Proofpoint Targeted Attack Protection and Threat Response
Recognized in the Category:
Photo Gallery
 |
 |
Proofpoint Targeted Attack Protection and Threat Response

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
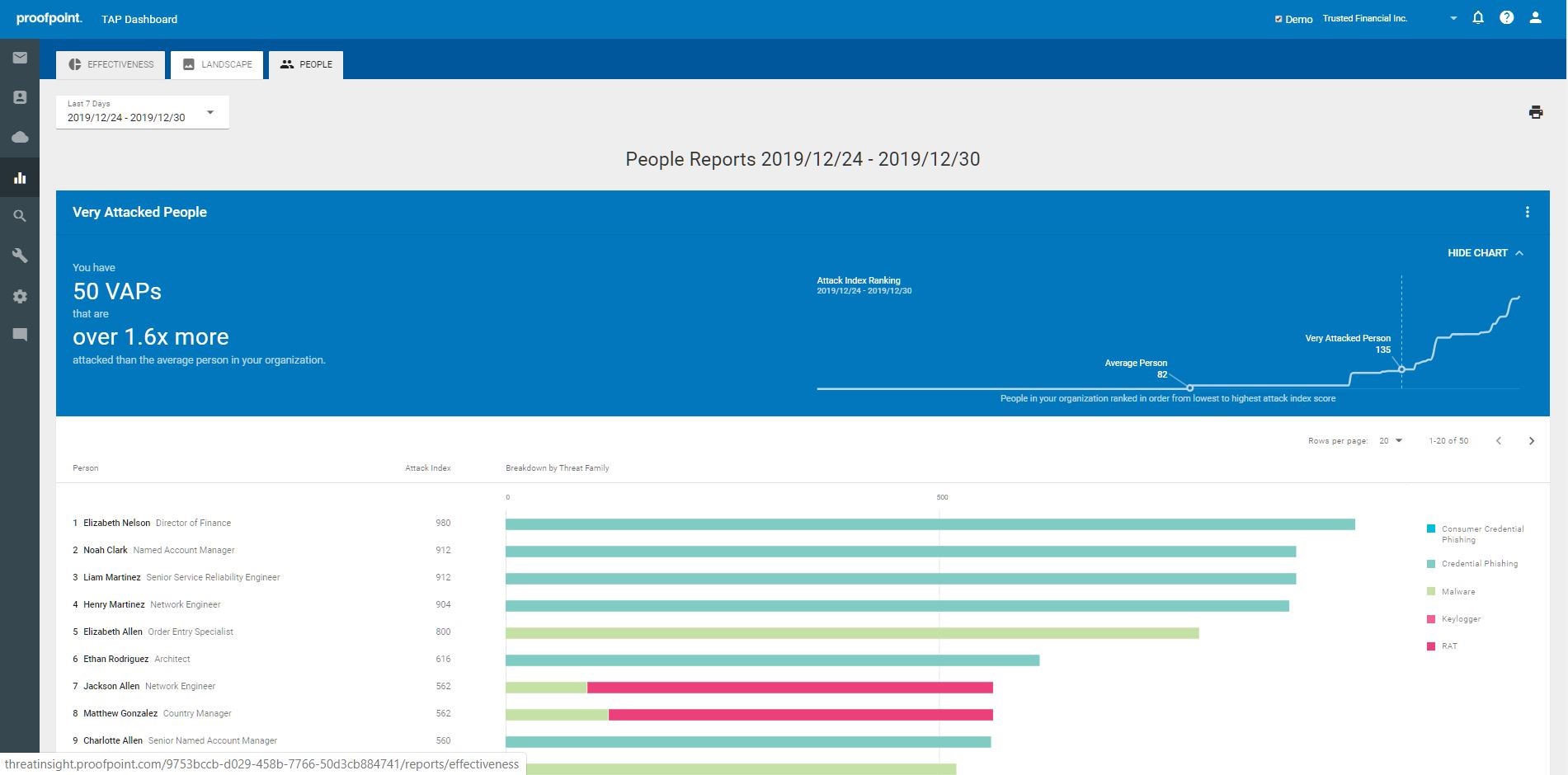
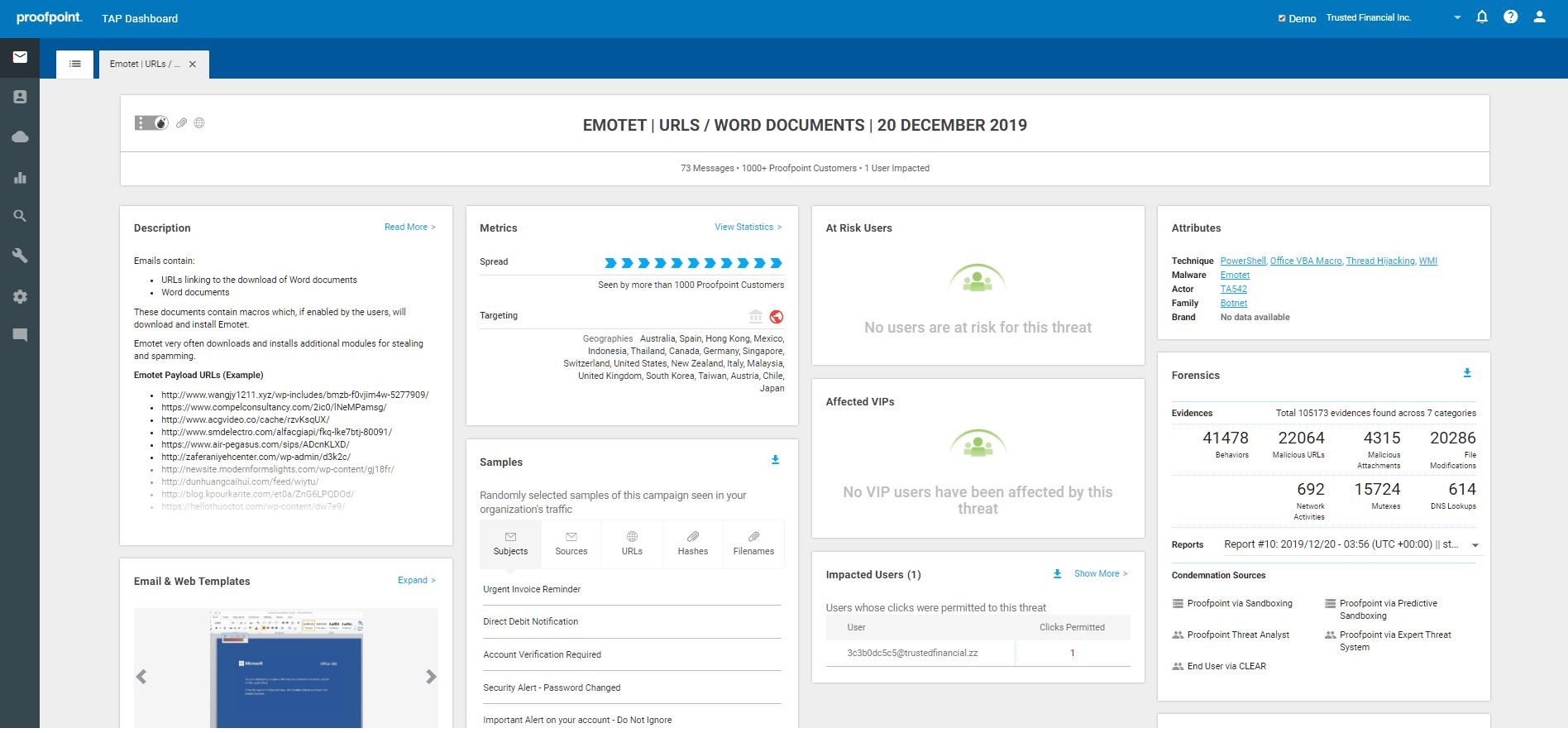
Proofpoint Targeted Attack Protection (TAP) detects threats that target people and their data via the tools they use to conduct business and works with Proofpoint Threat Response (PTR) to respond to these threats. TAP features multiple machine learning engines spanning threat classification, composite multistage threats, relationship and communication classification, key employee classification, and evolving page design classification to not only detect new and emerging threats, but also leverage that data to inform future detection. TAP applies machine learning-led predictive analysis of URLs, detection of malware-free attacks like BEC and credential phishing, and password cracking for zip files. Reports on VIPs and very attacked people (VAP’s) enable incident response prioritization and include forensic markers and why highlighted users are being targeted by threats.
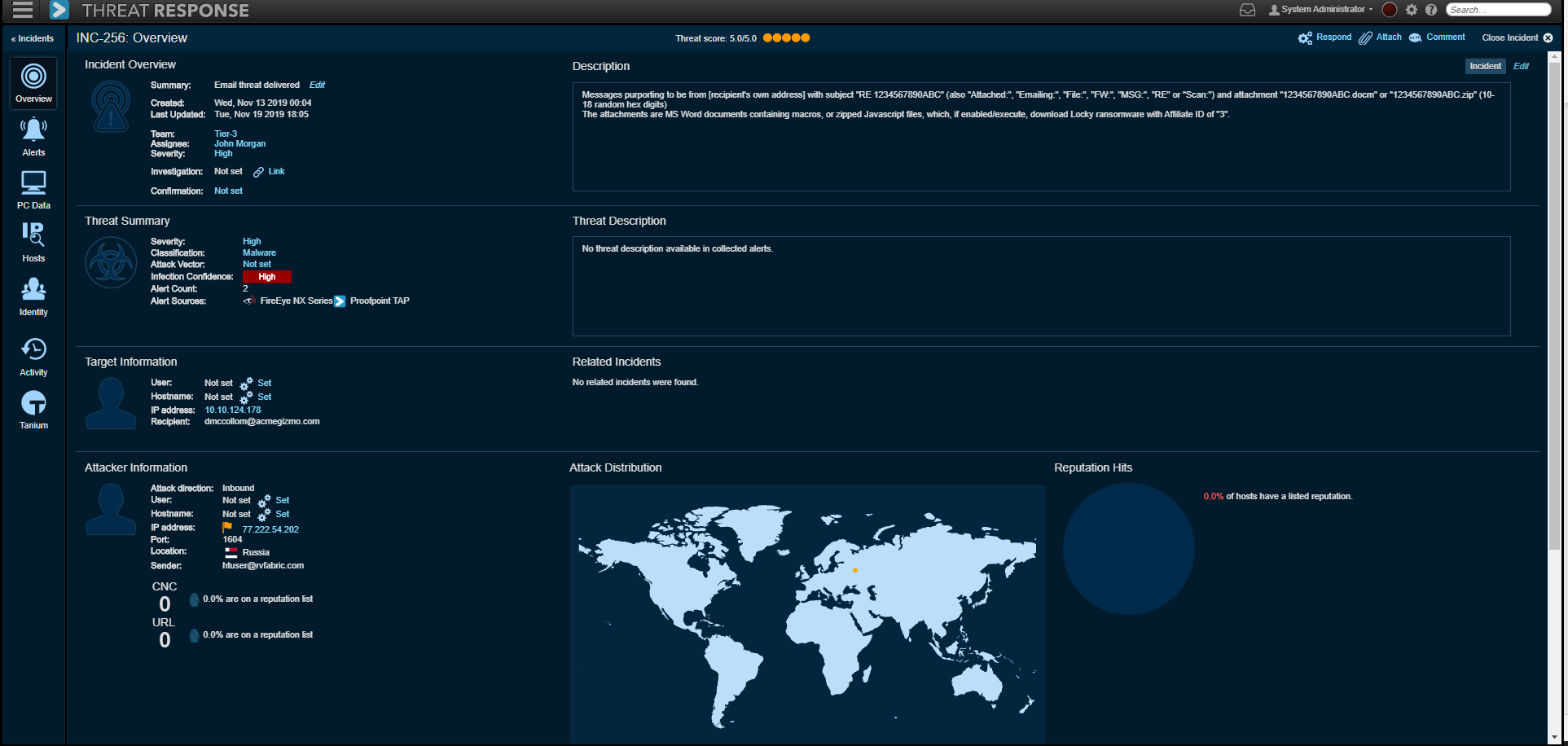
PTR is a force multiplier for security operations that orchestrates and automates incident response. PTR surrounds security alerts with rich contextual data to help security teams prioritize and execute response actions. It collects and analyzes security event context around incidents and investigations, and it collects endpoint forensics to confirm system infections to create actionable profiles of incidents. Based upon the enhanced context, it enables enforcement and quarantine actions automatically or at the push of a button leveraging existing infrastructure.
PTR collects and analyzes endpoint forensics from targeted systems to yield a rich snapshot of indicators of compromise. This information is compared to changes reported by malware analysis tools to provide insight into the health of the client. Based on the forensics collected and analyzed by the system, PTR Response presents a context rich view of the threat that allows analysts to take push-button response actions, identify, areas for additional investigation, or turn on automated response such as retract delivered email from users’ mailboxes, add users to low permission groups, or update blocklists of firewalls and web filters.
How we are different
•TAP differentiation starts with three to five levels of sandboxing, culminating in analyst-led or sandbox analysis and forensics. These sandboxes work alongside multiple machine learning engines spanning threat classification, composite multistage threats, relationship and communication classification, key employee classification, and evolving page design classification. This functionality not only detects new and never seen before threats, but also leverages its data to inform future detection. TAP offers a unique Attack Index capability that provides security teams with a people-centric view into their organization’s security posture which exposes an organizations Very Attacked People (VAP’s).
•Many security alerts lack critical information required to determine the context of a threat and next steps. Proofpoint Threat Response automatically enriches security alerts by collecting important internal and external context, intelligence, and data to create an actionable view of each alert. Armed with this insight, security teams can quickly understand, prioritize, and respond to security threats.
•Proofpoint Threat Response automatically checks every domain and IP provided in security alerts and sandbox reports against its built-in premium intelligence feeds, including Emerging Threats Intelligence. This step removes hours of tedious work and manual one-by-one searching against intelligence services to find attacking IPs and hosts leveraging known bad sites.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



