Photo Gallery
|

|
SpyCloud Third Party Insight


Additional Info
| Company | SpyCloud |
| Company size | 50 - 99 employees |
| Website | http://www.spycloud.com |
NOMINATION HIGHLIGHTS
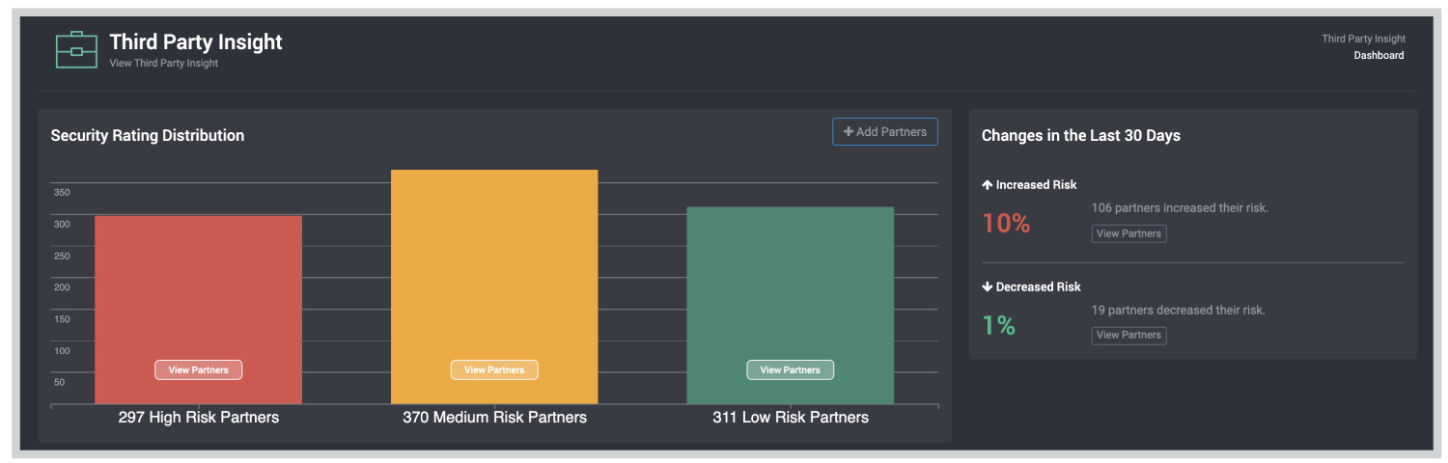
If a third party partner, vendor or supplier with privileged access to your network has their login credentials stolen in a breach, criminals have an easy path to your data and IP. SpyCloud Third Party Insight draws on the largest repository of breach records in the world to give security teams visibility into third-party exposures and take action to remediate. SpyCloud Third Party Insight simplifies vendor risk management with ongoing monitoring of your third parties’ breach exposures. When a new data breach compromises credentials tied to one of your partner companies, SpyCloud alerts users to the change and makes it easy for them to share details with the affected third party.
SpyCloud ingests new breach data all the time, giving users peace of mind that they have visibility of the latest account takeover threats that can weaken vendor cybersecurity and threaten your supply chain. With SpyCloud Third Party Insight, users can identify third-party exposures before criminals can exploit them.
Within the SpyCloud portal, third parties can see the exact employee credentials that have been exposed in data breaches, including plaintext passwords, making it easy for them to reset passwords for affected users and resolve their exposures. This data is not shared with the enterprise; only with the affected third party. The enterprise only sees a risk score and is made aware that a third party has exposed credentials that require remediation.
SpyCloud Third Party Insight goes beyond vendor risk management, giving you visibility of potential targets for mergers and acquisitions. By assessing prospective prospective M&A targets’ account takeover exposures, you can identify potential red flags that could endanger the partnership and make sure any compromised credentials are remediated before you join forces.
How we are different
Actionable data: Many vendor risk management solutions fall short when it comes to enabling high-risk vendors to close their security gaps. In contrast, SpyCloud Third Party Insight makes it easy to share full details with affected parties so they can remediate.Within the SpyCloud portal, third parties can see the exact employee credentials that have been exposed in data breaches, including plaintext passwords, making it easy for them to reset passwords for affected users and resolve their exposures.
Earliest possible data recovery: SpyCloud uses human intelligence and works undercover in the cybercriminal underground to obtain email addresses, passwords and other PII straight from criminals immediately after a breach. This unique collection method means SpyCloud recovers stolen data 18+ months sooner than other threat intelligence providers, which is critical because every second counts when it comes to securing data after a breach.
Most robust breach data collection: As a result of SpyCloud’s unique combination of human intelligence and early data recovery, the company maintains the largest collection of breach data, composed of more than 113 billion breach assets, helping businesses to find more compromises, which include those of critical partners, vendors and suppliers.


