Photo Gallery
 |

|
The Picus Security Validation Platform

Additional Info
| Company | Picus Security |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | picussecurity.com |
NOMINATION HIGHLIGHTS
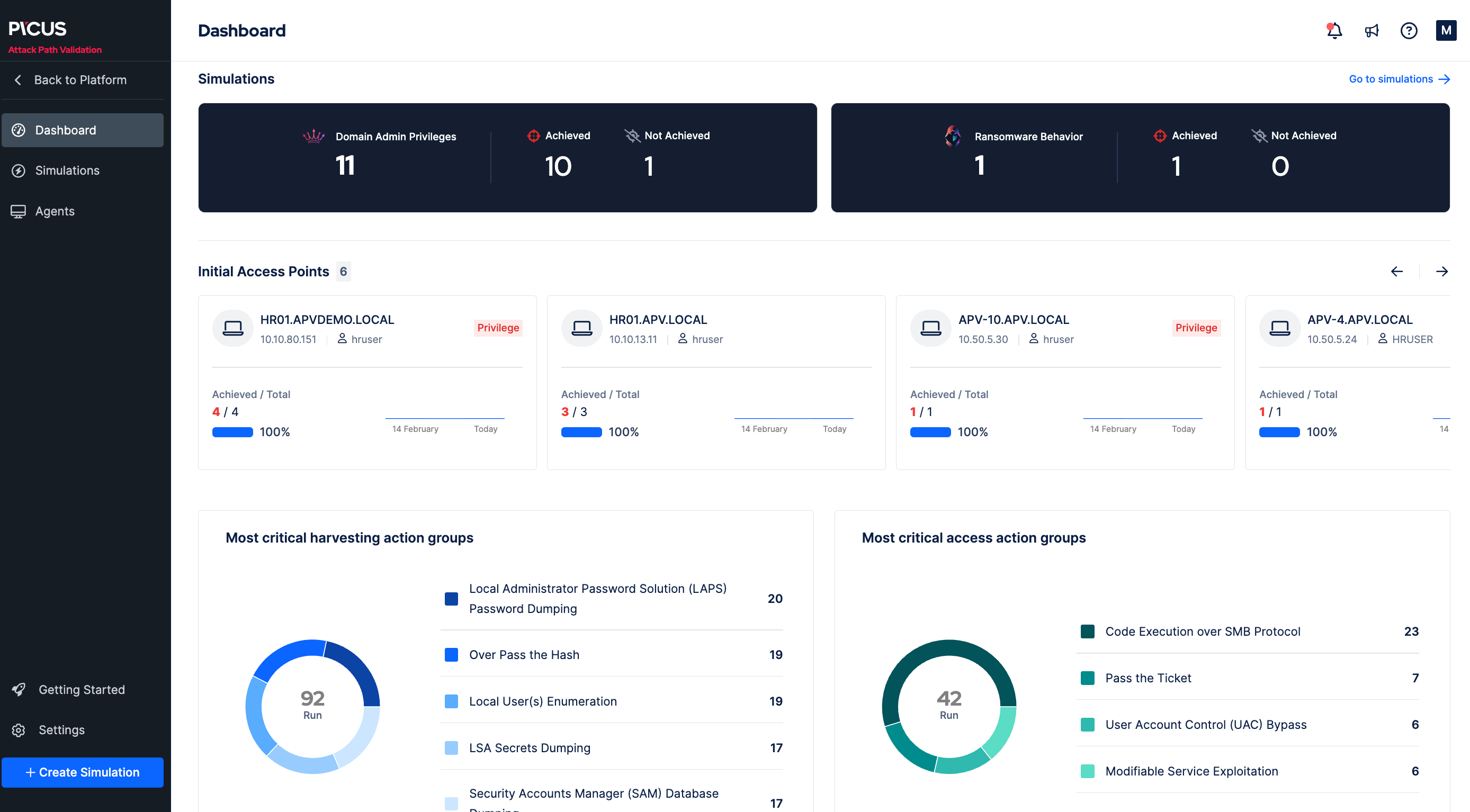
Picus Security gives organizations a clear picture of their cyber risk based on business context. It transforms security practices by correlating, prioritizing, and validating exposures across siloed findings so teams can focus on critical gaps and high-impact fixes. With Picus, security teams can quickly take action with one-click mitigations to stop more threats with less effort.
The Picus Security Validation Platform offers Breach and Attack Simulation, Automated Penetration Testing, Attack Path Mapping, Attack Surface Validation, Cloud Security Validation, and Detection Rule Validation. The platform easily reaches across on-prem environments, hybrid clouds, and endpoints coupled with Numi AI to provide exposure validation.
The Picus Security Validation Platform:
– Consistently identifies threat exposures across network, clouds, and endpoints with broad asset visibility and real-world attack simulations.
– Validates security controls, misconfigurations, and security regression to remove assumptions about your security posture.
– Performs on demand testing to identify attack paths and map them to the MITRE ATT&CK® framework to identify coverage blindspots and focus mitigation efforts.
– Scales detection engineering and red-teaming efforts with daily updates to the Picus Labs Threat Library and Threat Exposure Graph.
– Monitors security posture changes with scheduled or on-demand testing to assess infrastructure updates, network issues, and configuration drift.
– Narrows team resources to focus on risk-based prioritization; aligning organizational context, threat intelligence, asset information, vulnerabilities, and validation data.
– Enhances alert relevance by incorporating industry and geographical context, reducing noise and improving detection accuracy.
– Quantifies security risk with real-time performance metrics and AI-powered reports tailored for security and business leaders.
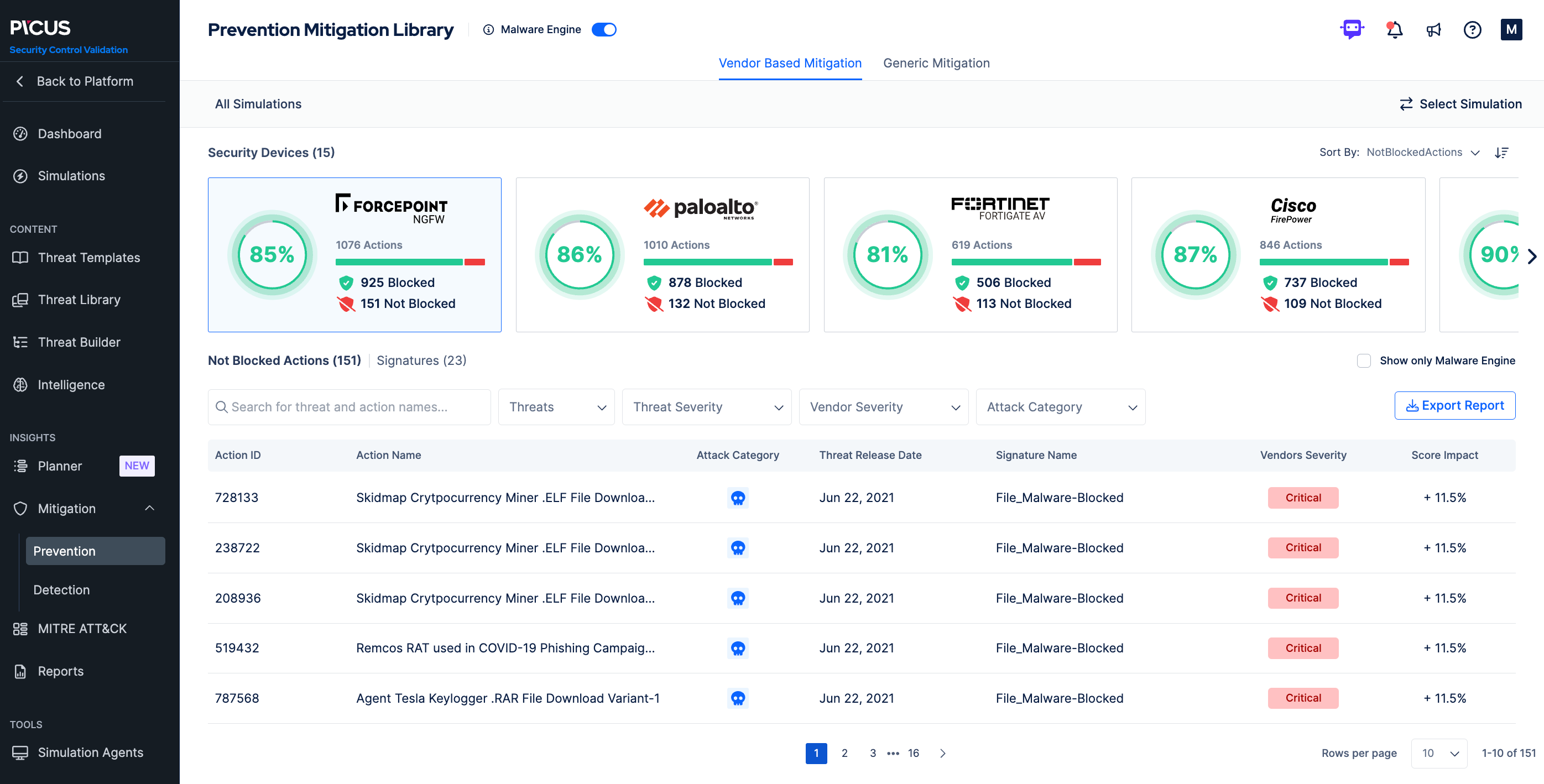
– Mitigates security gaps with actionable insights, vendor-specific prevention signatures and detection rules to fine-tune security controls.
– Reduces security fatigue and demands on red-teams by automating otherwise manual and time-consuming tasks and unlimited capabilities to test and evaluate an environment using customized simulations.
Key Capabilities / Features
Organizations struggle to understand which cybersecurity threats will have the most impact on their business operations. Security teams need the ability to fine-tune both detection and prevention by validating the effectiveness of their controls. In addition, enterprise companies are flooded with vulnerabilities and need a way to prioritize the high volume of exposures to give their Security and IT teams a clear shortlist of fixes that will move the needle and truly reduce risk. The Picus Security Validation Platform lets teams easily identify and shut down the most business-critical cyber threats to improve their overall security posture.
The Picus Security Validation Platform:
- Identifies gaps in security posture through on-demand testing of existing security infrastructure and controls, and by mapping the most likely attack paths through automated penetration testing.
- Validates the efficacy of controls through simulated attacks.
- Provides vendor-specific mitigation and actionable remediation recommendations that are highly focused, saving remediation time.
- Gives industry and geographical context, improving alert relevance and decreasing alert noise.
- Tracks security posture changes over time with scheduled or on-demand testing of infrastructure changes, network issues, and configuration drift, enabling a consistent security posture.
- Tests security controls against thousands of real-world threats, including malware, ransomware, vulnerability exploits, APTs, and more with the Picus Threat Library.
- Integrates with top SIEMs and EDRs, targeting whether alerts and vulnerabilities are detected and logged.
- Maps simulation results against the MITRE ATT&CK® Framework to quickly identify gaps and prioritize threat mitigations that pose the greatest risk to an organization.
How we are different
- Picus Security offers the only platform that delivers a validated risk level and actionable security insights by aggregating, correlating, prioritizing, and validating exposure data within a unified Exposure Graph security data fabric. This bridges previously siloed datasets stemming from vulnerabilities, threats, and assets. Picus is also an open platform, allowing enterprises to easily integrate siloed data sets, such as vulnerability or asset data, from their current security tech stack into their prioritization and validation tactics. As companies increasingly adopt the Continuous Threat Exposure Management (CTEM) framework, they look to integrate these core exposure assessment and validation capabilities within the SOC to reduce risk.
- Picus' Rapid Response Process for Emerging Threats ensures that critical threats are addressed within 24 hours and added to the Picus Threat Library. This includes attack development, mitigation content, and communication to customers and followers so they can check if the latest breach has an impact on them the same day they hear of it from industry news. This is why more than 600 organizations worldwide rely on Picus Security, including Fortune 500 companies, financial institutions, and government agencies.
- In 2024, Picus Security maintained a dynamic and continuously evolving product, delivering frequent updates across three cloud environments, on-prem, and air-gapped deployments. Over the past year, the company introduced 80+ major features and improvements, averaging 7.6 releases per day — totaling over 1,800 releases, and implemented 480 bug fixes while maintaining 99.99% platform uptime. Its commitment to continuous enhancement ensures customers receive cutting-edge security capabilities with enterprise-level reliability.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



