Photo Gallery
|
|
 |
Ericom Shield

Additional Info
| Company | Ericom Software |
| Company size | 100 - 499 employees |
| Website | http://www.ericom.com |
NOMINATION HIGHLIGHTS
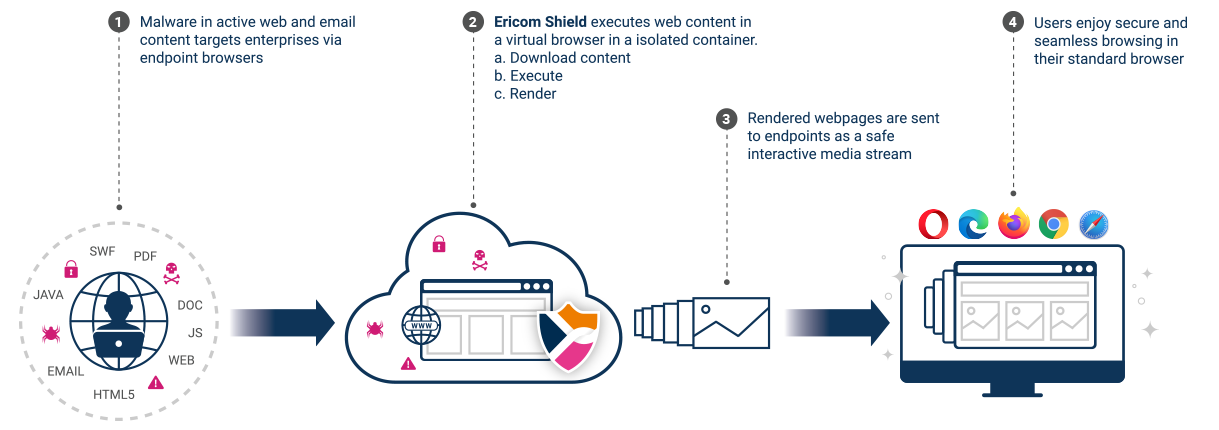
Ericom Shield is a cloud-based service that fundamentally changes the dynamic between hackers and businesses. It creates a unique Zero Trust browser isolation layer that protects organizations as they conduct essential daily activities involving email and the internet while preventing all web-based and email-borne threats from reaching endpoints.
All active web content, including any ransomware and other web-borne threats, is executed in a remote, isolated, cloud-based container. But only an interactive media stream representing the website is sent to the user device browser, providing a safe, seamless, fully interactive user experience. Whether users browse to a malicious site on their own or reach one by clicking a URL embedded in a phishing email, they are completely safe since no web content is ever executed directly on the device.
For additional phishing protection, websites launched from URLs in emails can be rendered in read-only mode to prevent users from entering credentials. Attached files are sanitized before being transmitted to endpoints, ensuring that malware within downloads cannot infect endpoints.
How we are different
• Shield’s isolation approach ensures that no malware hidden in active web content can ever reach a user’s endpoints. The technology takes a Zero Trust approach, assuming that all websites may contain malware, and isolates endpoints from any potential threats. This is fundamentally different than traditional tools like secure web gateways, which attempt to scan and filter website access based on threat intelligence, inevitably letting stealthy malware through. Shield offers a unique “prevention without detection” approach to web security.
• Each browsing session is executed within a cloud-delivered remote, isolated Linux container, which is safely destroyed when session ends. Further, pre-integrated market-leading multi-scan and sanitization technology ensures safe downloads from emails and websites.
• For additional phishing protection, websites launched from URLs in emails can be rendered in read-only mode to prevent users from entering credentials. Attached files are sanitized before being transmitted to endpoints, ensuring that malware within downloads cannot infect endpoints.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



