Advanced Persistent Threat (APT) Hunt Service
Recognized in the Category:
Photo Gallery
 |
Advanced Persistent Threat (APT) Hunt Service

Additional Info
| Company | Camelot Secure |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://camelotsecure.com/ |
NOMINATION HIGHLIGHTS
Camelot Secure, a trailblazing cybersecurity firm, has unveiled its Advanced Persistent Threat (APT) Hunt Service, setting a new benchmark in cybersecurity defense. This innovative service is engineered to shield organizations from increasingly complex and elusive threats that bypass conventional security measures and remain undetected for prolonged periods. In an era where, according to IBM, it takes organizations an average of 207 days to discover a breach and an additional 70 days to contain it effectively, Camelot’s APT Hunting service drastically shortens the discovery timeframe with its unique offensive approach. Utilizing AI and Machine Learning technologies, mapped with the MITRE ATT&CK™ framework and supported by real-time threat intelligence data feeds, this service unifies multiple data sources, automates the baselining process across protected cyberspaces, and persistently tests hypotheses against this baseline to ensure early detection and prioritization of threats for investigation.
Camelot Secure’s commitment to pioneering new cybersecurity methods is evident in its APT Hunt Service. It offers organizations a means to proactively identify potential threats through advanced technological innovations before they can inflict harm. This approach represents a significant departure from traditional cybersecurity practices, shifting towards a more offensive, predictive strategy in combating cyber threats. Camelot’s sophisticated APT Hunt tools and offensive attack surface monitoring technologies underscore its revolutionary stance in the cybersecurity industry. It aims to empower businesses to proactively and predictively safeguard their digital assets against sophisticated and targeted attacks that have historically evaded detection. Through this comprehensive cybersecurity protection, Camelot Secure redefines the landscape of digital security and ensures that organizations are equipped with the necessary tools and insights to maintain robust defense mechanisms in the face of evolving cyber threats.
Key Capabilities / Features
Camelot’s APT Hunt Services employ a proactive cybersecurity strategy to effectively counter APTs. This approach combines attack surface management, network and log analysis, and integrated threat intelligence feeds with sophisticated behavioral
analysis. The synergy of human expertise and cutting-edge technology, including AI, ML, and automation, enables efficient, proactive threat detection and resolution.
APTs are stealthy attacks by skilled adversaries, often remaining undetected in a network for extended periods intending to steal data or secrets. Companies need this
proactive approach to neutralize threats before they cause significant damage.
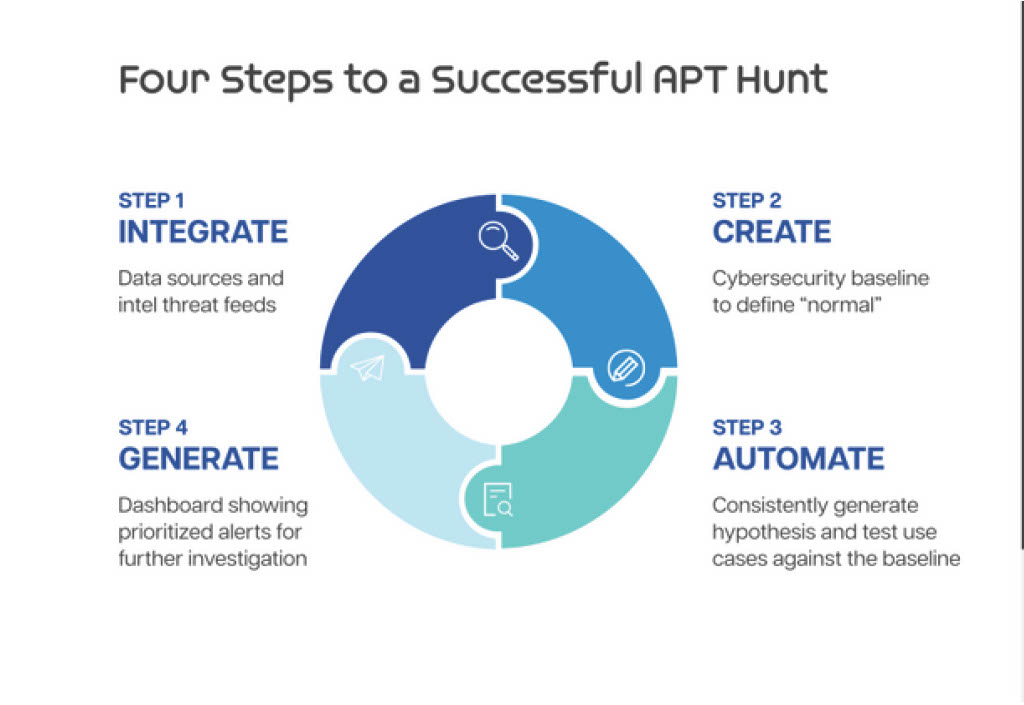
Camelot's four steps to a successful APT Hunt include:
1) INTEGRATE - Data sources and intel thread feeds.
2) CREATE - Cybersecurity baseline to define normal.
3) AUTOMATE - Consistently generate hypothesis and test use against the baseline.
4) GENERATE - Dashboard showing prioritized alerts for further investigation.
How we are different
* Innovative Offensive Approach: Camelot's APT Hunt Service revolutionizes cybersecurity by proactively identifying and neutralizing advanced threats before they can cause damage, leveraging AI/ML technologies and the MITRE ATT&CK™ framework for a cutting-edge offensive strategy.
* Advanced Integration and Automation: Camelot significantly shortens threat discovery times by integrating multiple data sources and employing automation to baseline cyber landscapes, setting a new industry standard for rapid response and prevention.
* Comprehensive Threat Management: Camelot’s unique methodology enhances detection capabilities and prioritizes threats more effectively, ensuring organizations can focus on the most critical vulnerabilities. It embodies a shift towards a predictive, proactive cybersecurity paradigm.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



