AttackIQ Adversary Exposure Validation Platform
Recognized in the Category:
Photo Gallery
 |
 |
AttackIQ Adversary Exposure Validation Platform

Additional Info
| Company | AttackIQ |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://www.attackiq.com/ |
NOMINATION HIGHLIGHTS
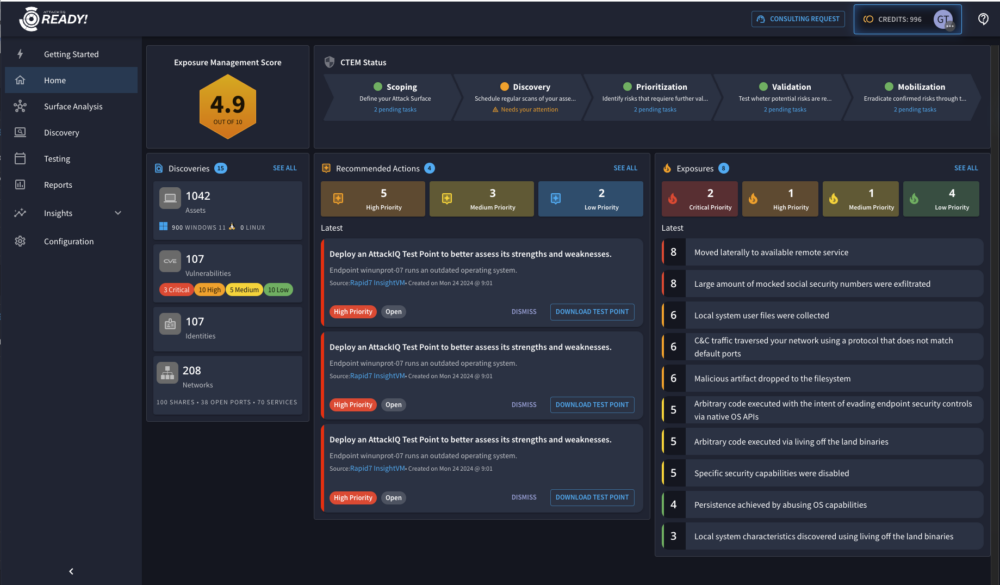
Traditionally, security teams conducted siloed vulnerability scanning to identify vulnerable assets and episodic penetration testing or red team exercises to assess risk posture. These efforts were not aligned with the organization’s actual threat environment, and the results were wholly inadequate to identify the breadth of failures of secure controls and resulted in large vulnerability backlogs.
The real shift left comes from integrating live threat intelligence and continuous validation of risk posture. AttackIQ helps organizations prioritize exposures based on whether they align with the adversary behaviors targeting them. With predictive posture validation, organizations can analyze indicators of activity that reveal adversaries’ potential moves.
In February 2025, AttackIQ will announce the launch of its Adversarial Exposure Validation (AEV) platform, designed to help security teams proactively identify, assess, and mitigate adversarial risks. This new offering ensures organizations can stay ahead of evolving threats by continuously validating their security posture against real-world adversary behaviors.
AtackIQ’s AEV platform takes data about vulnerabilities, potential adversary attack paths, and intelligence on where threat actors are actively operating. Then we apply AI to synthesize it all, giving security leaders a real-time, prioritized view of what needs immediate attention.
This comprehensive view fuels three key capabilities:
– We scale offensive testing by augmenting red teams — allowing organizations to emulate advanced adversaries without manually orchestrating every test.
– We optimize security controls through breach and attack simulation, automatically validating whether defenses can detect or prevent known adversary tactics.
– We reduce overall exposure by taking an end-end view, integrating live threat intelligence with a view of the overall attack surface and validating the controls that defend that attack surface, to determine which exposures matter the most for swift remediation.
Put together, these capabilities ensure organizations to can identify potential weaknesses and proactively eliminate them before
Key Capabilities / Features
AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, providing a structured, risk-based approach to continuous security assessment and improvement. While CTEM offers organizations a guide for risk management, AttackIQ’s AEV Platform makes it actionable. By simulating real threats with breach and attack simulation and automated penetration testing, AttackIQ’s AEV Platform uncovers exposures, prioritizes risks, and sharpens defenses in a cohesive, continuous process. This integrated approach delivers a data-driven defense against evolving threats.
As the security market consolidates, organizations are looking for integrated solutions that align with CTEM. CTEM itself is a framework, guiding the continuous assessment and prioritization of threats. By contrast, AEV is a category of technologies that combine Breach and Attack Simulation and Automated Pentesting. AEV focuses on validating security controls in real-time by emulating adversary behavior, effectively bridging the gap between knowing about a vulnerability and understanding its true risk.
When these two concepts converge, businesses gain a unified, threat-informed approach — reducing noise, prioritizing critical exposures, and delivering clear use cases like defensive posture optimization, exposure awareness, and scaled offensive testing. Rather than dealing with disjointed point solutions, security teams can continuously validate where they’re most exposed and take action faster
Key Features Include:
- Attack Surface Scanning – Continuously discovers and assesses externally exposed assets, giving security teams real-time visibility into potential entry points.
- Attack Path Management – Maps adversaries’ attack paths to expose vulnerabilities and high-risk areas before they can be exploited.
- Discovery and Threat Intelligence Integration – Enriches exposure findings with real-world threat intelligence, helping teams prioritize risks effectively.
- Exposure Validation and Testing – Automates exposure validation, enabling organizations to measure defensive effectiveness and optimize security investments.
How we are different
- Our core strength is continuously validating and optimizing organizations’ defensive posture through adversary campaign emulations. We leverage both atomic tests — focusing on discrete tactics or techniques— and full attack graphs that replicate realistic, multi-stage adversarial behaviors. Threat-informed testing ensures we’re always aligning with real-world attacker TTPs, making sure defenses are ready for the threats that matter.
- We automate purple teaming by unifying red and blue team efforts in a collaborative, iterative process that steadily identifies exposures and refines security controls. Meanwhile, detection engineering focuses on creating and validating the rules that enable quick, accurate threat identification.
- All of this is made possible by the most scalable and open attack simulation platform, our rich library of authentic attack content, and our deep integrations across organizations’ environments — covering email gateways, firewalls, WAFs, EDRs, SIEMs, and more. By ensuring we plug into every critical security layer, we can deliver more targeted and comprehensive validation, helping teams quickly uncover and remediate gaps, and ultimately strengthen overall defensive posture. This actionable intel is something you won’t find anywhere else. It fuels our ability to scale offensive testing through three primary augmentation uses. First, if your red team uncovers specific threat intelligence artifacts — like indicators of compromise — they can create custom attack scenarios to see if defenses hold. Second, insights from prior engagements can be automatically tested at scale to ensure lessons learned are never lost. Finally, you can leverage red team reports themselves as a source of CTI, feeding back into the discovery and scoping phases for automated testing. Together, these capabilities provide continuous, intelligence-driven offensive security that keeps pace with real-world threat actors.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



