Photo Gallery

|

|
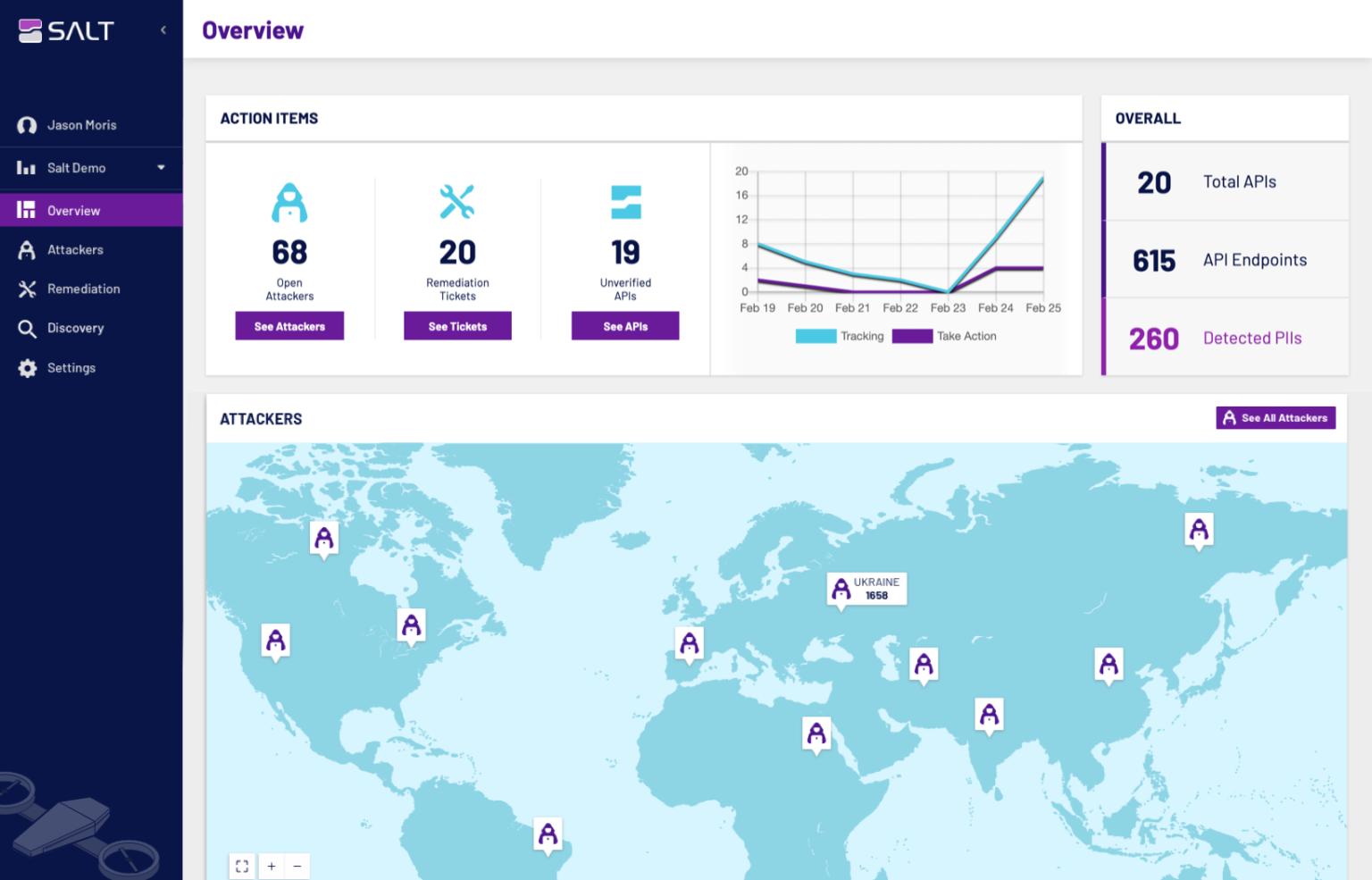
The Salt Security API Protection Platform

Additional Info
| Company | Salt Security |
| Company size | 10 - 49 employees |
| Website | https://salt.security/ |
NOMINATION HIGHLIGHTS
APIs sit at the core of today’s modern applications, connecting customers and partners to vital data and services. API-based applications are critical to revenue generation because they connect partners and customers together with critical data and services. However, according to Gartner, by 2022, API abuses will be the most frequent attack vector, resulting in data breaches for enterprise web applications and causing massive disruption to the bottom line.
Salt Security protects APIs across their full lifecycle, providing API discovery; identifying API vulnerabilities; stopping API attackers; preventing data exfiltration, account takeovers, and service disruption; and simplifying compliance. Salt leverages Big Data and AI, along with ubiquitous coverage, to gain the holistic detection needed to protect APIs across the full OWASP API Security Top 10 list of threats.
The Salt solution deploys in minutes and discovers and learns the granular behavior of a company’s APIs automatically and continuously. It requires no configuration or customization to ensure API protection and helps development teams work efficiently to meet project deadlines and business demands.
The Salt platform baselines normal behavior for each API, looks for anomalies, and correlates activity to detect attackers early in their reconnaissance efforts. As a result, security teams can block attackers manually or set the Salt Security platform to do so automatically, preventing attackers from successfully reaching their objective.
How we are different
- The Salt solution enables ubiquitous coverage and can be deployed to consolidate visibility and protection of APIs across on-premises and cloud-based deployments. It can run in traditional infrastructure or the cloud-native environments of containers and Kubernetes. Customers tap into the analysis portion of the solution via the Salt Security-hosted SaaS platform, with the option to deploy a hybrid mode that keeps customer data on-premises.
- Traditional security tools, such as Web Application Firewalls (WAFs), and management tools, such as API gateways, are based on proxy architectures. As such, their view of API activity is limited to individual transactions, meaning they cannot stitch together related events to identify an API attack. Because today’s attacks targeting APIs use a multitude of API call attempts to understand the composition and logic of targeted APIs, WAFs and API gateways miss this subtle activity that is usually performed by authenticated users. Salt leverages its big data and AI engine and ubiquitous coverage to identify the early indicators of attack, stop attackers from advancing, and turn attackers into penetration testers, providing valuable feedback used to identify and eliminate vulnerabilities. As a result, organizations are able to continuously improve their security posture.
- The Salt Security API Protection Platform has a DevOps-friendly setup, deploying in a matter of minutes and enabling protection with no need for configuration or customization. The solution is not inline, ensuring no impact or disruption to the applications being protected. It also requires no changes to application infrastructure and offers a variety of quick and easy deployment options, including API gateway integrations, sensors, containers (Docker, Kubernetes, etc.) and support through traffic mirroring.


