Photo Gallery
 |

 |
Heeler
Additional Info
| Company | Heeler Security |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://www.heeler.com |
NOMINATION HIGHLIGHTS
Heeler provides unprecedented visibility and control over applications, services, and their dependencies. Through a unique combination of code and runtime analysis, Heeler automatically discovers and models every application and service, generating a dynamic, always-up-to-date service catalog and a real-time threat model for each. What sets Heeler apart is its patent-pending technology that delivers this deep insight without requiring any disruptive changes—no agents to install, no tagging, no pipeline modifications, and no build alterations. It integrates seamlessly, allowing teams to focus on security, not configuration.
For application security teams, Heeler becomes an immediate force multiplier. It enables precise mapping of applications and services to their business value, allowing security controls and guardrails to be precisely applied where they matter most—on business-critical, production applications. This results in accurate, context-driven risk reporting that reflects the true exposure of an organization, for the first time cutting through the noise of irrelevant vulnerabilities.
By combining business context with runtime data, Heeler reduces vulnerability noise by up to 99%, slashing false positives and enabling teams to prioritize real threats. Remediation efforts are streamlined, cutting mean time to resolution (MTTR) in half, while automated guardrails help guide developers to build secure-by-design applications. This is a game-changer for teams overwhelmed by the sheer volume of code generated by AI and the 40% surge in vulnerabilities reported in 2024.
Heeler empowers security teams to shift from reactive firefighting to proactive risk management, transforming security from a bottleneck into a business enabler. In a landscape where threats evolve faster than ever, Heeler doesn’t just help teams survive—it enables them to thrive.
Key Capabilities / Features
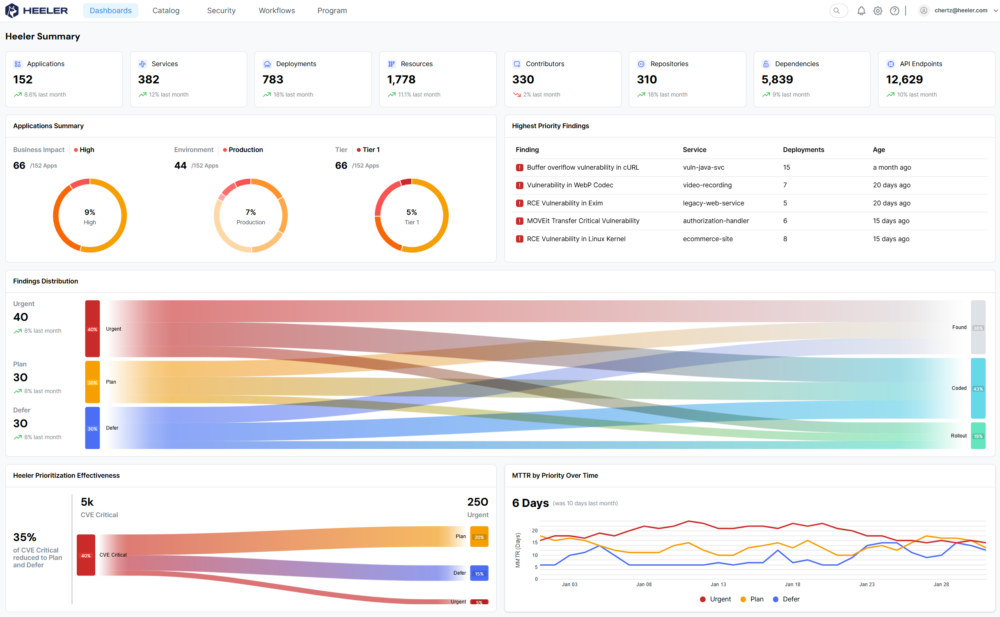
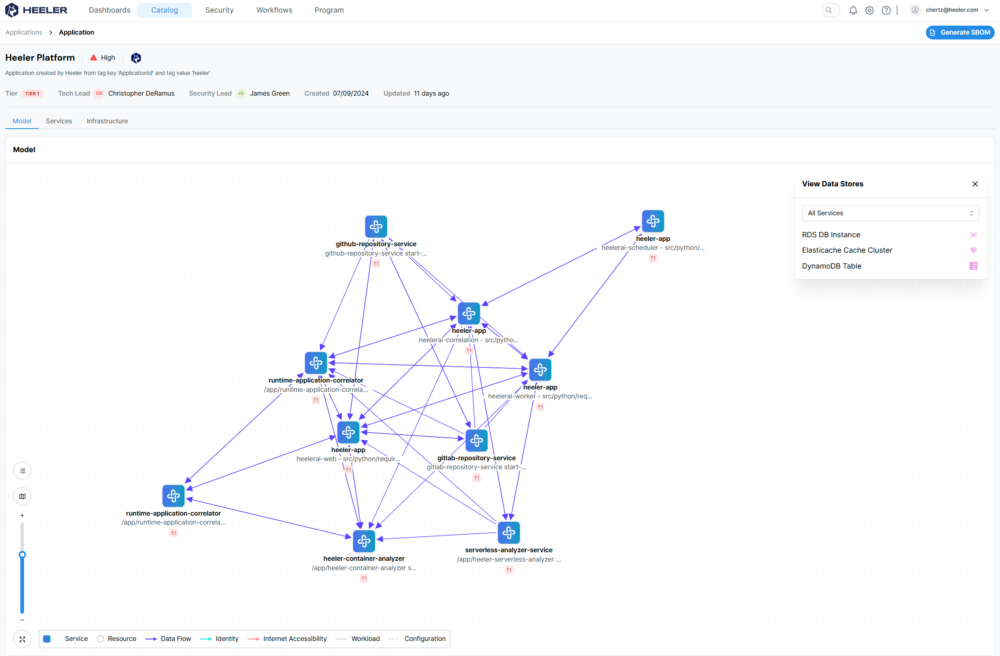
Comprehensive Observability and Service Discovery: Heeler automatically discovers and models all applications, services, and dependencies running in cloud environments in real-time, providing organizations with a complete, dynamic service catalog. This addresses the widespread lack of visibility into microservices architectures, filling gaps left by incomplete asset inventories or missing service catalogs. By mapping interdependencies across services, Heeler enables security teams to apply precise controls and respond effectively to risks, eliminating the operational friction caused by unclear ownership.
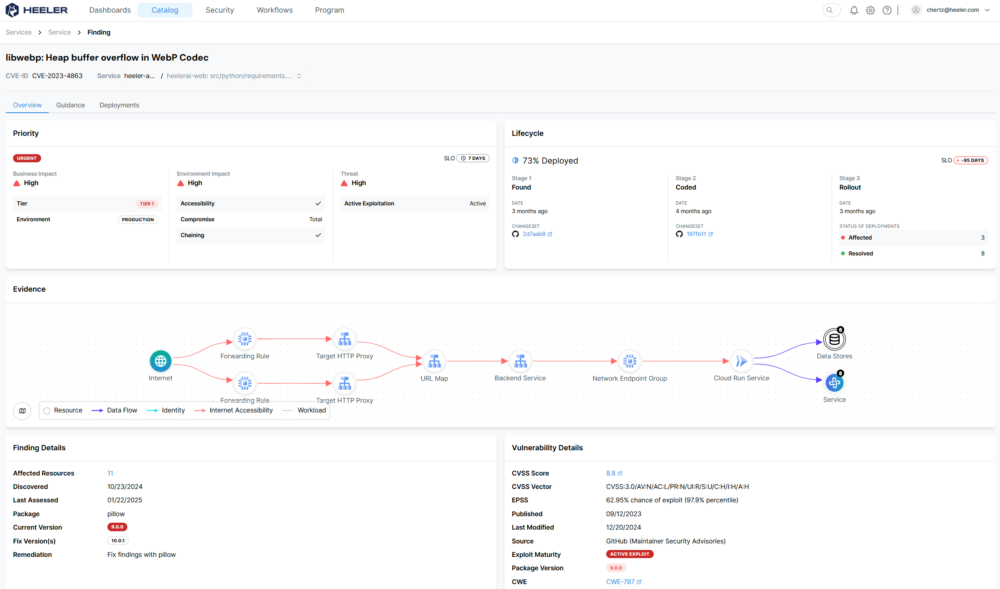
Advanced Vulnerability Management and Prioritization: Heeler tackles the overwhelming volume of vulnerabilities by prioritizing them based on reachability, business impact, and exploitability. Through deep static and runtime analysis, Heeler identifies where vulnerabilities exist in the environment, tracing them back to the exact commit, version, and deployment context. This holistic view not only reduces noise but also accelerates root cause analysis, allowing teams to focus on high-impact vulnerabilities in critical applications. By streamlining vulnerability lifecycle management—from ingestion and deduplication to prioritization and assignment—Heeler helps organizations meet compliance requirements like FedRAMP’s 30-day remediation SLA.
Ownership Attribution and Secure-by-Design Enablement: Heeler solves the persistent challenge of tracking ownership across expanding services and assets. By maintaining up-to-date service catalogs and linking vulnerabilities to specific teams and contributors, Heeler simplifies assigning responsibilities and accelerating incident response. Additionally, Heeler embeds secure-by-design principles into the development process with automated guardrails and workflows that guide developers toward secure coding practices. This proactive approach reduces downstream risks, empowering teams to deliver secure software efficiently while providing CISOs with actionable data and clear reporting to communicate application security risks and requirements to stakeholders.
How we are different
Unmatched Software Lineage and Fingerprinting: Heeler’s patent-pending technology leverages a groundbreaking algorithm to uniquely fingerprint every changeset in the source code and correlate it to deployed artifacts across VMs, containers, and serverless functions. By analyzing structural features—such as functions, methods, dependencies, and variable definitions—Heeler builds a precise map from code to runtime. This reverse-engineering capability works regardless of programming language nuances or deployment methods, offering unparalleled accuracy and visibility into how code changes impact production environments.
Real-Time, Holistic Security Correlation: Unlike traditional tools that treat code and runtime as separate entities, Heeler blends security signals from both, offering a unified view of application risk. As changes occur in the source code or cloud environment, Heeler’s real-time fingerprinting continuously updates the software lineage, providing up-to-the-minute insights. This tight integration between infrastructure and software enables security teams to identify, prioritize, and remediate vulnerabilities with precision, answering critical questions like where a service is deployed, whether security issues have been resolved, and if any deployments violate compliance standards.
Frictionless Deployment with Scalability: Heeler delivers deep application and security insights without agents, tagging, or pipeline modifications, making it easy to deploy and scale across even the largest organizations. By connecting via read-only access to source code repositories and cloud providers, Heeler operates non-intrusively, continuously detecting changes, updating fingerprints, and maintaining real-time visibility across complex cloud environments. This frictionless, scalable approach ensures organizations can maintain control over their security posture without disrupting development workflows or introducing unnecessary operational overhead.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



