Photo Gallery
 |
 |
Attivo Networks ThreatDefend Platform

Additional Info
| Company | ATTIVO NETWORKS |
| Company size | 100 - 499 employees |
| Website | https://attivonetworks.com/ |
NOMINATION HIGHLIGHTS
Attivo Networks, an early innovator in commercial-grade threat deception technology, has seen growth soar as enterprise, midmarket, and government organizations rapidly adopt deception technology. Customers commonly cite that they have successfully reduced cybersecurity risks by closing detection gaps and reducing attack dwell time experienced when an adversary bypasses perimeter defenses. Attivo Networks leads in deception technology innovation with hundreds of customers, has expanded globally with operations now in North America, Europe, Middle East, Asia, Australia, and LATAM, and in the last two years achieved recognition with over 125 awards for its products, leadership, and market impact. The company has received elite recognition as a Cool Vendor by Gartner, Inc. and scored the highest rankings in their recent deception technology comparison report with 13 out of the 14 categories receiving the highest scores possible. The company, for 2 consecutive years has garnered recognition as the 31st fastest-growing company in the Deloitte 500 list and won Fast Company’s Best Workplaces for Innovators Awards.
The ThreatDefend solution efficiently addresses the most complex detection challenges:
1. Accurate and substantiated detection of known and unknown threats
2. Coverage for all attack surfaces
3. Detection across all lateral movement attack methods
4. Easy to manage and take action on alerts
5. Company-specific threat intelligence and vulnerability assessment
6. Is not siloed in operations and serves as a force multiplier to existing controls
7. Highly effective for insider-, supplier-, and external threat detection – A joint survey with EMA found deception technology to be the top tool of choice for detecting insider threats
As the most comprehensive platform available, the ThreatDefend deception fabric provides scalable coverage of endpoints, networks, cloud (including, access management, container, and serverless functions), data centers, remote offices, IoT, medical IoT, ICS-SCADA, POS networks, and network infrastructure.
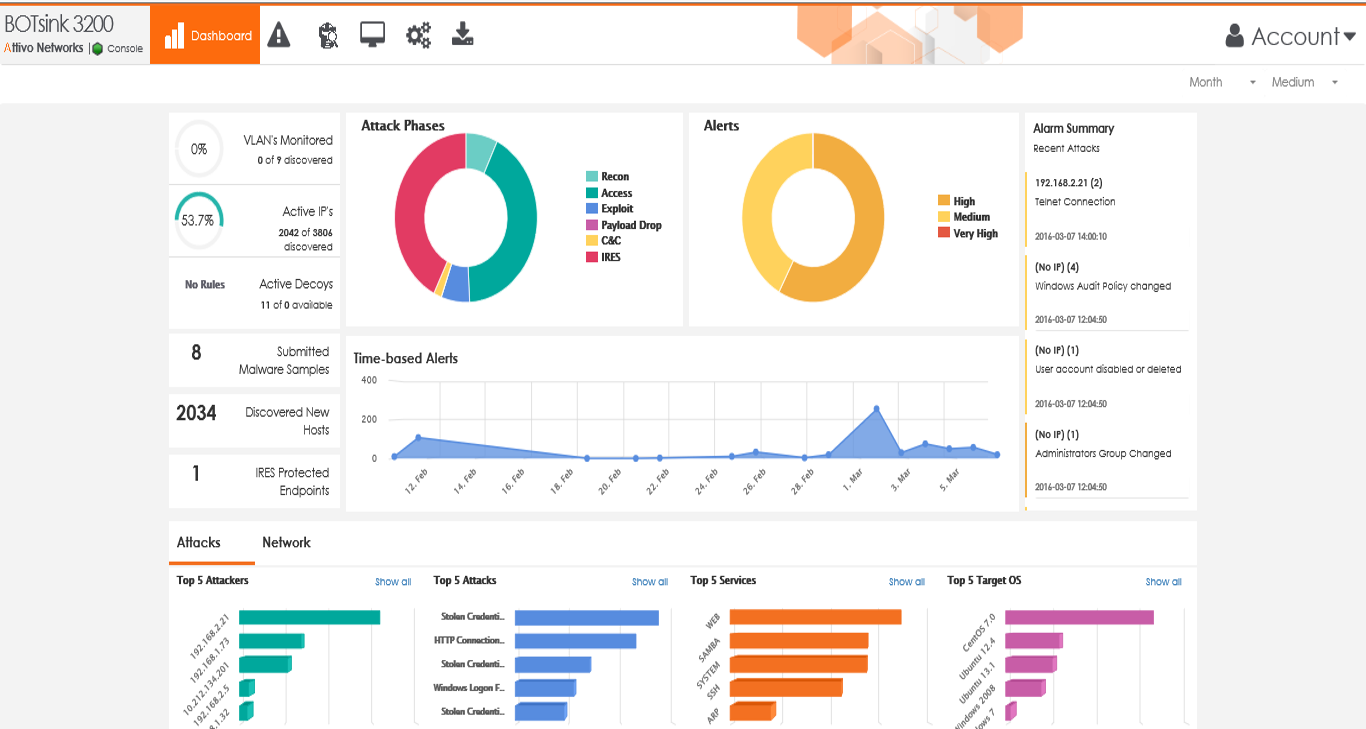
Ultimately, security teams gain visibility, detection, and response automation in a way that other deception or threat detection controls can’t achieve.
How we are different
The most authentic and believable deceptions through its camouflage architecture, using full OS, application, Active Directory, data, and database deceptions for optimal believability and blending in with the environment. Golden-image uploads and emulations provide additional customization so that solutions can look like typical production endpoints and servers or network infrastructure, ICS, IoT, Medical IoT, POS, or even a device within energy substations.
Supports multi-cloud environments for AWS, Google, Azure, and Oracle: decoy storage buckets, deceptive credentials, serverless functions, IAM Access Keys/Tokens, SSH keys, containers, DNS entries, and CloudWatch and CloudTrail monitoring.
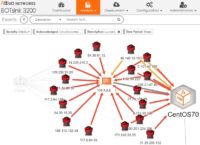
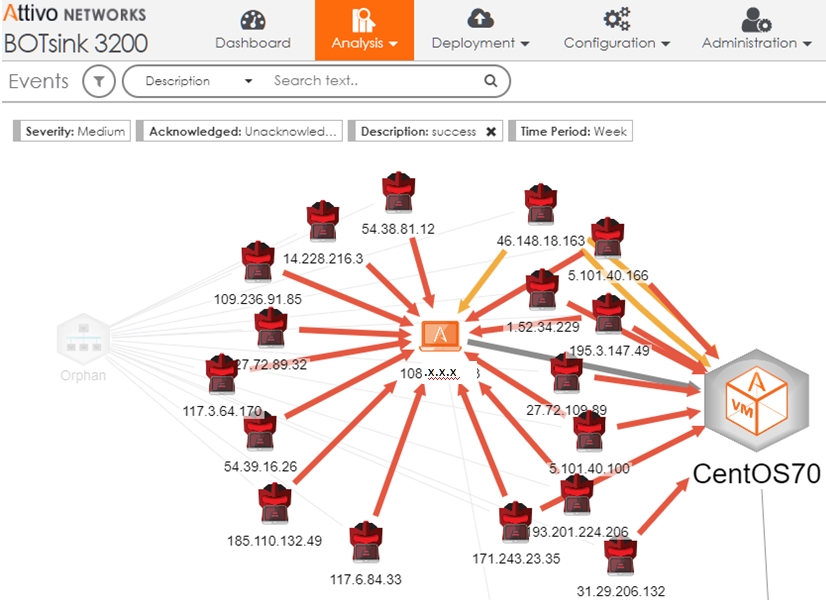
Attivo offers unique functionality that intercepts Active Directory queries, hides the real response and data, and adds deceptive content to misinform and misdirect the attacker while making them distrust their tools. By creating an altered reality for the attacker valuable enterprise resource information is hidden from the attacker and with the redirection of activities into the deception environment, security teams can safely study the attack and gather Tactics, Techniques, and Procedures (TTPs), along with company-specific threat intelligence.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



