Photo Gallery
 |
 |
DSS Enterprise

Additional Info
| Company | Design Simulation Systems Ltd |
| Company size | 5 employees |
| Website | http://www.designsim.com.au |
NOMINATION HIGHLIGHTS
DSS Enterprise is an Authentication, Authorisation and Access (AAA) Identity-as-a-Service (IDaaS) system.
It uses a SAML-based identity authentication protocol, without SAML message complexity. The total interface requirements are two simple HTTP requests.
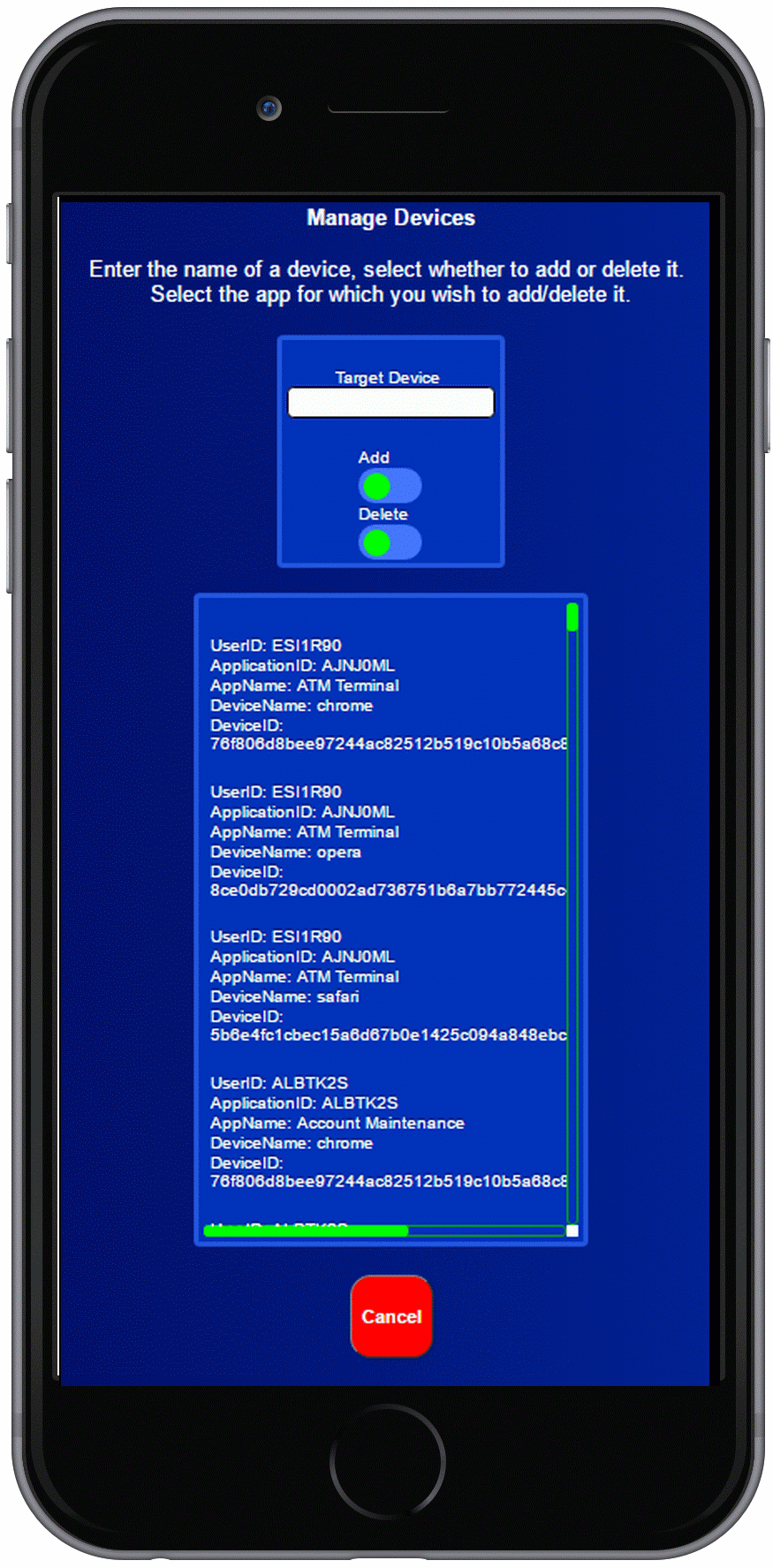
The second factor of the inherent Two Factor Authentication (2FA), is the unique signature of the user’s device.
This is derived from the device CPU, CPU clock speed, device graphics adapter and its version, device operating system and its version, and browser type and its version. Such a signature cannot be impersonated by hackers.
The slightest change in any of these parameters, such as a software, firmware or hardware upgrade, produces a different signature, and renders the original one useless.
The device signatures are derived automatically, without querying the device, installing cookies or client software on the device.
The signatures, together with verification of the source IP address, protect the Single Sign-on feature from tailgating and session hijack
Data-at-rest is protected by a novel, ultra secure encryption key management system. The key isn’t stored in any physically accessible location, and only the system knows its value. Although the administrator can change it, he never knows its value. Once changed, not even we can discover the encryption key.
Only the users themselves know and can set and change their passwords. Once set and stored encrypted, neither the administrator nor the root user can access them.
Out-of-the-box installation, simple configuration in under an hour via a smartphone. Just install four files, start your Oracle database and run the schema creation and population script.
Runs on Solaris or Linux, with script-driven user migration from an Excel csv file into an Oracle, DB2 or Informix database.
How we are different
1. The unique user device signature is derived without querying the device, installing cookies or installing client-side software.
2. The encryption keys are not stored in any physical location. Data-at-rest is protected by an encryption key management system where, even having changed the key, the administrator doesn't know its value.
3. Only the users know and can set their credentials. Once set, not even root can decipher them.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



