Photo Gallery
 |

 |
ANY.RUN Threat Intelligence Lookup

Additional Info
| Company | ANY.RUN |
| Company size | 100 - 499 employees |
| World Region | Middle East |
| Website | https://any.run/ |
NOMINATION HIGHLIGHTS
ANY.RUN Threat Intelligence Lookup addresses a critical market need by enhancing organizations’ cyberattack response capabilities and improving overall security efficiency. It supports compliance requirements, increases security ROI by reducing investigation time and effort, and delivers precise threat intelligence.
For security teams, ANY.RUN TI Lookup accelerates threat research, enabling swift and accurate connections between isolated IOCs and specific threats or known malware campaigns. It ensures analysts stay ahead of emerging malware trends while offering workflow flexibility through both a web UI and API integration.
For organizations, TI Lookup minimizes risks by detecting threats as they emerge and enabling proactive responses to mitigate potential damage. It also supports employee training by providing access to a detailed knowledge base on malware behavior, facilitating the onboarding of new hires and junior researchers while strengthening their skills.
Key Capabilities / Features
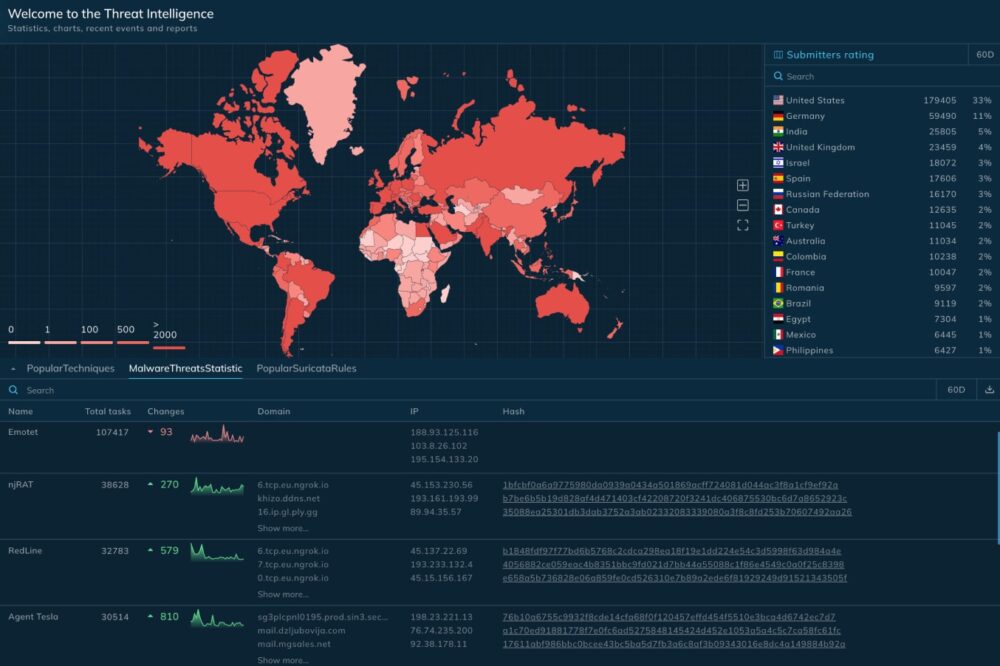
TI Lookup enriches and supports further investigations by providing examples and contextual data from other analyses to aid decision-making. While competitors primarily focus on searching by IOCs, the product offers the unique ability to query events, leveraging its rich sandbox dataset to uncover a wider scope of threat intelligence.
Up-to-Date Data and Real-World Samples.TI Lookup houses an extensive collection of unique data gathered from its cloud-based sandbox, where cybersecurity analysts worldwide upload fresh samples daily. These samples allow for extracting a variety of events and indicators, such as threat types and names, OS events, hashes, and more, including searches using YARA rules.
TI Lookup provides access to data that is difficult—or even impossible—to find in other open sources, giving users an unmatched edge in threat intelligence and investigation.
Subscription for Event Updates. Users stay informed with real-time updates on events relevant to their organization. These updates enhance security posture and enable strategic and tactical responses to threats targeting the company's infrastructure.
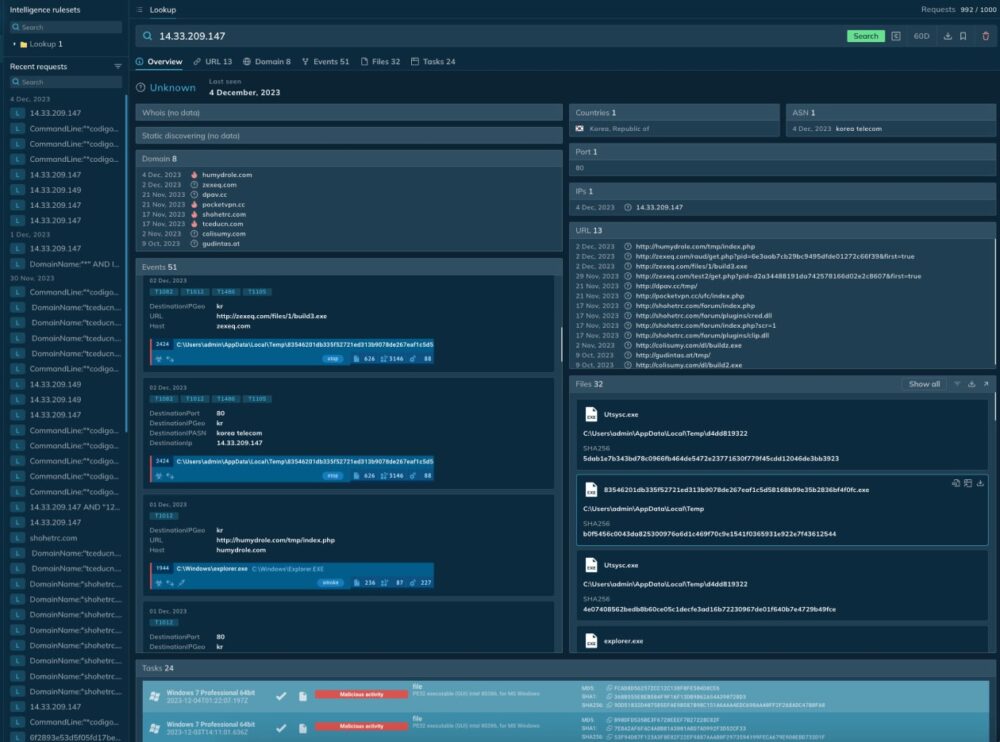
Fast and Contextual Insights. TI Lookup delivers deep contextual information within seconds. It reveals how events function, whether they are linked to threats, and the nature of these connections. With a lightning-fast response time of just two seconds when searching events from the past six months, the platform significantly simplifies and accelerates the investigation process.
By providing actionable insights, TI Lookup empowers organizations to respond quickly and effectively to emerging threats, improving overall cybersecurity resilience.
How we are different
1) ANY.RUN Threat Intelligence Lookup offers unique advantages that distinguish it from competitors. It provides a fast, flexible, and detailed threat investigation tool that simplifies the research process. The service supports deep exploration of attack structures, enabling analysts to investigate threats across system event sequences—such as registries, traffic, files, and process strings—unified by a single analysis.
2) With access to fresh data from interactive analyst sessions, including insights unavailable through automated data collection, the platform enriches investigations with IOC, IOA, and IOB updates from real-time sandbox analyses. ANY.RUN's powerful wildcard search and YARA integration allow for complex queries across loosely related events, enhancing threat validation and uncovering hidden connections.
3) Additionally, the platform enables users to monitor changes in threat indicators, access a vast knowledge base, and improve response times.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



