Photo Gallery
 |
 |
ManageEngine Log360

Additional Info
| Company | ManageEngine |
| Company size | 5,000 - 9,999 employees |
| Website | http://www.manageengine.com |
NOMINATION HIGHLIGHTS
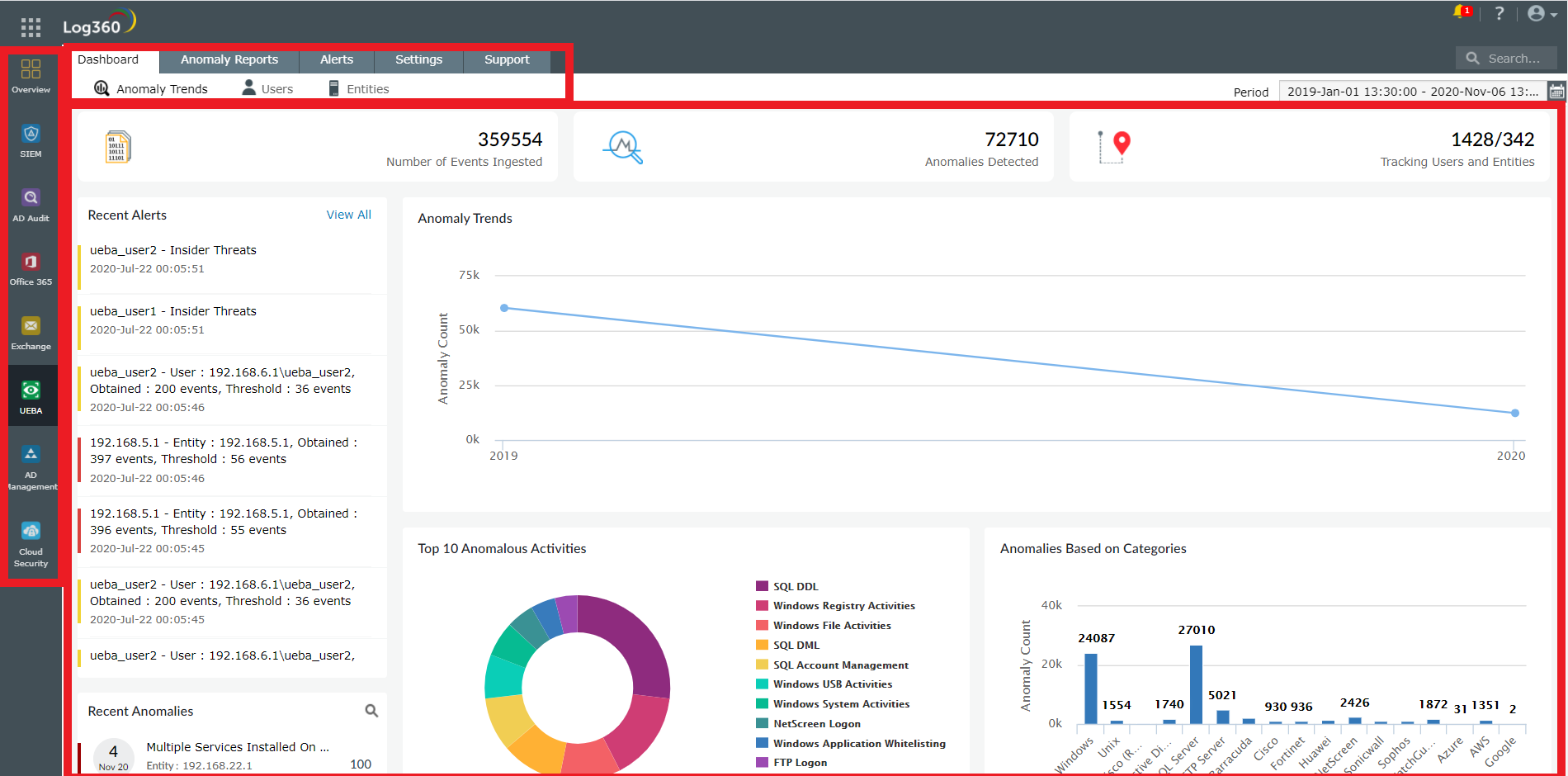
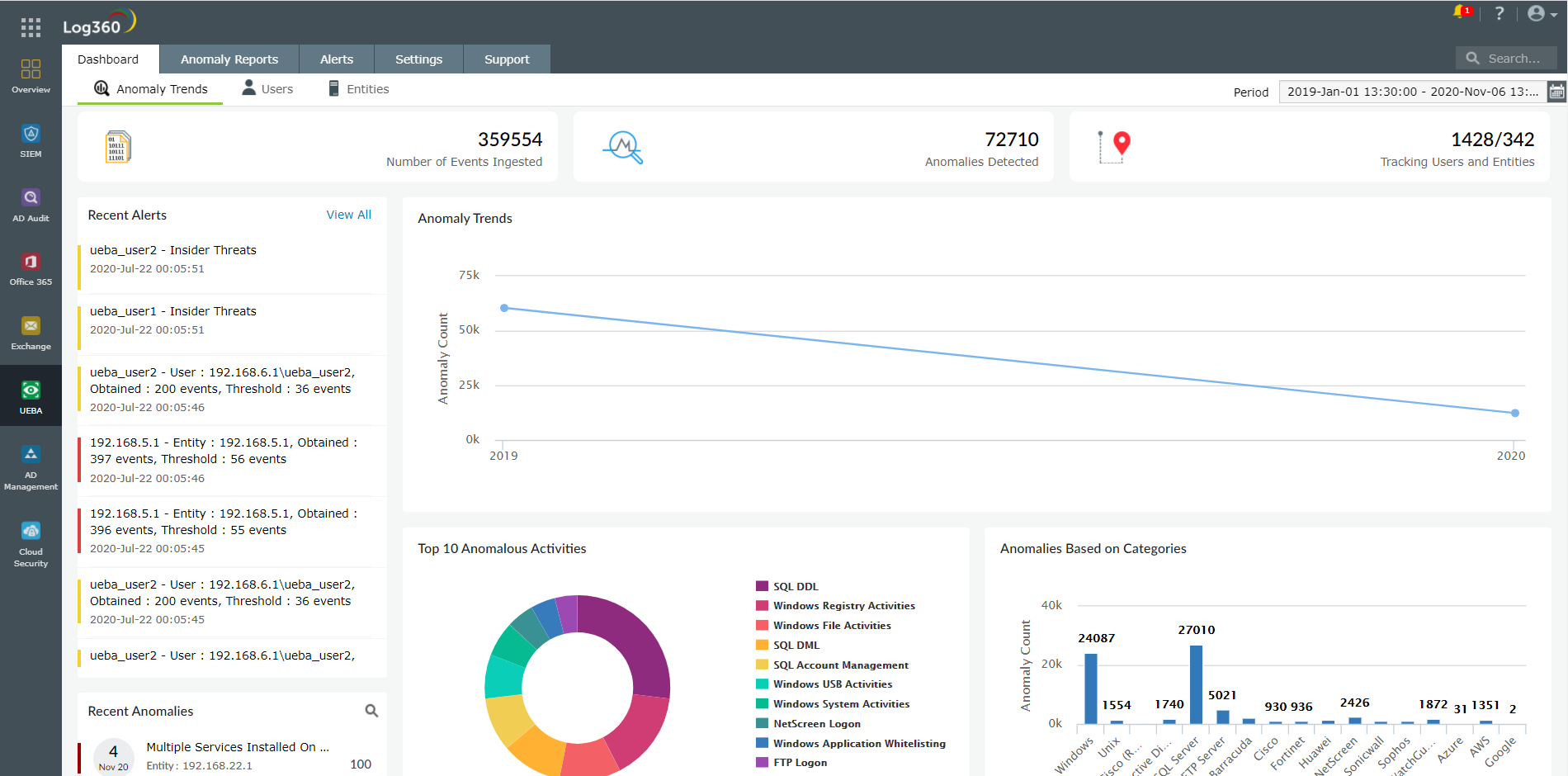
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities to detect, investigate, and respond to security threats. The UEBA capability is powered by machine learning and can detect anomalies in the behavior of users and entities in a network. There are three types of anomalies that it looks for:
a. Time anomaly: This occurs when a user performs an activity, or an entity has an activity performed on it, at a time that falls outside an expected range.
b. Count anomaly: This occurs when the number of activities performed by a user or performed on a host exceeds an expected threshold.
c. Pattern anomaly: This occurs when an unexpected sequence of events happens together.
Based on the extent of the anomalies, an overall risk score is calculated for every user and host. For users, this overall risk score is further divided into four sub-risk scores: the insider threat risk that a user poses, data exfiltration, logon anomalies, and compromised accounts. A timeline of the user’s anomalous activity can also be easily viewed to understand what took place.
Seasonality factors and dynamic peer group analysis are used for better risk scoring in Log360. While seasonality enables you to disregard expected seasonal behavior deviations while calculating risk, peer group analysis enables you to get the overall context of how a particular user’s behavior compares to other members within their peer group. You can also customize risk scoring by defining the list of anomalous activities that need to be considered, the importance of each anomalous activity, and the time decay factor (the time it takes for a risk score to gradually fall back to zero).
Log360 enables you to set up alerts based on:
1) Discrete anomalous occurrences within the network.
2) Risk thresholds defined by your organization’s risk appetite.
How we are different
1. Ability to build custom anomaly models: Log360 offers built-in anomaly models that learn the baseline of expected activity for every user and host in the network. For example, to discover time anomalies, Log360's built-in anomaly model looks for what is normal at 15-minute intervals, and to discover count anomalies, it aggregates the number of user and host activities every hour. In addition to this, Log360 allows you to train your own anomaly model using different time intervals and aggregation periods. This capability is called custom anomaly modeling. It enables you to cater specifically to your company's security situation.
2. Consideration of seasonality for better risk scoring: Log360 scores risks accurately by considering seasonality factors. Log360 will learn about any activity that happens in a network at regular intervals, whether hourly, daily, weekly, or monthly. If an activity that seems normal at first glance is in fact happening at an unusual time, Log360 recognizes it as an anomaly.
3. Peer group analysis for better risk scoring: Log360 identifies users or hosts with similar characteristics or behavioral patterns and classifies them as one peer group. You can build better security by comparing the observed behavior of a user or host to that of the relevant peer group. The user or host risk score can be impacted positively or negatively depending on the peer group.
Log360 uses behavior-related information collected over time to build peer groups. If a user exhibits a behavior for the first time, it checks whether a peer group that showcases such a behavior already exists. If it does, the user is classed into that peer group. To calculate the risk score, it then analyzes variables such as the number of members in the peer group and the frequency of occurrence of the action.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



