Photo Gallery
 |

 |
A security tool tailored to SMBs' needs

Additional Info
| Company | Fudo Security Inc. |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://fudosecurity.com/ |
NOMINATION HIGHLIGHTS
Fudo One is a software solution for SMBs and StartUps. It’s a free cybersec solution for 3 users and 3 servers.
Fudo One is the perfect tool for managing access to your DevOps, Admins, Privileged Employees, Freelancers, Subcontractors, Vendors, and all kinds of third-parties. The Zero-Trust approach is the perfect alternative to the VPN access method. Users have access to specific applications and accounts only when needed and for a specific reason. All authorized users’ activity is constantly monitored and recorded.
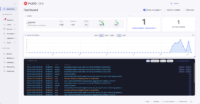
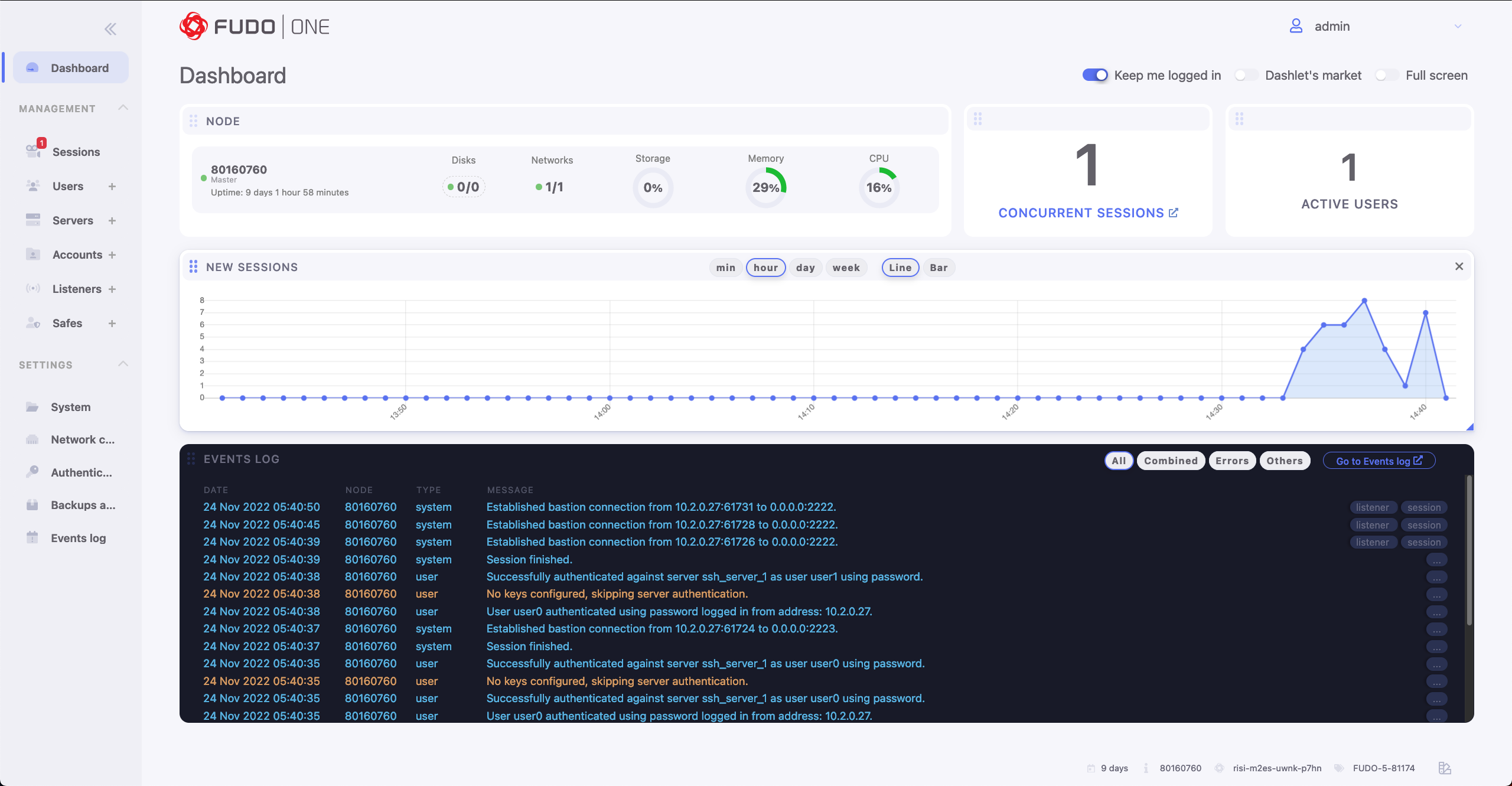
Fudo One also allows you to perform a variety of actions on both recorded and live remote access sessions. Key features include the ability to watch a session live, share it with others, and terminate it with the possibility of blocking the user when dangerous behavior is detected.
The Fudo One Session Management feature will help you audit users’ activities and prevent unintentional and unnecessary data access. You can closely monitor all privileged users with an effortless tool that does not require increasing IT staff. And that’s not all. The Fudo One Just-In-Time feature enables you to grant access to company resources upon request only or be set up in advance. This will give you full control over all remote access sessions.
Super quick instalation: through a single click, users can download software and start using their own Fudo One immediately.
How we are different
Fudo One is a software solution for SMBs and StartUps.
Agentless Convenient Access with Fudo One, users can get access to their accounts quickly and easily. Users will not have to change their habits and can continue to use native clients. They can also connect through the Fudo Web Client which only needs a web browser for access.
Session Monitoring & Recording: now the administrators can control sessions with abilities to join, share, pause, or terminate any potentially suspicious session in real-time.
Share your resources over RDP, VNC, SSH protocols and record everything.
Super easy multi-factor authentication
Users can configure their own second-factor authentication methods by themselves. With the User Access Gateway, it is simple to set up mobile applications with OATH QR codes.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



