Photo Gallery
 |
OsecT
Additional Info
| Company | NTT Communications |
| Company size | 10,000 or more employees |
| World Region | Asia |
| Website | https://www.ntt.com/en/index.html |
NOMINATION HIGHLIGHTS
OsecT is an Intrusion Detection System (IDS) for Operational Technology (OT) and Industrial Control Systems (ICS), developed by NTT Communications. It is built on network security technologies researched and developed by NTT, a leading Japanese telecommunications carrier. These technologies include traffic flow analysis techniques refined through DDoS attack countermeasures in ISP/Tier 1 large-scale networks and security risk visualization technologies for communication services that supported the Tokyo 2020 Olympic and Paralympic Games.
By analyzing communication flows within OT/ICS environments, OsecT provides functionalities such as visualizing hosts, networks, and security risks, as well as detecting threats and vulnerabilities, including cyberattacks. It supports customers in strengthening their security measures, taking preventive actions, and responding promptly to incidents to minimize the impact of cyberattacks.
Additionally, our development team is focusing on pricing, architecture design, and functionality development to make OT security solutions more accessible to small and medium-sized enterprises, which often face challenges in allocating significant funds and human resources for security measures.
Key Capabilities / Features
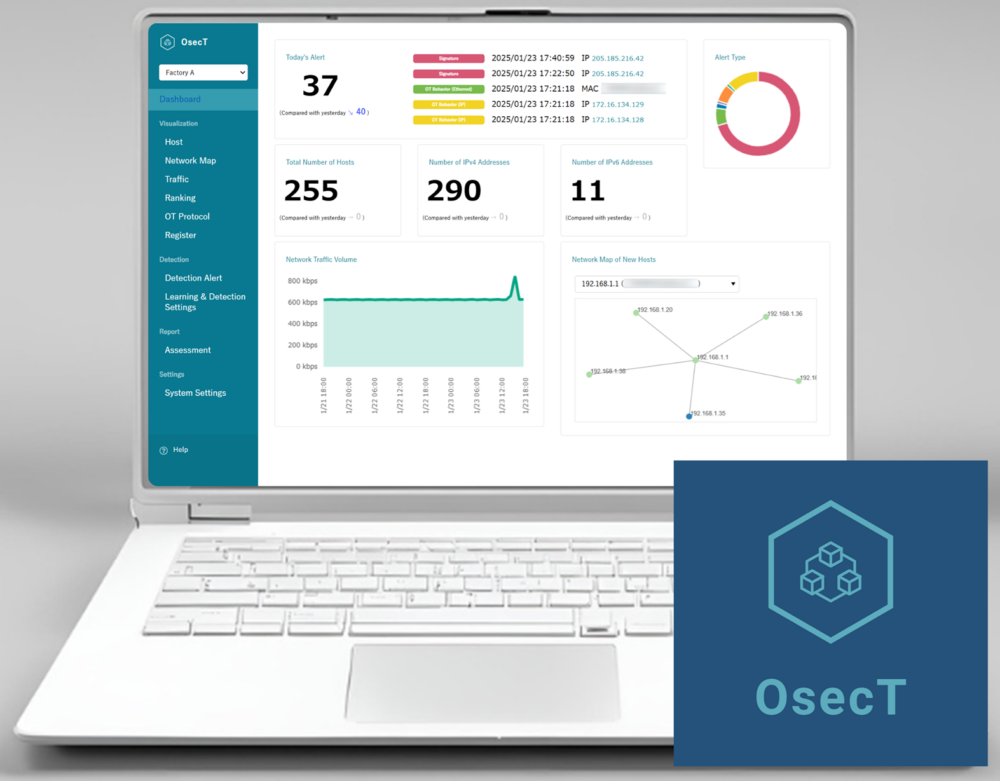
• Host/Network Visualization: The host and network information within the customer's environment is analyzed and then visualized on the Web Portal. For example, it includes host lists, network maps showing the connections between hosts, communication of OT protocols, and a visualization of the differences in network between two time periods, providing a visual understanding of the entire OT network environment. By identifying unmanaged hosts and pinpointing hosts and communications that pose security risks, it helps strengthen security measures and supports an effective response during incidents.
• Threat and Vulnerability Detection: In addition to signature-based detection, which identifies known attack patterns, anomaly-based detection is applied by learning the communication patterns within the customer’s environment and identifying deviations as anomalies. When a threat or vulnerability is detected, an alert is immediately issued. For example, detection of unauthorized hosts, detection of hosts using unsupported operating systems, detection based on the 5-tuple, detection triggered by increases or decreases in traffic volume or communication interruptions, detection of OT protocol commands, and detection based on known threats and vulnerabilities can all be utilized.
• Integration with Existing Host Registration Data: By importing register data from existing host management software into OsecT, information such as host installation locations, host administrators, and their contact information can be displayed alongside communication-based analysis on the visualization and detection alert UI. This can help streamline response efforts, such as during suspicious device detection.
• Assessment Report: With a simple click of a button on the Web Portal, a report is generated that displays a list of hosts connected to the network, traffic trends, and security risks such as hosts using unencrypted communication, external communication, and RDP communication. The report also provides recommended actions for identified risks, supporting understanding and addressing issues even without security expertise.
How we are different
• Low cost: It can be operated at an annual cost of approximately $6,800, which is less than half the price of other competing products. Therefore, it can be adopted even at a corporate scale with limited budgets for OT security. Along with the features mentioned below, our product is highly recommended for small and medium-sized enterprises that find it difficult to allocate significant budgets and personnel for OT security measures.
• Low Implementation Barrier: OsecT can be used immediately by simply connecting the device called "OsecT Sensor" to the mirror port of a network switch in customer's OT environment with a LAN cable. The sensor is equipped with our mobile closed-network SIM card. Log data transmission to OsecT SaaS environment (Web Portal) and maintenance of OsecT Sensor are carried out through the dedicated mobile network, eliminating the need to implement additional infrastructure such as VPNs for OsecT management. OsecT Web Portal is accessible over the internet, enabling remote personnel to centrally monitor sensors across multiple factories. Moreover, attack surface management is centrally handled by our company.
• Usable without Expert Support: In addition to providing all the necessary features to implement OT security measures, the WebUI is designed with a focus on daily usability through user experience testing, making it intuitive even for first-time users. Furthermore, an assessment report, which includes detected issues and recommended actions, can be automatically generated, allowing users to identify and address problems without security expertise.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



