Photo Gallery
 |
 |
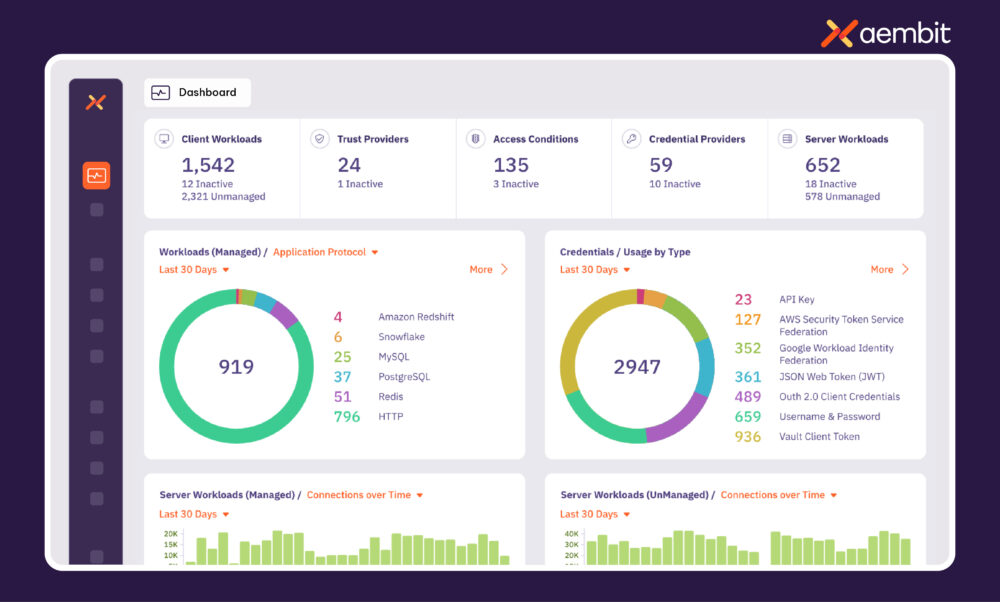
Aembit Workload IAM Platform

Additional Info
| Company | Aembit |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://aembit.io/ |
NOMINATION HIGHLIGHTS
The Aembit Workload IAM Platform secures access between software workloads – think: applications, AI agents, and service accounts – using a policy-based, identity-driven, MFA-strength, and secretless approach that spans cloud, SaaS, and data center environments. Acting like Azure AD or Okta, but for non-human identities instead of users, our platform protects the expanding attack surface created by distributed workloads. By automating the entire non-human access workflow – from discovery to enforcement and audit – from a centralized control plane, the platform delivers scalable and secure non-human IAM without reliance on static credentials.
Key Capabilities / Features
With Aembit, companies can:
✓ Secure access to sensitive resources by validating access rights in real time using the native identity of the workload and an access policy, instead of a static secret.
✓ Harden environments by accelerating the transition to both secretless access tokens and workload identity verification
✓ Reduce risk by providing Zero Trust conditional access based on posture from CrowdStrike and Wiz, and access conditions such as time, geolocation, threat data, and more.
✓ Simplify operations by providing a discovery workflow to bring new workloads under management easily.
✓ Scale and automate DevOps by minimizing credential rotation, reducing key sprawl, removing the need for secrets scanning.
✓ Remove the burden of developers needing to build authorization code through no-code auth-as-a-service.
✓ Accelerate ITDR and audit/compliance with identity-based logging.
How we are different
First Workload IAM Built for Modern Threats: Unlike traditional, human-focused IAM tools, Aembit is purpose-built to secure non-human identities (NHIs) against threats like malware, token hijacking, and credential leaks. Attackers increasingly exploit NHIs across cloud services, code repositories, and automation tools—Aembit eliminates static secrets and enforces real-time, context-aware access.
Beyond Legacy Secrets Managers & No More Static Credentials: Secrets managers only store and rotate credentials, leaving them vulnerable if stolen. Aembit removes static secrets altogether, replacing them with just-in-time, policy-driven access that verifies every request dynamically based on device posture, threat intelligence, and geolocation. Even if an attacker obtains a credential, they can’t use it without meeting security conditions.
More Than Just Visibility ... Actionable Security: Unlike the many non-human security visibility tools that identify issues but don’t fix them, Aembit proactively addresses the root causes of insecure access. Instead of just monitoring risk, Aembit prevents credential theft and misuse by enforcing dynamic, just-in-time policies that grant or deny unauthorized access in real time.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



