Photo Gallery

|


|
Hadrian

Additional Info
| Company | Hadrian |
| Company size | 50 - 99 employees |
| World Region | Europe |
| Website | https://hadrian.io |
NOMINATION HIGHLIGHTS
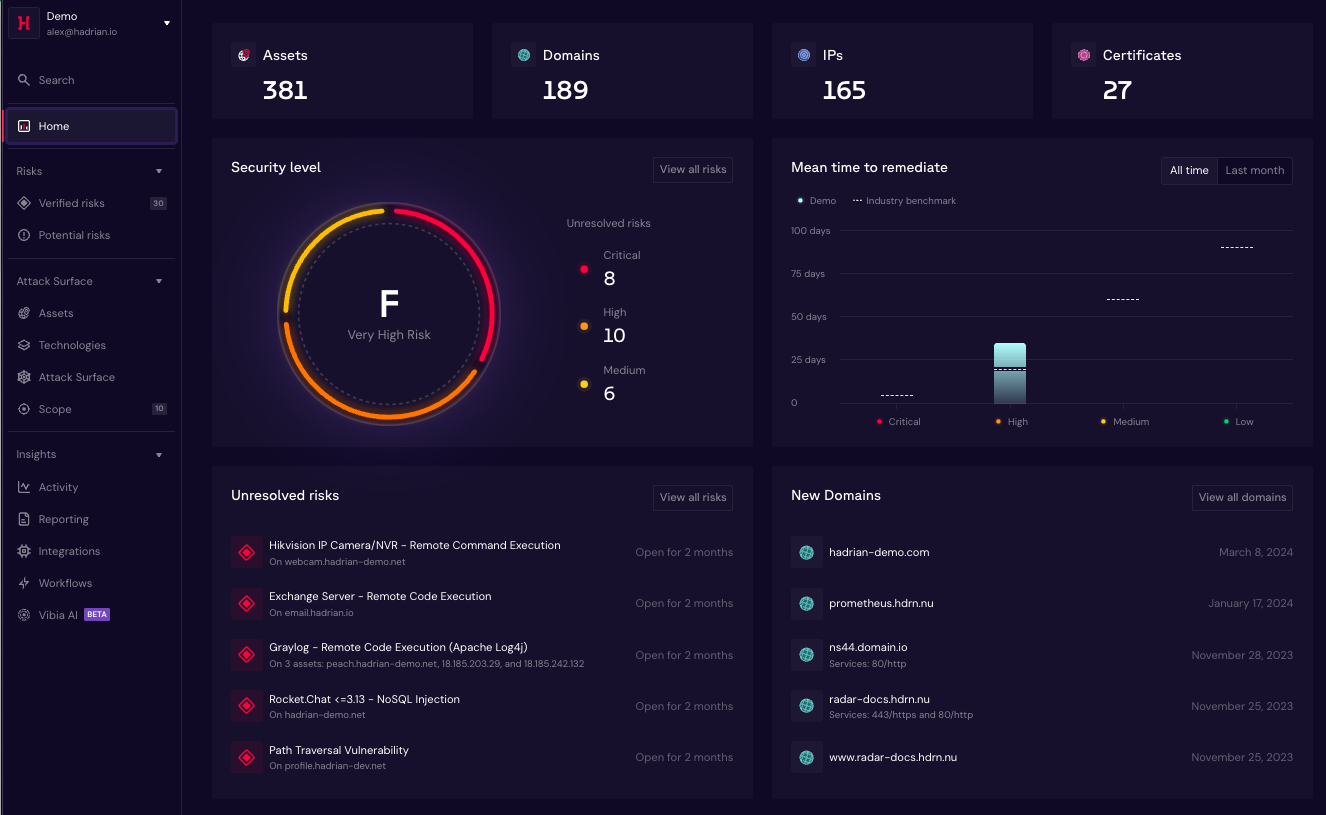
Hadrian is at the forefront of modernizing security practices through automation, enhancing speed and scalability in digital security solutions. By harnessing the insights from seasoned hackers, Hadrian enables companies to precisely identify critical risks.
The core of Hadrian’s digital security model lies in automated event-based scanning, providing a comprehensive mapping of vulnerabilities across an organization’s attack surface infrastructure. This proactive approach, developed by expert hackers, ensures accurate and continuous security validation, running tests on thousands of digital assets autonomously.
Unlike traditional security methods reliant on scheduled testing, Hadrian’s platform offers real-time insights and the hacker perspective. By seamlessly integrating attack surface discovery, automated penetration testing, and threat exposure management technologies, organizations gain unprecedented visibility into their security posture.
Hadrian’s autonomous approach not only detects threats promptly but also validates and prioritizes results, enabling organizations to swiftly fortify their security defenses. The platform’s versatility caters to various security needs and has garnered acclaim from red teams, penetration testers, SOC teams, DevSecOps practitioners, and compliance officers alike.
In the dynamic cybersecurity landscape, Hadrian serves as a trusted ally, proactively mitigating risks and fortifying organizational defenses. With Hadrian, companies can embrace automation and leverage the hacker perspective to stay ahead of emerging threats.
Key Capabilities / Features
Hadrian's product features are designed to revolutionize digital security by providing proactive, hacker-led solutions that continuously validate and fortify defenses. Here are the key features:
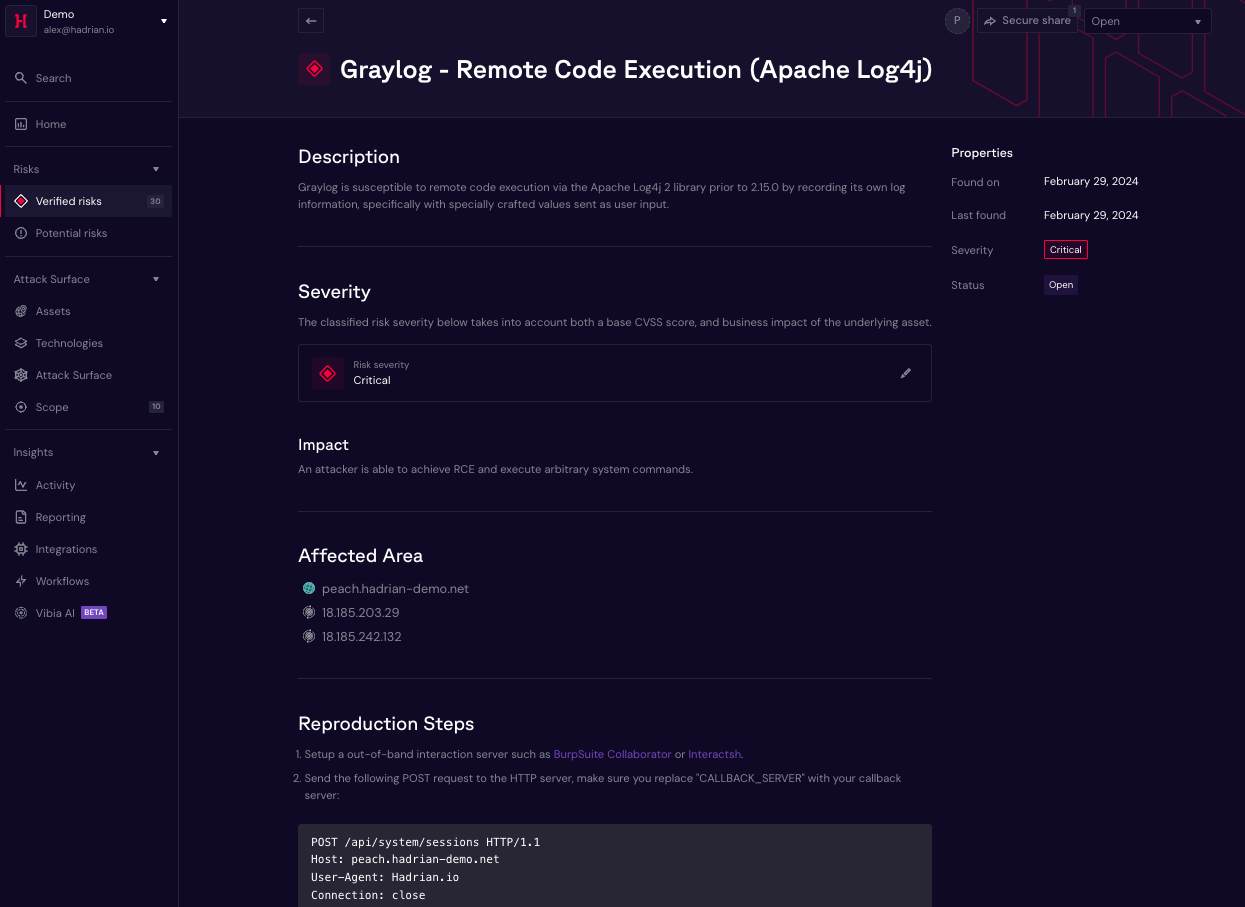
Automated Event-Based Scanning: Hadrian's approach ensures real-time identification and mapping of vulnerabilities across an organization's entire attack surface infrastructure. Unlike traditional security methods, which rely on scheduled testing, Hadrian proactively delivers accurate insights.
Hacker Perspective: Developed by an expert team of hackers, Hadrian's solution provides a unique hacker perspective, revealing potential targets and methods that could be used in real-world data breaches. This ensures a comprehensive understanding of security risks.
Continuous and Comprehensive Testing: Hadrian conducts continuous and autonomous testing on thousands of digital assets, validating risks completely autonomously. This approach ensures that organizations stay ahead of emerging threats.
Platform Integration: Hadrian's platform combines attack surface discovery, automated penetration testing, and threat exposure management technologies in a cloud-based and agentless platform. This integration ensures comprehensive security coverage across diverse environments.
Orchestrator AI: Orchestrator AI powers Hadrian's event-based threat validation engine, enabling faster risk detection and providing clear reproduction steps. Maintained by Hadrian's in-house hacker team, Orchestrator AI requires minimal configuration and offers enhanced efficiency.
Cloud and API Risk Monitoring: Hadrian provides real-time visibility of vulnerabilities and weaknesses in multiple cloud environments, aiming to be the single source of truth for customers with thousands of accounts across different providers.
Penetration Tester Emulation: Hadrian automates increasingly complex tactics, techniques, and procedures (TTPs) to provide continuous, autonomous, and comprehensive offensive security testing. This allows organizations to move away from expensive and infrequent annual penetration tests.
3rd Party Risk Detection: With the rise in complexity of software supply chains and integrated business partnerships, Hadrian offers comprehensive visibility of third-party risk. This supports various use cases, including software bill of materials creation, vendor evaluation, and assessment during M&A activities.
How we are different
Hadrian's solution is differentiated in several ways from its competitors. It is designed to be as seamless as possible so that customers can get the most value with the least effort.
Our differentiation also lies in our unique architecture that was built from the ground up to replicate real-world hacker behaviors:
Continuous and autonomous platform - The solution uses our proprietary Orchestrator AI to find and validate external-facing risks across the organization using the same techniques as a penetration tester. The zero-touch design of Orchestrator AI simulates a security expert with no configuration, no scheduling, and no manual intervention required. Hadrian’s hacker team continuously develops new penetration testing capabilities and reviews output samples of Orchestrator AI to ensure accuracy. Hadrian’s event-based architecture monitors attack surfaces around the clock for changes, investigative scans are triggered the moment a potential threat is detected.
Comprehensive capabilities - Orchestrator AI uses its knowledge of customers' environments to comprehensively test for exploitable OWASP Top Ten risks, known and zero-day vulnerabilities, and exposed and misconfigured services. The platform combines a range of next-generation technologies and security capabilities including attack surface management, continuous autonomous red teaming, risk-based vulnerability management, cyber threat intelligence, cyber threat exposure management. This holistic approach to offensive security is the most complex approach on the market.
Streamlined workflows - Hadrian’s insights are immediately actionable and quantifiably improve security posture. Verified risks have reproduction steps, severity score explanations, and step-by-step integrations that provide all of the information necessary for resolution to occur. To streamline the process tools such as Secure Share and Vibia, our generative AI, enable non-security professionals to understand the risk and how to resolve it. Built into the platform are workflow automation such as automated regression testing that occurs whenever a risk is marked as resolved to verify remediation.


