Photo Gallery
 |

 |
Cognito™


Additional Info
| Company | Vectra |
| Company size | 100 - 499 employees |
| Website | http://www.vectra.ai |
NOMINATION HIGHLIGHTS
Security operations centers are understaffed and overworked. They deal with mountains of alerts, and most can review only a small fraction of the total, which often turn out to be noncritical or false positives. It’s a waste of time, and once alert fatigue sets in, repeated cries of wolf may lead to the actual wolf on premises being ignored.
Security leaders face a massive skills and human resource gap. It’s estimated that there are more than 1 million cybersecurity positioned unfilled—growing to 1.5 million by 2019 (cybersecurityventures.com/jobs).
The impact is clear: Cyber attackers operate undetected for an average of 99 days, but obtain administrator credentials in less than three days, and 53% of attacks are discovered only after notification from an external party (Mandiant M-Trends Report 2017).
The Cognito™ automated threat detection and response platform from Vectra® automates the hunt for cyber attackers and speeds-up incident response. Using artificial intelligence (AI), Cognito automates the real-time detection and response to in-progress cyberattacks hiding inside enterprise networks. Cognito is the fastest way to find and stop active threats – from cloud and data center workloads to user and internet-of-things (IoT) devices.
Gartner states: “Cognito excels at the ability to roll up numerous security events to create a single incident to investigate that describes a chain of related activities, rather than isolated alerts that an analyst then has to piece together.”
How we are different
-- Cognito speeds-up incident response. Cognito employs a unique array of AI techniques – including supervised (pre-trained), unsupervised machine learning and deep learning techniques – to detect and respond to in-progress cyberattacks in real time. Integrated intelligence enables Cognito to correlate events to reveal the larger attack narrative.
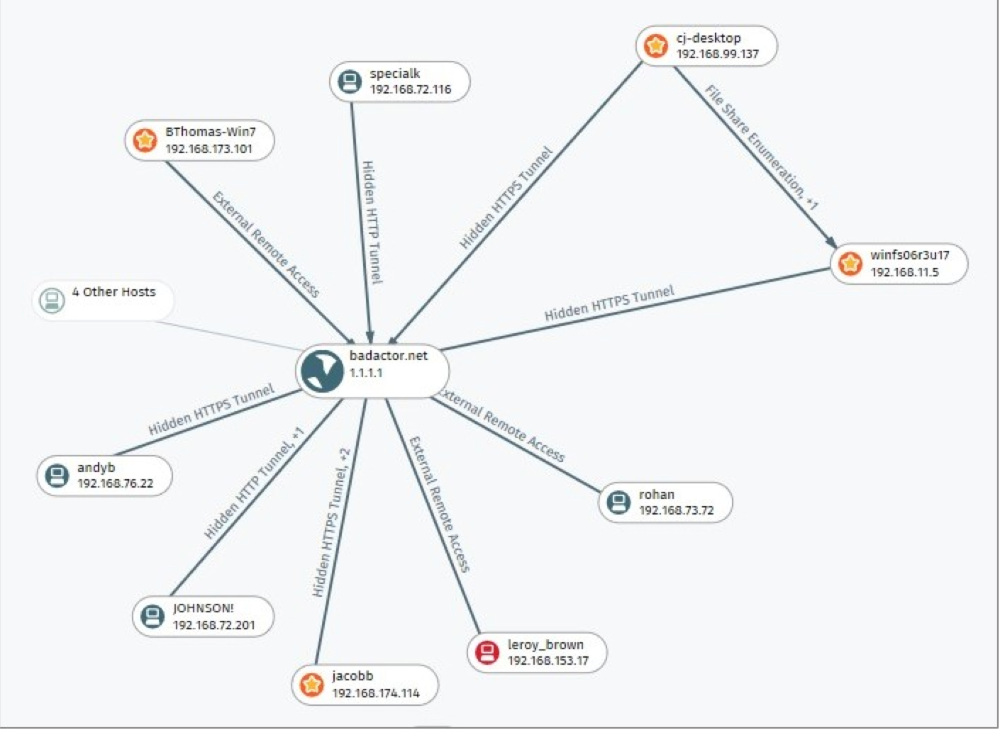
Threats are automatically triaged, scored and correlated to compromised hosts, and attack behaviors are correlated across hosts to provide the “narrative” of developing attacks. Threats are prioritized on an intuitive user interface while alerting and remediation actions are taken with other security technologies that are integrated with Cognito.
Cognito reduces customers’ security operations workload by 29X or more, according to the 2017 Vectra Attacker Behavior Industry Report. https://info.vectra.ai/hubfs/Vectra-Attacker-Behavior-Industry-Report-2017-Q1.pdf
-- Connect the dots of attacker behaviors. Highly complex, multi-stage attacks are difficult to root out. Cognito connects the dots of related attacker behavior detections across all hosts in real time, relieving the burden on security analysts to find these relationships manually. A synthesized view of an attack campaign allows an entire attack to be stopped at the earliest signs of detection.
Cognito integrates threat intelligence and indicators-of-compromise (IoC) feeds. Threat intel detections capture metadata from data packets to protect personal privacy and are correlated with Cognito attacker behavior detection algorithms to amplify the attacker signal and provide the most complete context.
-- Stop in-progress attacks. Tight integration with leading security tools allows customers to build well-coordinated security infrastructures that automatically map active attacks to infected hosts, rank the certainty and severity of threats, and prioritize the threats that pose the highest risk. Cognito works with leading endpoint security (e.g., Carbon Black, Crowdstrike, McAfee, Symantec), network access control (e.g., Cisco ISE), firewall (e.g., Cisco ASA, Juniper, Palo Alto), SIEM (e.g., ArcSight, QRadar, Splunk), security orchestration (e.g., Demisto, Phantom) and network visibility (e.g., Gigamon, Ixia) products. https://vectra.ai/partners-technology

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



