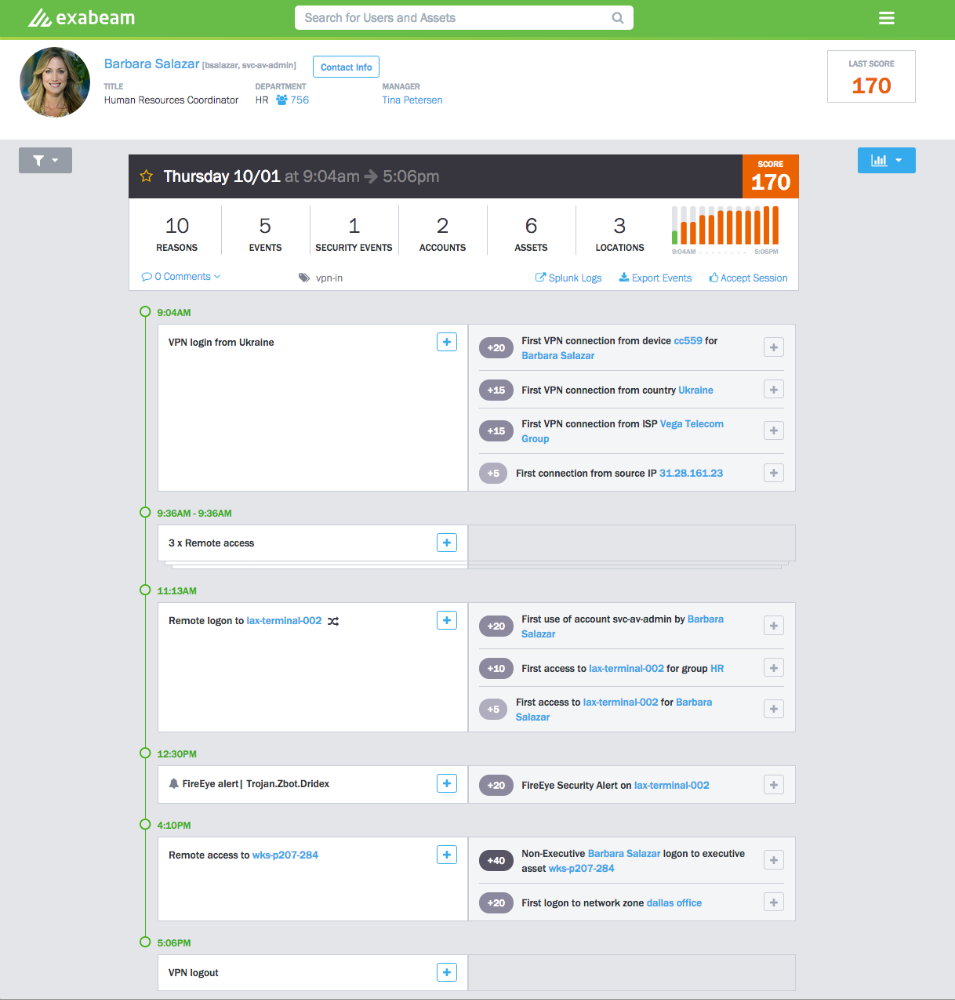 |
Exabeam User Behavior Intelligence Platform

Additional Info
| Company | Exabeam |
| Company size | 75 employees |
| Website | http://www.exabeam.com |
NOMINATION HIGHLIGHTS
Exabeam’s User Behavior Analytics (UBA) Platform “connects the dots” across a user’s activities to detect if stolen credentials are being used to attack a corporate network. As part of the expected ~$9 Billion solutions market, Exabeam is designed to notify security analysts when anomalous behavior takes place.
Historically, SIEM products would be the assumed solution for this problem. However, attacks have changed, shifting from network-based to identity-based, and SIEM products continue to miss them, allowing breaches to occur and failing to help security operations center (SOC) teams respond effectively.
Exabeam detects identity-based attacks and helps SOC staff respond quickly and completely after detection. It uses machine learning to automatically create a unified identity for each user, across all of that user’s IP addresses, devices, and accounts. It then creates per-user baselines of normal behavior, and compares activity to that baseline to determine anomalies and prepares a timeline for guided response.
Exabeam lets customers:
• Quickly identity threats not seen by traditional security products. In more than 50 percent of pilots, Exabeam consistently finds attacks underway that were previously undetected.
• Enhance compliance reporting. Companies often have policies regarding access and attribution of access rights. Exabeam provides attribution of the unauthorized access to the person using the credential at the time.
• Accelerate response. On average, security incidents can take six -10 days to piece together investigation information about accounts compromised and systems affected. By providing this information automatically, Exabeam can eliminate one week per incident of analyst time.
How we are different
• The Exabeam User Behavior Analytics Platform is a specific identity state engine that tracks user sessions across devices, IP addresses and account names. This is unique and is important because attackers typically leave the initial machine, create new accounts or switch IP addresses to avoid detection. Only Exabeam tracks across identity state and this allows us to detect “multi-hop” attacks that other UBA products miss.
• Unlike competing technologies, Exabeam works on existing log data and does not require agents or network taps to be installed. This allows the platform to provide value in a few hours, versus weeks or months.
• By stitching together all of a user’s activity across devices, networks, accounts, etc., Exabeam gives incident response teams a blueprint for next steps, i.e. “Mandiant in a box” which alleviates shortages of expert staff.
Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



