Photo Gallery

|


|
Aembit Workload IAM Platform

Additional Info
| Company | Aembit |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://aembit.io |
NOMINATION HIGHLIGHTS
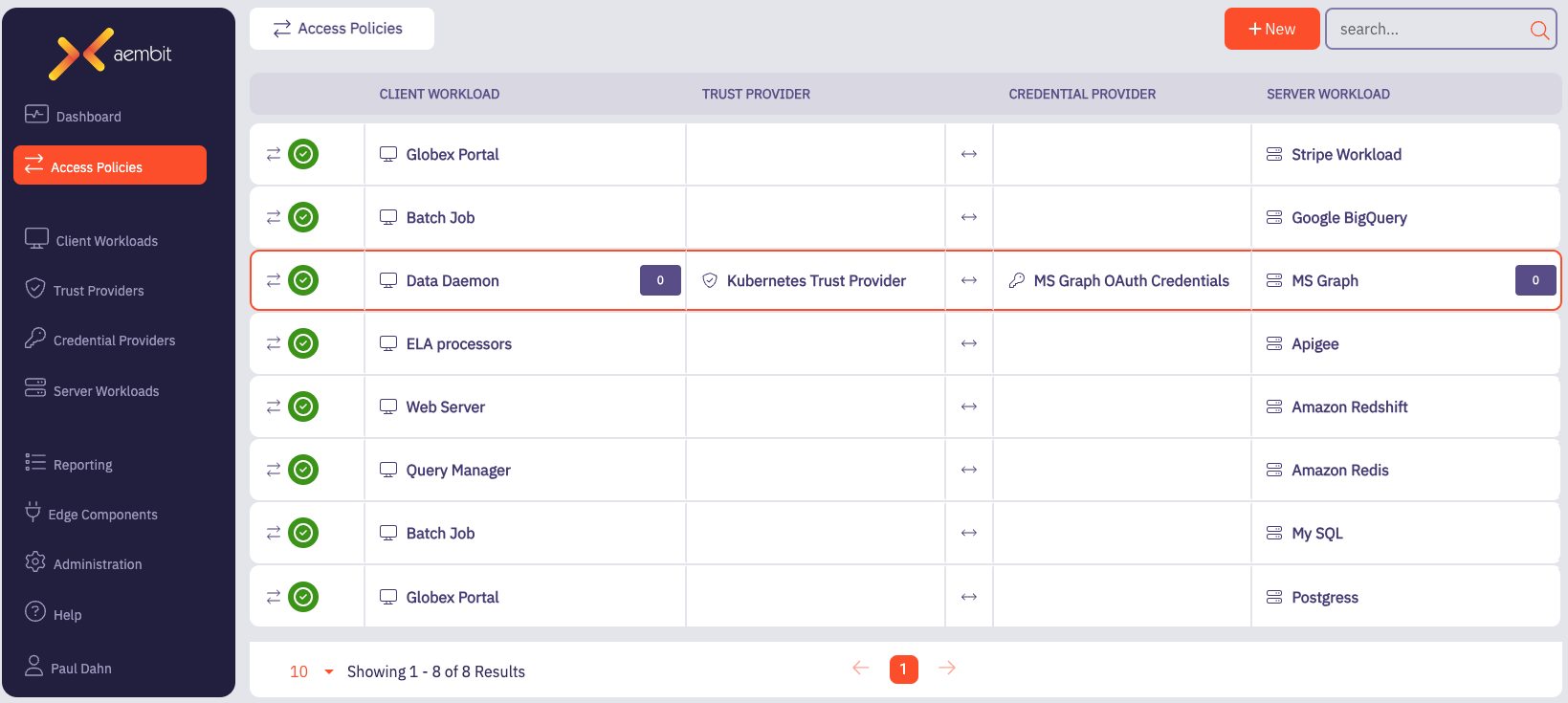
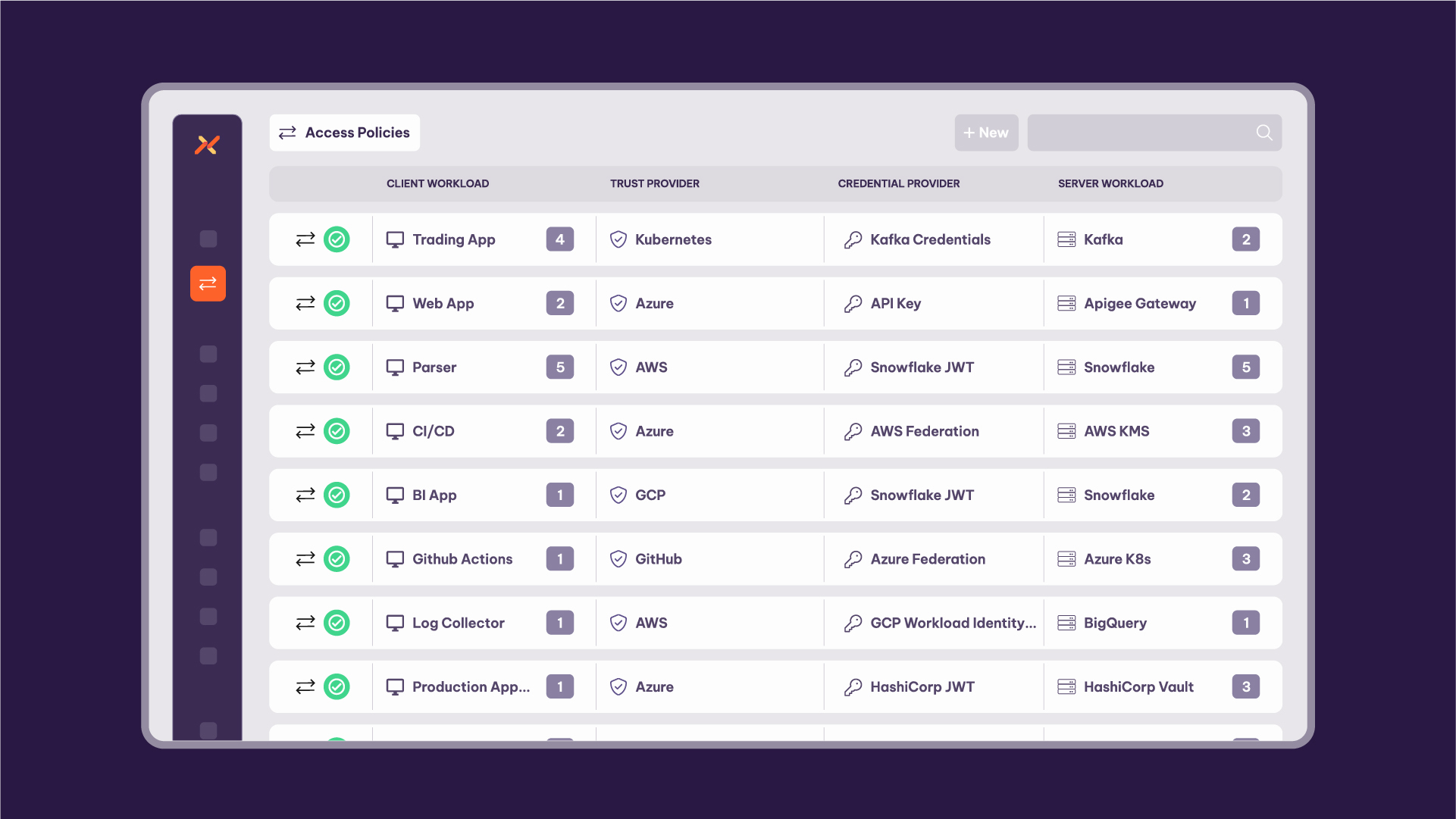
Aembit is the workload identity and access management platform (IAM) that enables DevOps and security personnel to manage, enforce, and audit access between workloads, across clouds, SaaS, and data centers. Workload IAM is analogous to “user IAM” or “customer IAM” platforms, but manages the identities of, and access from, workloads (typically, software applications) to services, rather than from humans to services. With Aembit’s identity control plane, DevSecOps teams can fully automate secretless, policy-based, and Zero Trust workload access.
Key Capabilities / Features
With Aembit, enterprises can:
--Secure access to sensitive resources by validating access rights in real-time using the native identity of the workload and an access policy, instead of a static identity secret.
--Harden environments by accelerating the transition from static secrets to both secretless access tokens and secretless workload identity verification.
--Reduce risk by providing Zero Trust conditional access based on posture from CrowdStrike and Wiz, and access conditions such as time, geolocation, threat data, and more.
--Simplify operations by providing a discovery workflow to bring new workloads under management easily.
--Scale and automate DevOps by minimizing secrets rotation, reducing key sprawl, and the need for secrets scanning.
--Remove the burden of auth from developers through no-code auth-as-a-service.
--Accelerate incident response and audit/compliance with identity-based logging and one-click change to access rights.
Aembit supports a broad range of workload environments (major clouds, SaaS, and on-prem) and compute (VMs, Kubernetes, and serverless) and a wide variety of credential types (OAuth, OIDC, JWT, API keys, username/pw). Aembit scales to tens of thousands of workloads and is automated through infrastructure as code.
Aembit is SaaS, with a production class free tier and self-service deployment. Larger customers typically start with a high-priority use case such as access to a database, securing cross-cloud access, sensitive SaaS service, or hardening CI/CD.
How we are different
--Many workloads rely on static, or long-lived credentials. These credentials, which rarely change, are often hard-coded into applications and tracked in spreadsheets, creating a significant security vulnerability. Traditionally, secrets managers have been deployed to mitigate these risks by centralizing credential storage and management. However, secrets managers can introduce their own complexities, such as the overhead of managing the secrets manager itself, implementing it across multi-cloud environments, and enabling least-privilege access to secrets within the vault. With Aembit, dynamic credentials deliver short-lived access credentials that are injected just-in-time. Applications don’t need to know the credentials, and they are valid for only a short period. Aembit also implements workload Zero Trust by adding conditional access. For example, Aembit can check CrowdStrike or Wiz posture assessment before authorizing access.
--DevOps and security teams often need to integrate multiple systems, like cloud IAM, secrets management, and audit logging to meet security and compliance requirements. This is difficult to implement and expensive to operate. Aembit simplifies and accelerates application delivery by handling workload authentication, authorization, and logging -- from a single dashboard -- for users, regardless of system or environment.
--Implementing workload-to-workload access today requires a developer to implement something extra in their application. It’s time consuming, frustrating, and inconsistent. That is time and effort that could go toward developing revenue-generating features.
Aembit removes the burden of auth from developers, while ensuring that identity and access management is implemented consistently everywhere. Our transparent proxy is deployed as a sidecar or agent and takes care of auth.


