Photo Gallery
 |

 |
Fusion Behavioral Intelligence Platform

Additional Info
| Company | E8 Security |
| Company size | 50 employees |
| Website | http://e8security.com/ |
NOMINATION HIGHLIGHTS
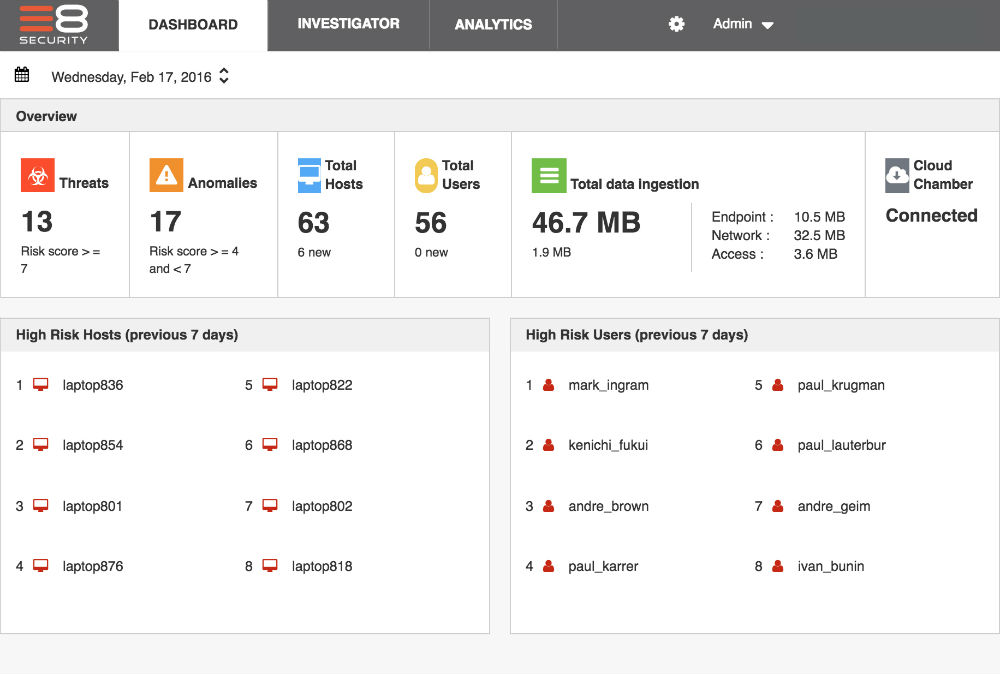
E8 Security’s Fusion Behavioral Intelligence Platform enables security analysts to detect and hunt for unknown threat indicators, and respond before a breach occurs. It’s powered by big data and machine learning to identify undetected threats inside the organization at scale as the threat landscape evolves, by recognizing the effects a threat has on surrounding resources through unusual behavior patterns.
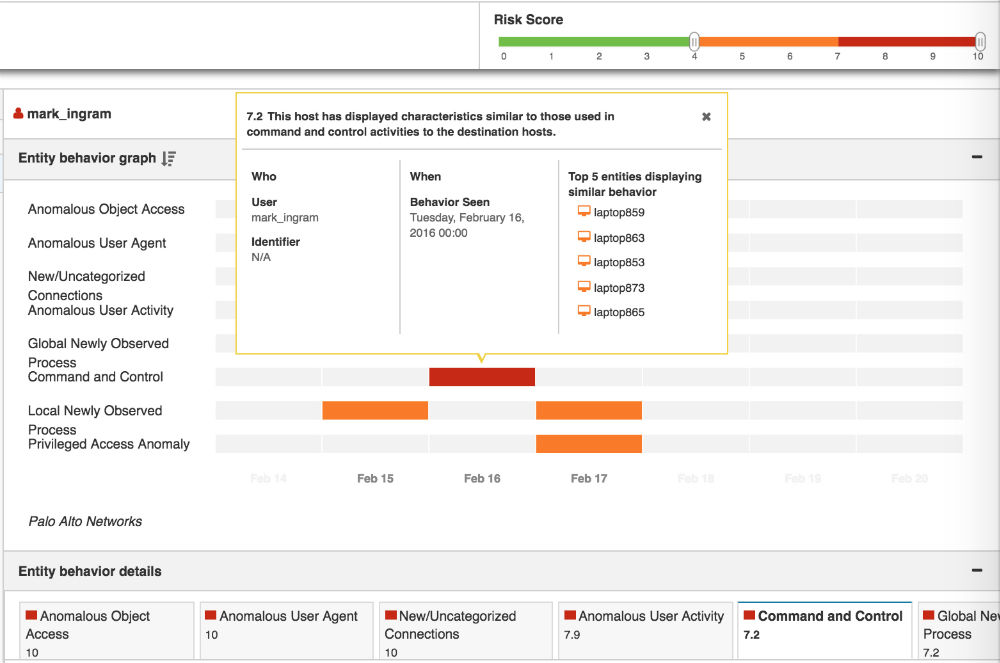
Traditional hunting approaches rely on indicators of compromise (IoCs), targeting information about the threat itself. E8’s Fusion Behavioral Intelligence Platform enables threat hunters to catch unknown threats before anything is known about the threat, itself, by detecting abnormal behaviors of internal resources – these suspicious activities are typically early warning signs that there’s some kind of threat to the business. Keying in on these behavioral signs helps threat hunters catch and eliminate threats inside the network before anything bad happens.
Entity, Signal, and Data Fusion technologies within the Fusion Behavioral Intelligence Platform provide everything threat hunters want to know, without having to ask. E8 enables security analysts to start with a single source of each entity on the network, get a unified view of what they’re up to, and easily explore the “when” and “how” behind every event across all data sources.
How we are different
- E8 Security's Fusion Behavioral Intelligence Platform makes advanced hunting easy. Threat hunters are able to see related behaviors and entities, and search and filter without having to master a query language. Because the platform connects users, devices, and IP addresses, hunters always know the "who" behind every indicator.
- The Fusion Behavioral Intelligence Platform ingests and analyzes data from endpoint, user, and network sources, providing a full-spectrum hunting ground. Threat hunters can seamlessly explore data from disparate sources, pivot on behaviors and interesting data facets, and visualize data and relationships in multiple ways.
- By detecting suspicious and anomalous behaviors, threat hunters are able to catch unknown threats inside the network earlier. E8's platform enables behavior hunting, allowing threat hunters to key in on the abnormal behaviors of internal resources that are typically the early warning signs that a threat is present.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



