Photo Gallery
 |
 |
Proofpoint Browser Isolation

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
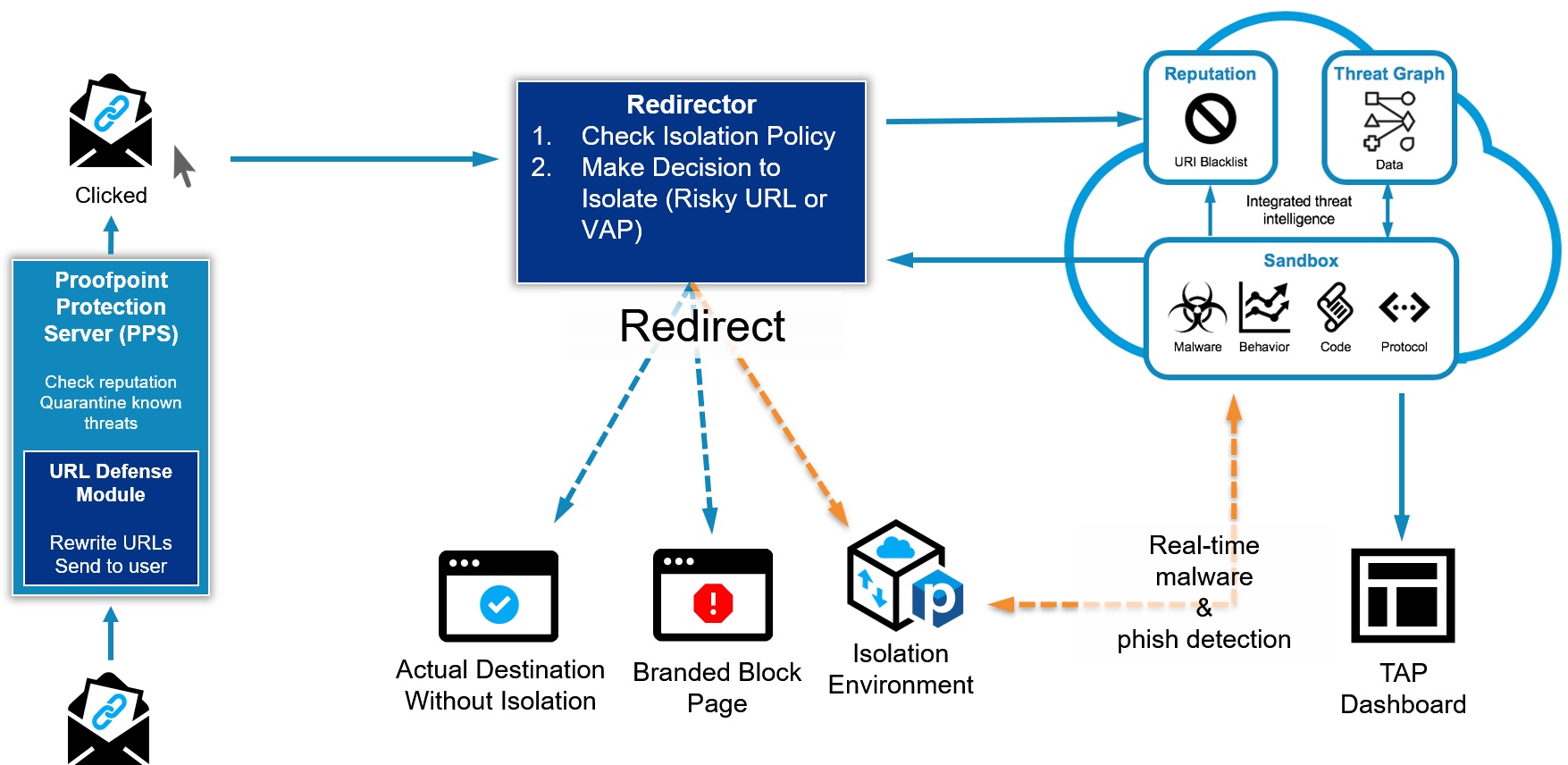
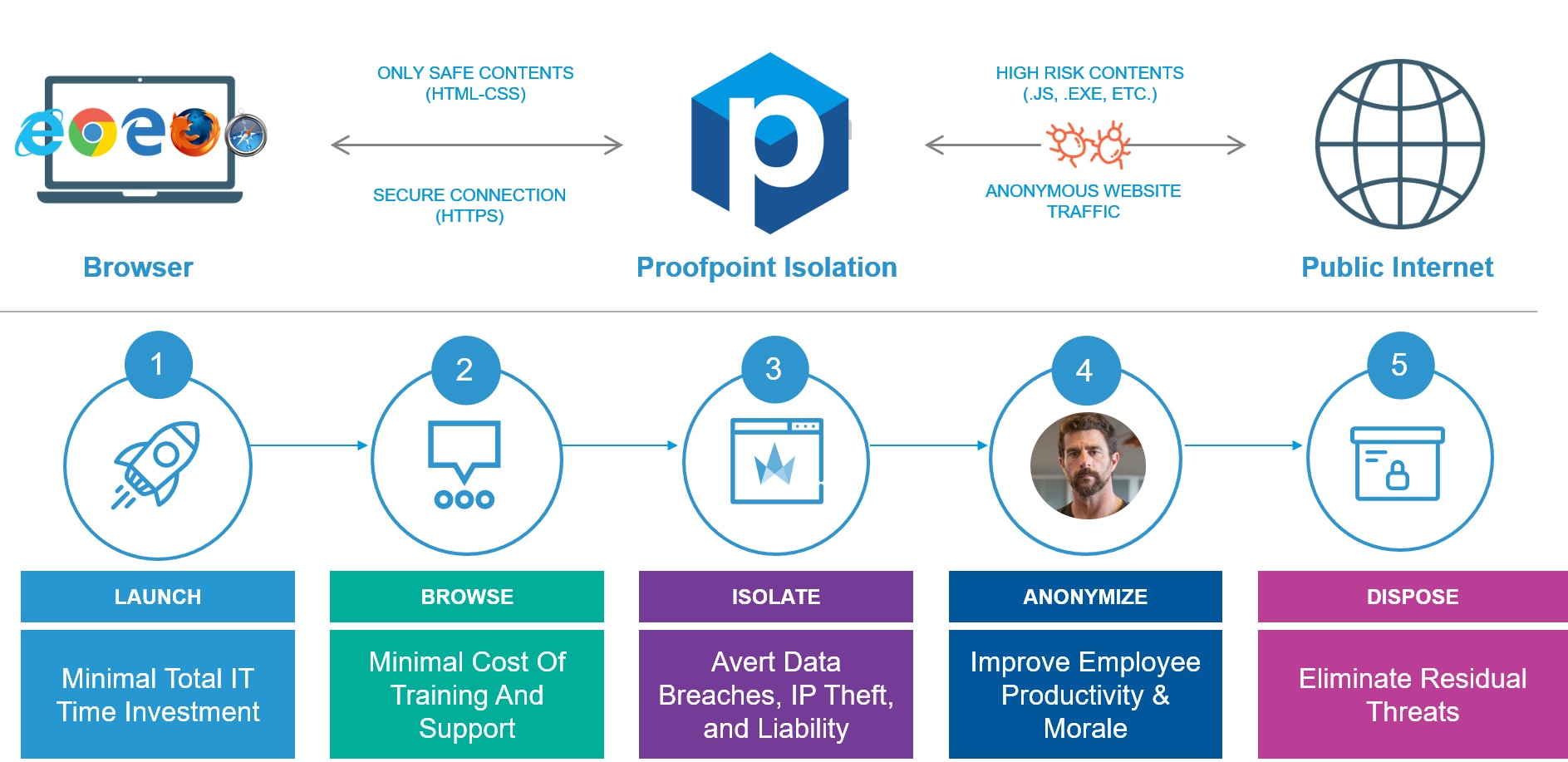
Proofpoint Browser Isolation lets your people freely access websites, cloud apps, personal webmail and corporate email without exposing your organization to malware and data loss. Browser Isolation renders browser sessions in a secure container in the cloud to keep harmful content off your network and users’ endpoints. With Browser Isolation, users may view and interact with a particular web page, however malware and other harmful content are removed from the page. Uploads, downloads and input forms are disabled to prevent data theft and loss. In addition, Proofpoint Browser Isolation’s proprietary real-time anti-phishing scan analyzes the site and automatically blocks further use of the page if it finds a threat.
Browser Isolation protects all web browsing activities for all end users, including your very attacked people (VAPs). It provides a secure and anonymous web browsing service that is simple for your IT team to deploy, manage and support.
Browser Isolation is an integral component of Proofpoint’s secure web gateway offering, Proofpoint Web Security. It isolates risky traffic to personal webmail, social media, high risk and uncategorized sites. It also applies advanced threat and data protection, by deeply analyzing traffic for zero-day phishing URLs and ransomware exploits.
When used with Proofpoint CASB, Browser Isolation secures users’ access to cloud apps and data by isolating browser sessions in a secure container, securing file uploads and downloads for risky users and behaviors. It applies cloud DLP policies to file transfers in real time, preventing theft or loss of sensitive data.
When used with Proofpoint’s Email Protection and Proofpoint Targeted Attack Protection (TAP), URLs in email are redirected to the isolation environment based on key risk factors. This allows users to click and view suspicious and uncategorized URLs safely in isolation as they are analyzed by TAP in the background.
How we are different
● Proofpoint’s Browser Isolation provides adaptive controls to help protect your very attacked people (VAPs) by isolating suspicious content in patient zero scenarios
● Browser Isolation leverages Proofpoint’s integrated threat intelligence across cloud, web, email and social media, to defend against malicious URLs and safely removes any malicious content to view and print files in a safe manner.
● Proofpoint Browser Isolation integrates seamlessly with Proofpoint Web Security and all other SWGs and is deployed 100% in the cloud without requiring any additional hardware or endpoint agents.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



