Photo Gallery
 |

 |
Bitglass CASB

Additional Info
| Company | Bitglass |
| Company size | 100 - 499 employees |
| Website | https://www.bitglass.com |
NOMINATION HIGHLIGHTS
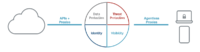
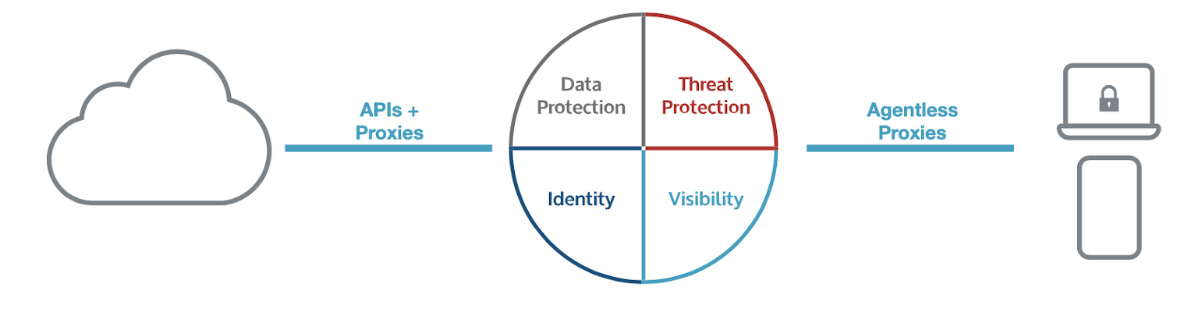
Bitglass’ multi-mode cloud access security broker (CASB) enables enterprises to secure any SaaS apps, IaaS instances, data lakes, and private apps built on any platform. It uses machine-learning techniques to deliver real-time data and threat protection across the dynamic enterprise cloud footprint, and automatically learns and adapts to new or updated cloud applications, malware threats, user behaviors, and more–across any app or device. The cloud-first security solution boasts an agentless architecture, provides end-to-end security and comprehensive visibility over corporate data, limits risky external sharing, and prevents data leakage. It is one part of Bitglass’ integrated SASE platform, along with Bitglass’ SmartEdge SWG and real-time ZTNA.
Bitglass’ CASB enables IT departments to adopt cloud and BYOD by filling critical security and compliance gaps. Because the agentless solution can be rolled out quickly and with no software installations required (which is helpful when securing remote work and crucial in BYOD environments), customers report large operational cost savings. Unlike frustrating, agent-based tools that demand software installations on personal devices, Bitglass secures data and offers specialized security capabilities without invading user privacy. From a business perspective, organizations in heavily regulated and security-conscious industries–such as healthcare and financial services–can rely on Bitglass to safely deploy the tools that their businesses need to remain competitive.
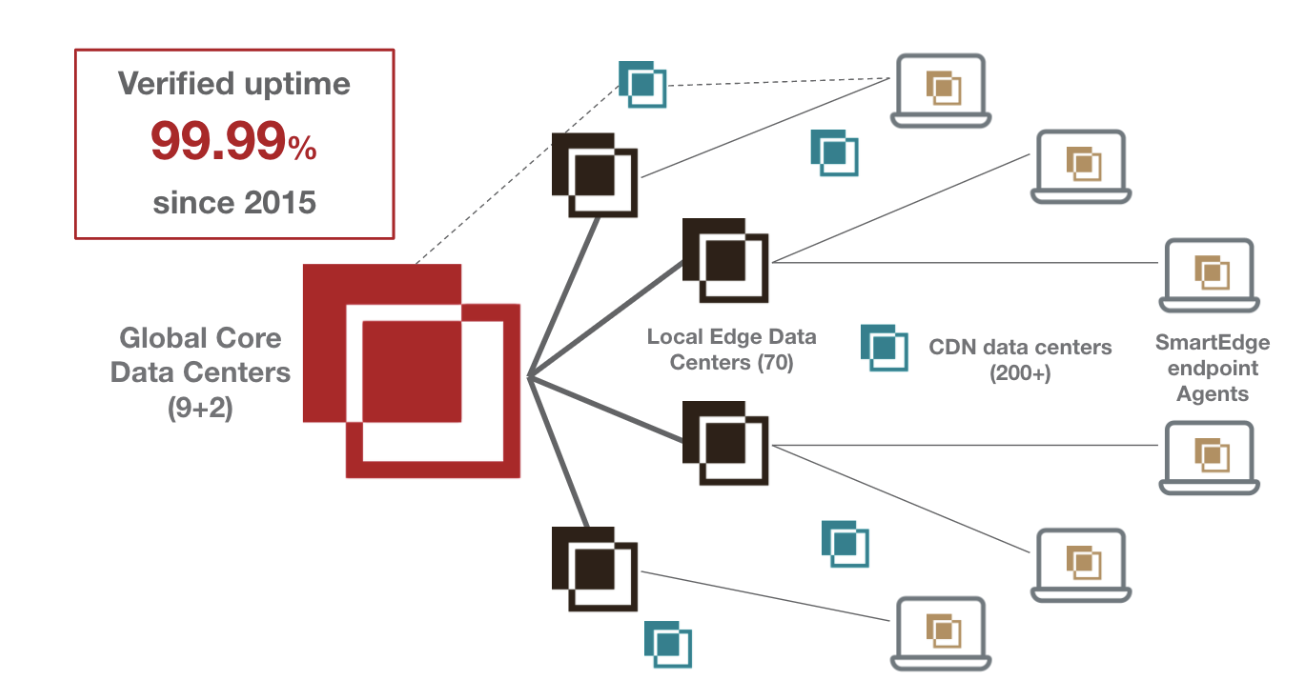
The Bitglass CASB is built on a fabric deployed globally on the public cloud, at more than 280 points of presence. Bitglass’ Polyscale Architecture automatically scales with load changes to maximize performance and business continuity around the clock and across the globe. Bitglass has delivered 99.99% uptime since 2015 as measured and published independently by SolarWinds/Pingdom. Additionally, users report faster access to critical business applications via the Bitglass proxy, which optimizes the flow of traffic to accelerate performance.
How we are different
- Bitglass provides the only CASB with searchable, full-strength encryption. Most CASBs are forced to choose between full-strength encryption that breaks key functionality like search and sort, and weak, easily breakable encryption that enables said functionality. Fortunately, due to its patented technology, Bitglass provides 256-bit AES encryption with 256-bit initialization vectors that can still allow search and sort--providing enterprises with top-notch encryption without sacrificing functionality.
- Unlike competitors, Bitglass is the only CASB with a proven multi-mode architecture, using a combination of proxies and API integrations to ensure complete coverage against all risk of data leakage as sensitive information migrates beyond the corporate firewall. Through forward proxy, reverse proxy, and API integrations, Bitglass can secure any app or device. Our competitors have yet to achieve agentless reverse proxy with the same reliability because they lack Bitglass’ AJAX-VM, patented technology needed for robust reverse proxy functionality, which is critical for securing personal devices. Consequently, Bitglass’ CASB is the only one with agentless, real-time advanced threat protection that is capable of detecting zero-day threats at upload, at download, and at rest.
- Bitglass’ CASB can single-handedly replace multiple disjointed, outdated solutions that require updates on endpoints and prove to be both time consuming and invasive to privacy. For example, Bay Cove Human Services, a 2,000-employee healthcare organization, was seeking to deploy an identity and access management solution, a mobile device management tool, and a CASB. After extensive testing between different CASBs, Bitglass was selected to satisfy the requirements of all three. Bitglass’ solution reduces the overall cost to the organization while providing comprehensive data protection, zero-day threat protection, robust identity and access management, and complete visibility wherever protected health information and other sensitive data goes.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



