Photo Gallery
 |
 |
Attivo Networks ThreatDefend Platform


Additional Info
| Company | Attivo Networks |
| Company size | 100 - 499 employees |
| Website | http://www.attivonetworks.com |
NOMINATION HIGHLIGHTS
Attivo ThreatDefend Platform
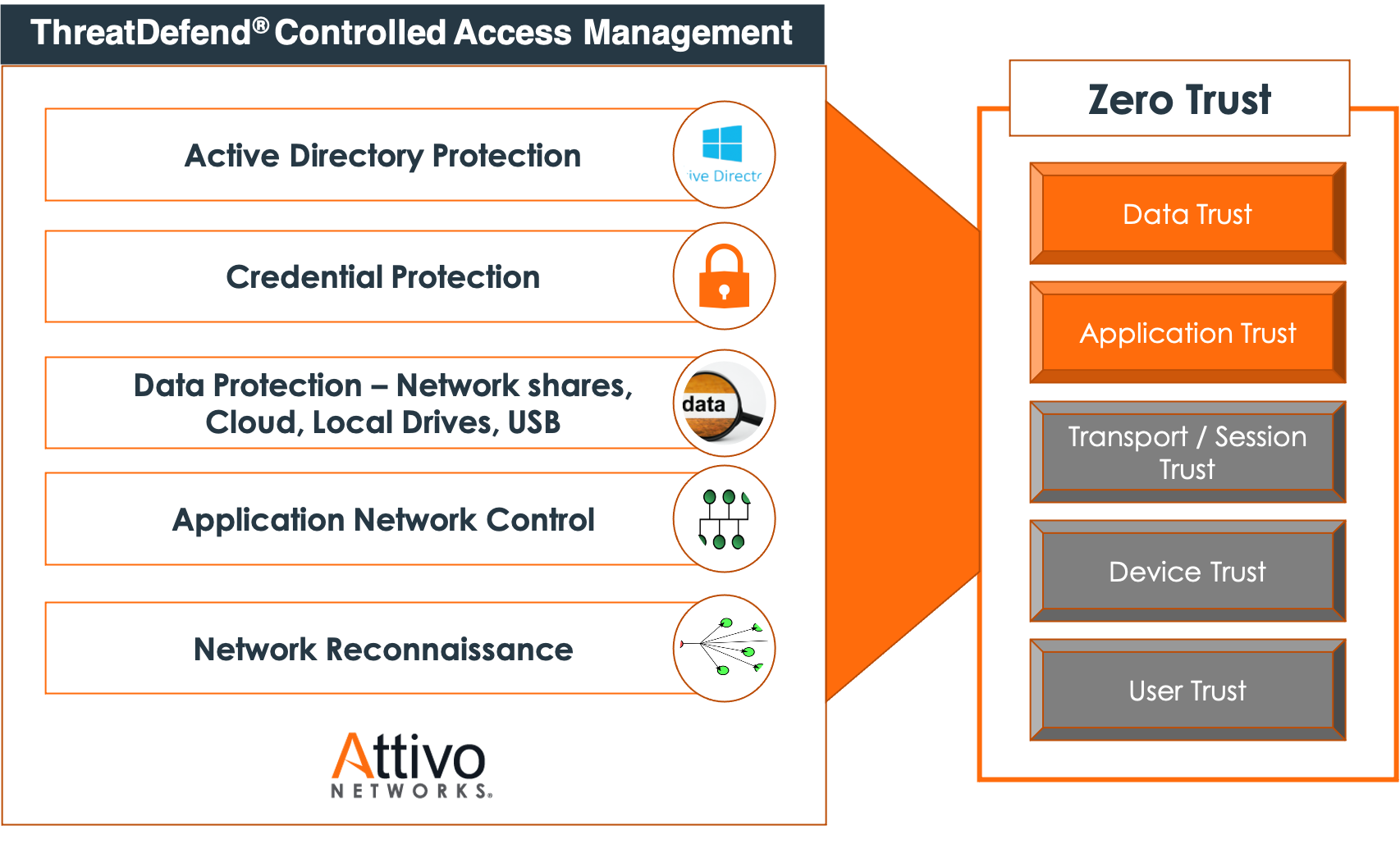
Zero Trust builds on five layers – user, device, transport/session, application, and data. The majority of security tools focus exclusively on user and device trust, leaving a gap where unauthorized users can access applications and data if they have credentials or found access. Attivo adds additional access management functions specifically for data and applications to close this gap.
With Data Trust, regarding validated users, once the network authorizes a user and validates access, the user can access all the data on the local system and within AD. The Attivo ThreatDefend Platform® hides and denies access to local files, folders, network or cloud shares, removable storage devices, and privileged accounts. It limits access unless the accessing user has specific permissions, not just general permissions to access all the data. Additionally, the ADSecure solution conceals and restricts access to sensitive AD objects, allowing access only from authorized applications, returning decoy objects to unauthorized applications. ADSecure permits domain administrators and other authorized groups to query AD actively, but not accounts operating with user-level permissions.
With Application Trust, ADSecure limits access to only trusted or validated applications for specific data forms within the user context. Not only must the querying user be authorized, but so does the application. For example, the solution allows standard Windows User Manager snap-ins to access user and group permissions, but not other applications like command line or PowerShell interfaces. The ThreatDefend platform Deflect function can implement Application Trust for network reconnaissance when attackers attempt to find open ports and services. Attackers use authorized applications to connect to open ports and services. Should an attacker attempt to probe for open ports or services to compromise, the Deflect function redirects the activity to a decoy with a corresponding port and service to engage the attacker.
How we are different
The Attivo Networks ThreatDefend® platform is different because it focuses on data and application trust instead of user and device trust. The solution offers Zero Trust controlled access management functions to allow applications access to data and resources once the domain authorizes them. It does so without interfering with daily operations. The platform’s components work together to deny, detect, and derail discovery, lateral movement, privilege escalation, and data gathering activities that attackers could get away with if they compromise a validated user account on an authorized device.
For Data Trust, the platform controls access to data on the local system and within AD. The solution hides and denies access to local files, folders, network or cloud shares, removable storage devices, and privileged accounts, preventing unauthorized users from accessing these objects. Additionally, the ADSecure solution can conceal and restrict access to sensitive AD objects. Plus, it can return disinformation, which will misdirect attackers into engagement servers.
The ADSecure component of ThreatDefend limit access (Application Trust) to only trusted or validated applications for specific data forms within the user context. Not only does the user issuing the query have to be authorized, but so does the application invoking it. Additionally, the Deflect function provides Application Trust, redirecting attackers attempting to find open ports and services away from their targets and into decoys that alert on and record their activities.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



