Attivo Networks Endpoint Detection Net Suite
Recognized in the Category:
Photo Gallery
 |
 |
Attivo Networks Endpoint Detection Net Suite

Additional Info
| Company | Attivo Networks |
| Company size | 100 - 499 employees |
| Website | https://attivonetworks.com/ |
NOMINATION HIGHLIGHTS
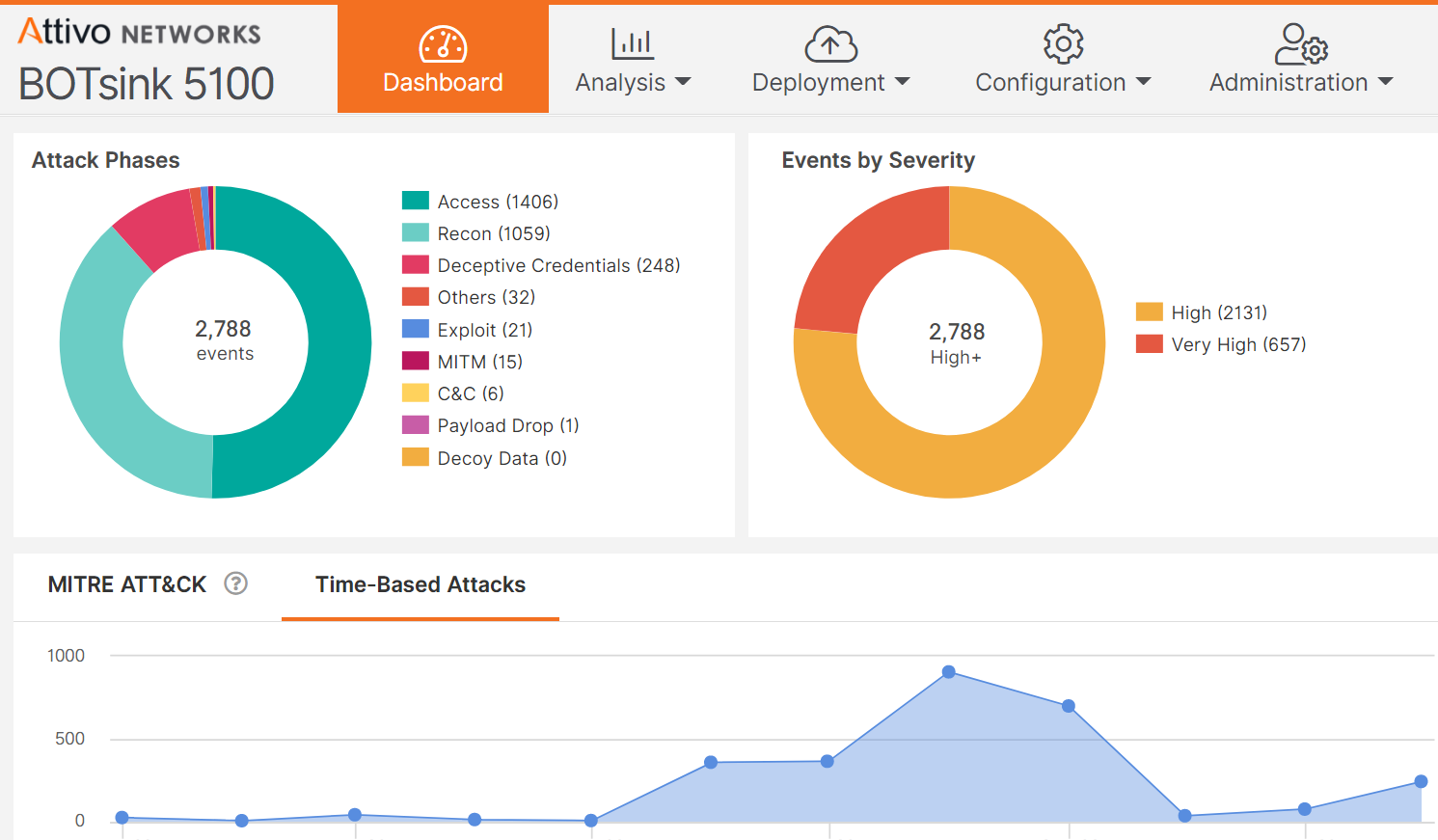
The Attivo Networks Endpoint Detection Net changes the game so that attackers can’t break out, move laterally, or escalate privileges from an infected endpoint. Every endpoint essentially becomes weaponized to disrupt an attacker’s attempts to break out and advance their attack. The attack methods that the solution efficiently derails include, but are not limited to:
• Access and theft of local and admin credentials – visibility and obfuscation
• Unauthorized Active Directory queries – hide information, alert, and return fake data to queries
• Enumeration of file shares and connected systems (anti-ransomware) – hide and deny access to data
• Network reconnaissance – hide hosts (production assets) and available services on these hosts
• Man-in-the-Middle attacks – prevent theft of credentials in transit
Locking down the endpoint with the Attivo EDN suite dramatically reduces risk by detecting attacks early and preventing lateral movement. Plus, alerts are substantiated, actionable, and provide company-centric threat intelligence for stopping an attack, hunting threats, and remediating faster. Integrations with EDR and other security solutions boost detection performance and offers incident response automation for operational efficiencies.
How we are different
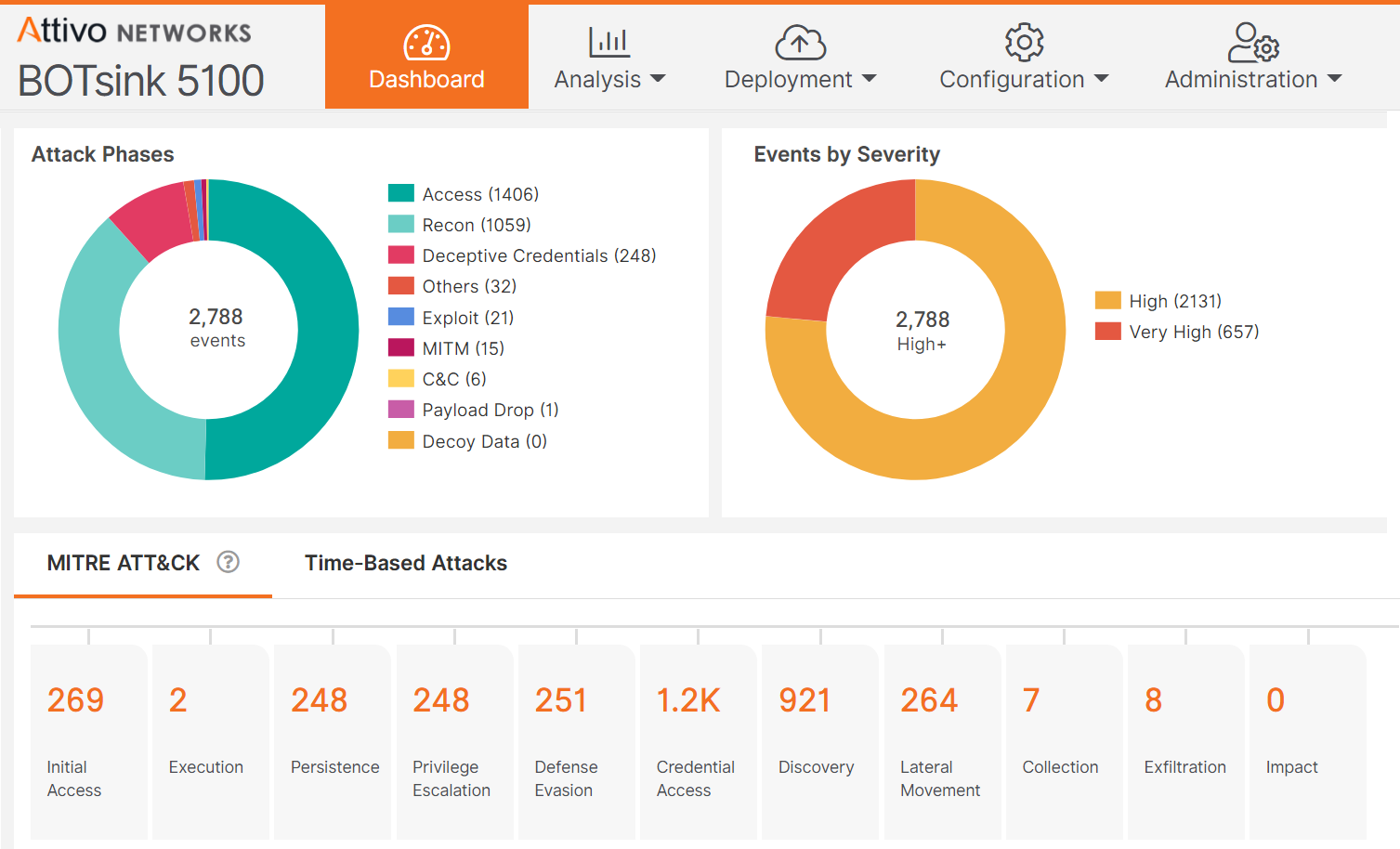
The Attivo Endpoint Detection Net (EDN) Suite takes a different approach than traditional endpoint protection (EPP) and endpoint detection and response (EDR) solutions. Instead of preventing the initial compromise, the Attivo EDN solution prevents the attacker from breaking out and moving laterally, stealing credentials, and elevating privileges. MITRE ATT&CK® DIY testing has proven that the EDN solution can boost detection performance by an average of 42%.
Lateral movement: Attackers looking to break out from an endpoint will need to move laterally. Attivo disrupts their attack, preventing them from moving laterally by hiding and denying access to real data and Active Directory objects and detecting attempts to fingerprint an endpoint to find vulnerable ports and services.
Credential theft and privilege escalation: Sophisticated attackers will steal credentials and seek to enumerate Active Directory as a means to gain domain control. The EDN suite prevents them from doing this by making it easy for organizations to see and remediate exposed credentials and attack paths. It also obfuscates real credentials with fake ones that breadcrumb to engagement servers and protects Active Directory by detecting and alerting on unauthorized queries and returning fake data that misinforms attacker’s tools to derail the attack. The solution gathers attacker Tactics, Techniques, and Procedures (TTPs), and Indicators of Compromise (IOCs) for accelerated and automated incident response.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



