Photo Gallery
 |
 |
Stealthbits StealthAUDIT Management Platform

Additional Info
| Company | Stealthbits |
| Company size | 100 - 499 employees |
| Website | http://www.stealthbits.com |
NOMINATION HIGHLIGHTS
StealthAUDIT enables organizations to collect and analyze data to obtain meaningful information and take appropriate action. For example, if several files scanned contain sensitive data and are accessible to everyone in the company, StealthAUDIT lets the organization remove access for everyone except those who are in roles that require access.
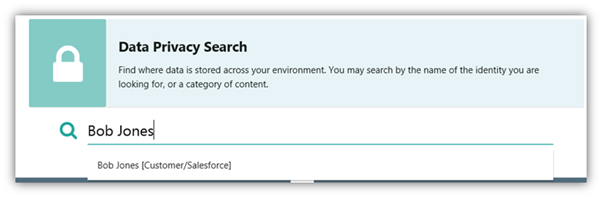
Global data privacy regulations, including CCPA/CPRA and GDPR, require organizations demonstrate compliance with data usage restrictions and adequately secure subject data from unauthorized access and data breach. One aspect of these regulations is that organizations must be able to show an individual what information they have related to them if they submit a data subject access request (DSAR). Responding to such a request can be time consuming, sometimes taking weeks. Failure to comply not only can result in a fine, but also highlights the organization’s vulnerability to potential data breaches.
StealthAUDIT’s Data Privacy Engine effectively connects identities with the location of their personally identifiable information, enabling privacy and legal professionals to easily facilitate critical data privacy workflows like Data Subject Access Requests (DSAR). The solution also lets security professionals measure and mitigate risk as well as intelligently implement Privacy by Design principles while contextually detecting and responding to data breaches.
A data breach or ransomware attack routinely requires an excessive amount of manhours and budget to address and remediate. StealthAUDIT not only drastically reduces this but also provides customers with the assurance that a potential attack will be stopped before it has a chance to wreak havoc on their system by encrypting data or something worse.
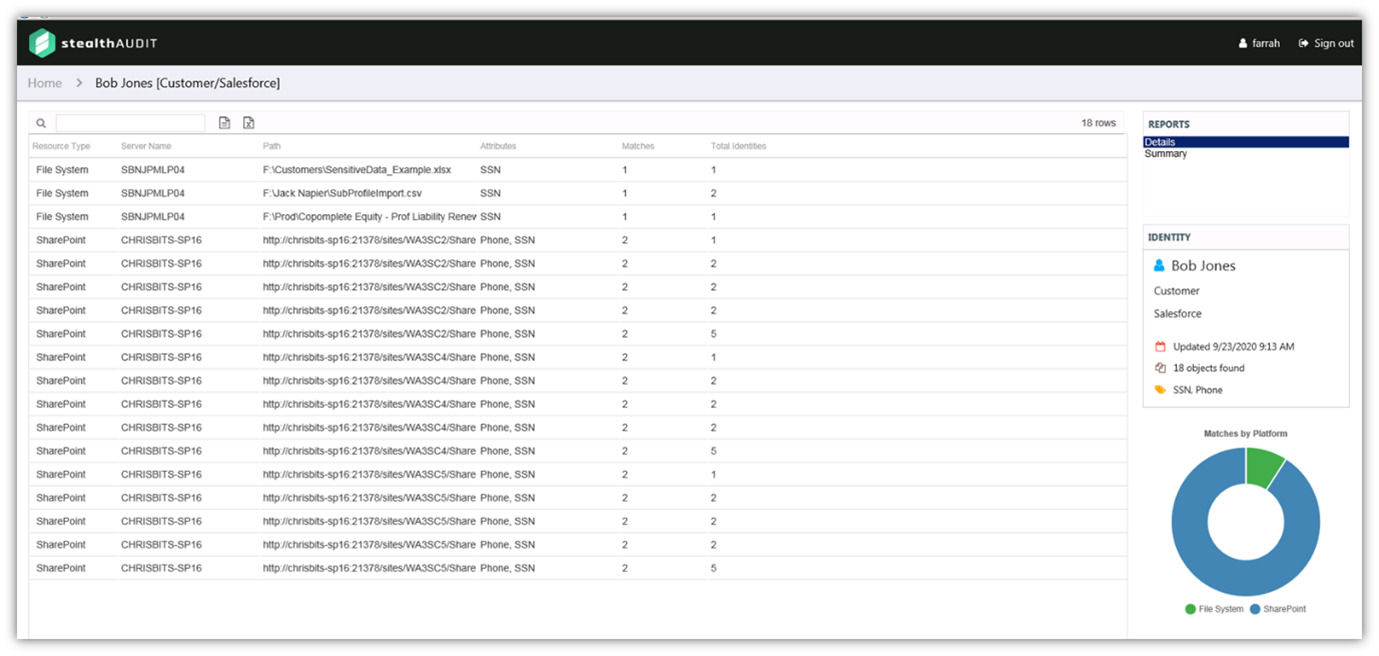
Additionally, customers appreciate that StealthAUDIT generates reports that enable understanding where data resides, what protections are applied to it and who has access or is accessing it. This provides a clear picture of an organization’s risk of data breach or attack. All of this is realized quickly, as customers repeatedly cite a short deployment time.
How we are different
StealthAUDIT differs from its competitors in several ways:
• While most organizations focus on unstructured data, StealthAUDIT can scan and protect both structured and unstructured data
• Instead of requiring customers telling the solution where to look, StealthAUDIT automates data discovery, often locating issues that customers didn’t know to look for
• StealthAUDIT can scan the contents of over 400 file types, including Optical Character Recognition (OCR), with images, which most solutions are unable to process
• StealthAUDIT pre-discovers the attributes of data subjects across all repositories (structured, unstructured, on-prem, in the cloud, etc.) and maintains an understanding of which files and tables relate to which people. This facilitates immediate fulfilment of DSARs because StealthAUDIT already knows the answer before the question is asked.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



