Photo Gallery
 |
|
|
Absolute Platform, featuring Reach


Additional Info
| Company | Absolute |
| Company size | 100 - 499 employees |
| Website | http://www.absolute.com |
NOMINATION HIGHLIGHTS
There’s nothing more concerning to CISOs than millions of employees taking company financial data, IP, personal records and more around the globe, leaving CISOs struggling to protect millions of scattered endpoints when controls are compromised and devices are off the network. Since CISOs can’t protect what they can’t see, they require an always-connected endpoint security solution to help already-stretched staff efficiently secure every endpoint in their fleet.
According to a Ponemon Institute report, 63 percent of enterprises cannot monitor at-risk, dark
endpoints, making them vulnerable to a costly data breach. To target this systemic illness crippling
enterprise security today, Absolute launched the Absolute platform in August 2017. It gives IT
security teams the flexibility to adopt security solutions that address their specific needs, including
endpoint visibility, control and resilience.
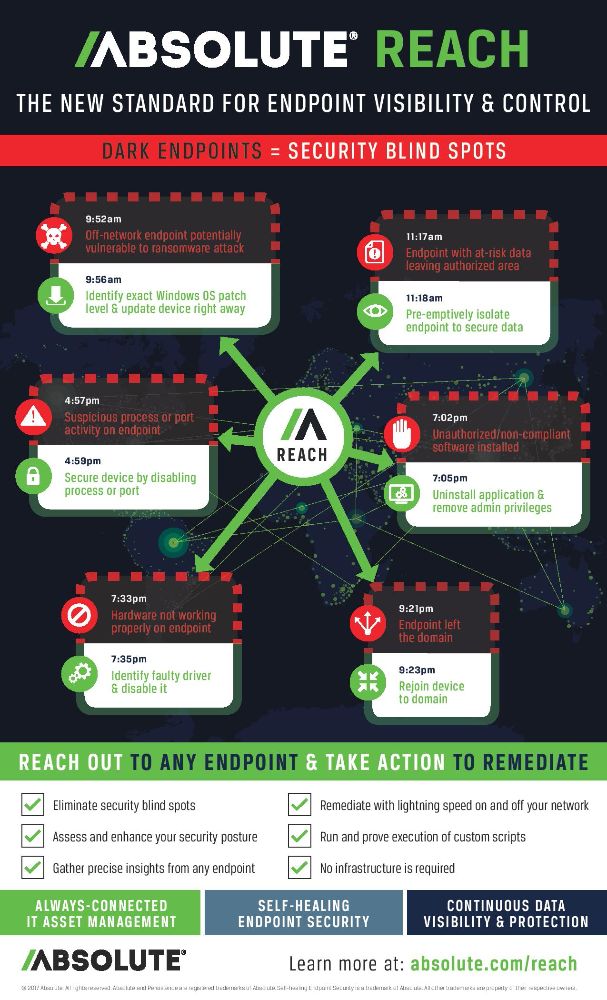
The layered platform’s most notable feature is Absolute Reach, an innovative new capability that gives
IT security professionals the power to leverage always-on visibility and control over endpoints and data—on and off the network. Absolute customers can now validate the scripts they executed to prove compliance. This allows asset managers and security professionals to:
– Evaluate and harden security posture: Leverage always-on visibility and control over endpoints and data to evaluate exposure risk and prove compliance.
– Eliminate endpoint blind spots: Remediate known vulnerabilities in near real-time to reduce risk through maintenance and compliance validation.
– Customize queries and remediation actions: Create and execute fast asset management queries to speed inventorying and audits. Execute custom remediation actions to proactively address vulnerabilities and threats.
– Reduce vulnerabilities across all endpoints: Assess endpoint agent compliance, understand current patch and version profiles, and take remedial actions across an entire endpoint population with just a few clicks.
How we are different
- Absolute Reach delivers confirmation of delivery and execution of any deployed script, regardless of device, task or location. That, in turn, proves compliance. No other company can offer this guarantee.
- Absolute Reach gives IT and security teams the power to see every endpoint on and off the corporate network. Other solutions limit IT teams to what’s currently on the corporate network, which doesn’t work in today’s mobile world.
- Absolute Reach leverages Absolute's patented Persistence technology, which is embedded in the firmware of more than one billion popular PCs and mobile devices worldwide. Application Persistence provides an extra layer of resilience for business-critical applications with a zero-touch, automatic re-installation if an application is removed or disabled.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



