Photo Gallery
 |

 |
Fasoo Enterprise DRM

Additional Info
| Company | Fasoo |
| Company size | 100 - 499 employees |
| World Region | Asia |
| Website | https://en.fasoo.com/ |
NOMINATION HIGHLIGHTS
Fasoo Enterprise DRM (FED) is an advanced data-centric security solution designed to protect sensitive data persistently throughout the entire document lifecycle. FED ensures that files are encrypted upon creation and remain protected regardless of location – on-premises, in the cloud, or shared externally. With FED, organizations can mitigate the risks of data breaches, insider threats, and unauthorized access, ensuring that sensitive data remains secure, visible, and managed in today’s hybrid work environments.
What sets FED apart is its persistent encryption technology. By encrypting, adding metadata, and containerizing the file itself, FED provides continuous protection and control, even when files leave the organization’s perimeter. It also provides granular access control and file usage logs based on user and contextual information.
Fasoo’s data-centric approach aligns with enterprise data security and governance requirements, including GDPR, CCPA, PDPA, PCI DSS and more. It offers continuous data management that ensures full control over how information assets are accessed, shared, protected, and curated. From safeguarding intellectual property in manufacturing and financial services to ensuring regulatory compliance in healthcare and government sectors, FED has been widely adopted across various sectors and recognized as a leading solution in data-centric security.
Fasoo Enterprise DRM represents a proactive approach to data security, delivering peace of mind to organizations seeking to secure their most valuable assets – data.
Key Capabilities / Features
- Persistent File Encryption: Protect sensitive data continuously with real-time automatic encryption, ensuring data security at the file level. Comprehensive features extend to screen content, printed materials, and mobile devices, offering all-encompassing protection for diverse use cases.
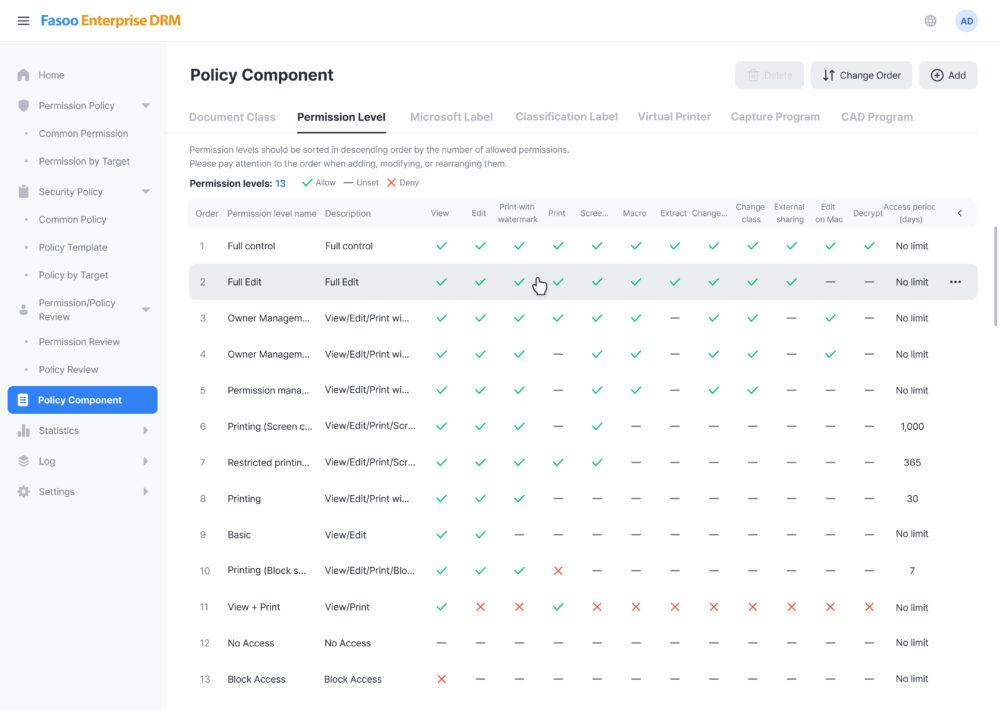
- Dynamic Access Control: Define and manage detailed permissions, including view, edit, screen capture, and print controls, for enhanced security.
- Screen Capture Prevention: Prevent unauthorized screen capture attempts in real time to protect sensitive information from being exposed.
- Copy/paste Restriction: Restrict copy and paste functionality to prevent unauthorized duplication or extraction of sensitive data, maintaining control over how information is shared or transferred.
- Dynamic Watermark: Automatically apply dynamic watermarks to documents, screens, and printouts, displaying user information such as ID, IP address, and timestamp. This deters unauthorized sharing and enhances accountability by visibly liking content to specific users.
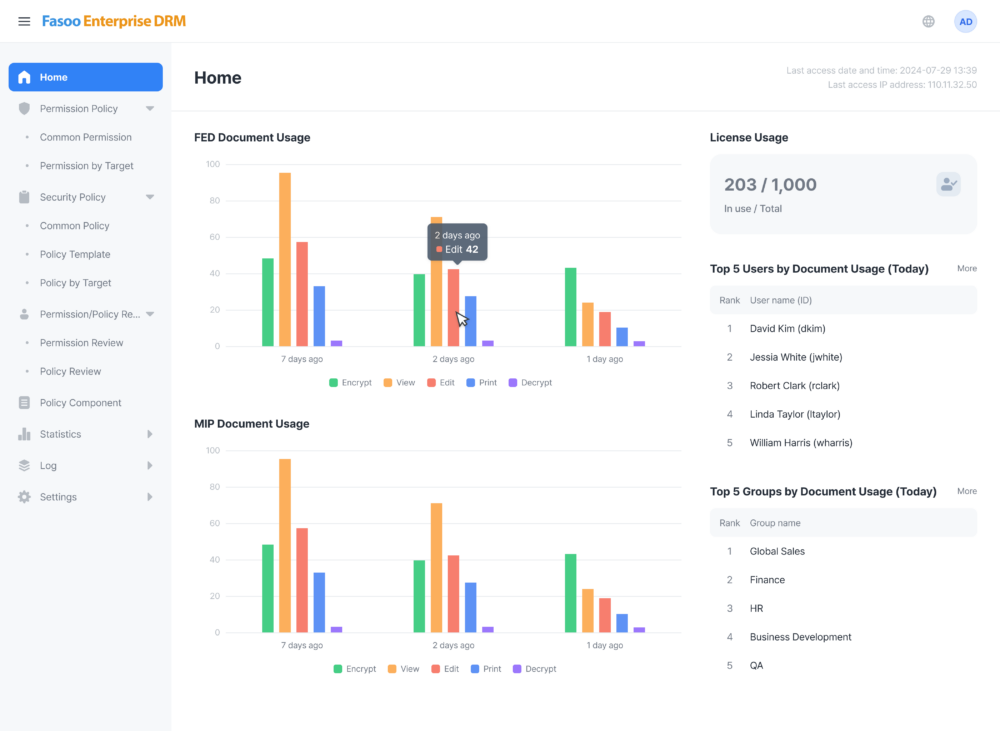
- Continuous Monitoring: Track file usage comprehensively, including derivative files, with user authentication and detailed logs. Ensure complete data visibility and control over how sensitive data is accessed and used.
- Centralized Policy Enforcement: Streamline security management by allowing centralized deployment and management of security policies.
- Integration-Friendly Architecture: Experience seamless integration with M365, enabling secure collaboration without compromising usability. Automatically convert DRM-protected local files into M365-secured cloud files. By converting local DRM files into M365-compatible formats, users can leverage DRM-protected files in AI services like Microsoft Copilot.
- Multi Platform Support: Ensure robust security across both Windows and macOS environments. Key features such as file encryption, screen capture prevention, and dynamic watermarks ensure data protection without compromise, regardless of the operating system.
How we are different
• Persistent Protection Beyond Boundaries
FED provides continuous encryption that stays with files, regardless of location, ensuring comprehensive data security compared to solutions that rely on perimeter defenses. By maintaining data encryption, access controls, and monitoring, FED eliminates security gaps across on-premises systems, cloud storage, and collaboration platforms.
• Granular Access Control for Enhanced Security
FED enables organizations to apply dynamic access controls, ensuring that only authorized users can view, edit, print, screen capture, extract or export sensitive data. With role-based permissions and dynamic watermarks, organizations can safeguard their intellectual property and sensitive information assets, even in external collaboration. This precise control mitigates insider threats and enforces the highest level of data security.
• Simplified Compliance
FED streamlines regulatory compliance with centralized policy enforcement and comprehensive audit trails. By delivering full visibility into user activity and data flows through detailed logs, FED enhances accountability and supports zero trust security frameworks, ensuring seamless adherence to compliance requirements.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



