Exabeam Security Management Platform
Recognized in the Category:
Photo Gallery
 |
|
|
Exabeam Security Management Platform


Additional Info
| Company | Exabeam |
| Company size | 100 - 499 employees |
| Website | https://exabeam.com |
NOMINATION HIGHLIGHTS
Exabeam’s Security Management Platform (SMP) allows security teams to outsmart the odds by adding intelligence to their existing security tools. Out-of-the-box use case coverage delivers repeatable outcomes, greatly reducing burnout for understaffed and overwhelmed security teams who are already stretched thin.
With organizations rapidly increasing their cloud consumption in the age of remote work, The Exabeam SMP allows organizations to detect improper access of cloud storage objects and defend against threats to cloud-based data on AWS, Google Cloud and Microsoft Azure.
Insider threats typically go under the radar due to the threat actor posing as a legitimate user. The Exabeam SMP provides real-time mapping of logs to attribute behavior to users and devices. With data enhancement and context, security teams have visibility into abnormal behavior and risky activity to stop insider threats.
In traditional SIEMs, investigations can consume upwards of 70% of analyst time. The Exabeam SMP includes automation that reduces the time it takes analysts to detect, triage, investigate and respond to incidents by 51%, including automated connectors to cloud resources, out-of-the-box detection rules and models, automated timeline creation, behavioral threat hunting, response actions and turnkey playbooks.
The Exabeam SMP includes all of the modern SIEM components – a cloud data lake; user and entity behavioral analytics (UEBA); and security, orchestration and automated response (SOAR) – to help organizations stay as secure as possible.
The Exabeam SMP can be deployed on cloud infrastructure, as software-as-a-service or through a managed security service provider as well as on-premises, helping organizations accelerate their transition to the cloud securely.
How we are different
Industry-leading UEBA
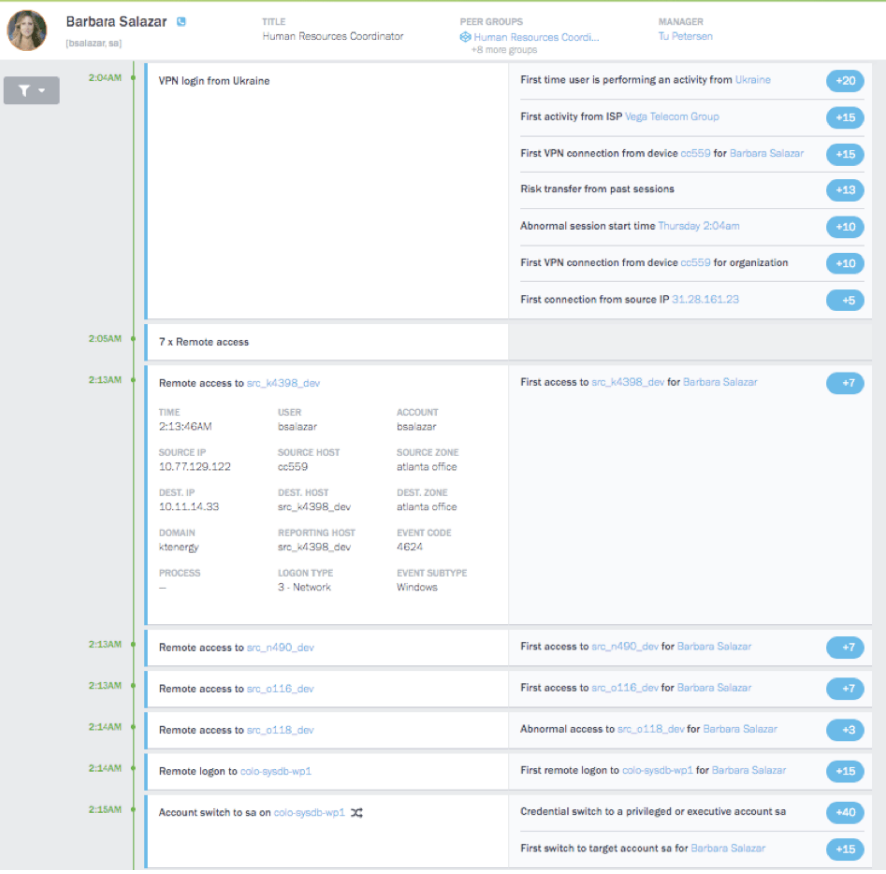
Threat detection comes from market-leading Exabeam UEBA allows analysts to track abnormal behavior including lateral movement, credential switches and privilege escalations that would be difficult, if not impossible, to detect with traditional security management tools.
End-to-End Automation
Exabeam improves efficiency at every step of security operations workflow by eliminating mundane and repetitive tasks through automation. A few notable examples include:
Exabeam Cloud Connectors allow organizations to reliably collect logs and initiate response actions for over 40 cloud services.
Behavioral analytics automatically detects user and device behaviors indicative of a threat. Some refer to it as “automatic correlation.”
Exabeam speeds analysts’ work by providing them with actionable insights during triage and investigation. Alert enhancement and automated incident timelines, provide real-time actionable intelligence to expedite decision making during alert triage and investigation.
Response automation, including turnkey playbooks that incorporate third party technology without requiring customers to bring their own license for those technologies, make incident responders more efficient.
Repeatable Outcomes
Exabeam use case coverage helps organizations solve specific problems by providing visibility, detection logic and response procedures out-of-the-box. Analysts can employ use case content and features for each stage of their workflow, not just detection. Exabeam also provides clear guidance on the data sources that are needed for security teams to protect against external and internal threats.
Organizations can deploy complete coverage for 3 categories of threats including compromised and malicious users:
Insider threats: including use case coverage for privilege access abuse, account manipulation, physical access, data access, data exfiltration and evasion.
Compromised users: including use case coverage for account manipulation, privilege escalation, compromised credentials, and lateral movement.
External threats such as phishing, malware, and ransomware.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



