Photo Gallery
 |

 |
Attivo ThreatDefend for ICS Systems

Additional Info
| Company | ATTIVO NETWORKS |
| Company size | 100 - 499 employees |
| Website | https://attivonetworks.com/ |
NOMINATION HIGHLIGHTS
Critical Infrastructure (CI) provides essential services for public health and safety, commerce, and national security. While most threats to CI were physical and tangible, such as natural disasters and physical attacks, networking the Operational Technology (OT) that make up CI for management and operations has added digital and virtual threats that are much more difficult to defend against. Compounding this problem is the lack of OT-specific security solutions that put it at higher risk than Information Technology (IT) networks. The ThreatDefend platform offers deception capabilities to defend CI and OT networks against attacks targeting them.
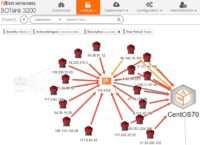
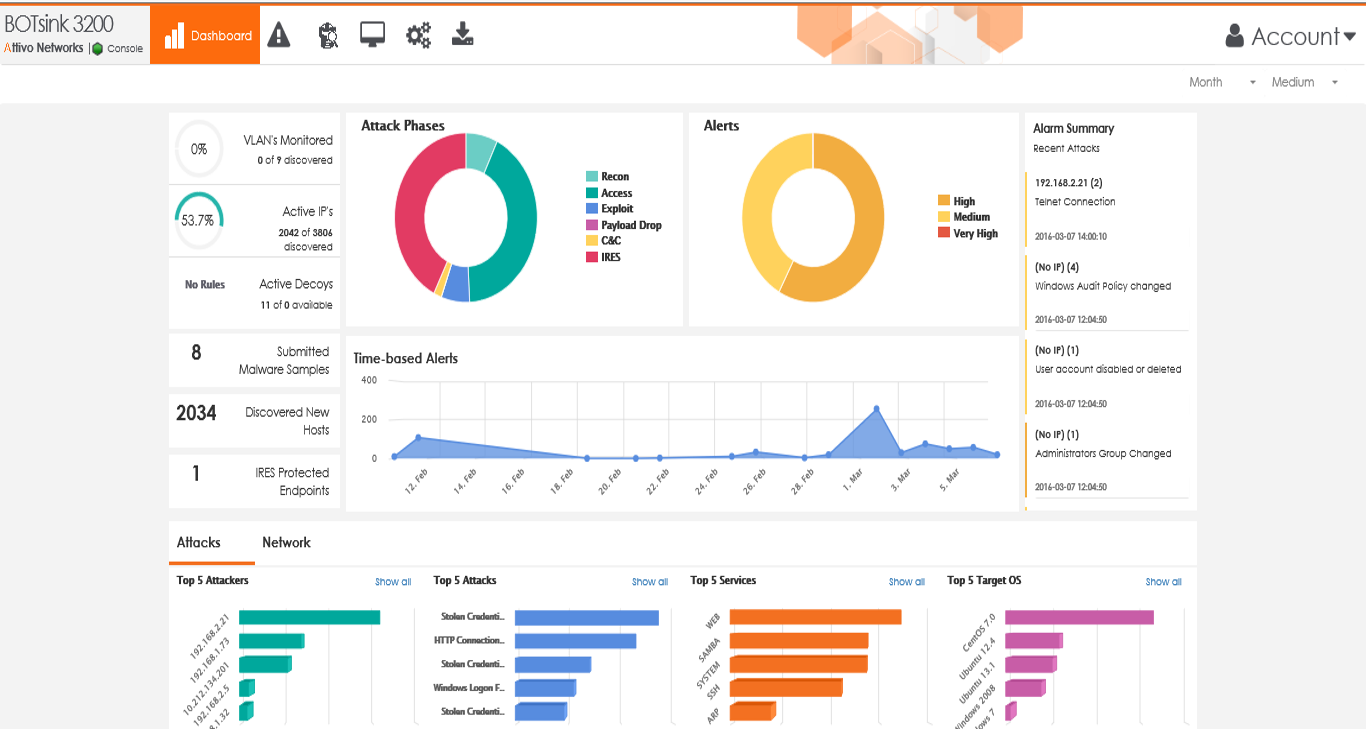
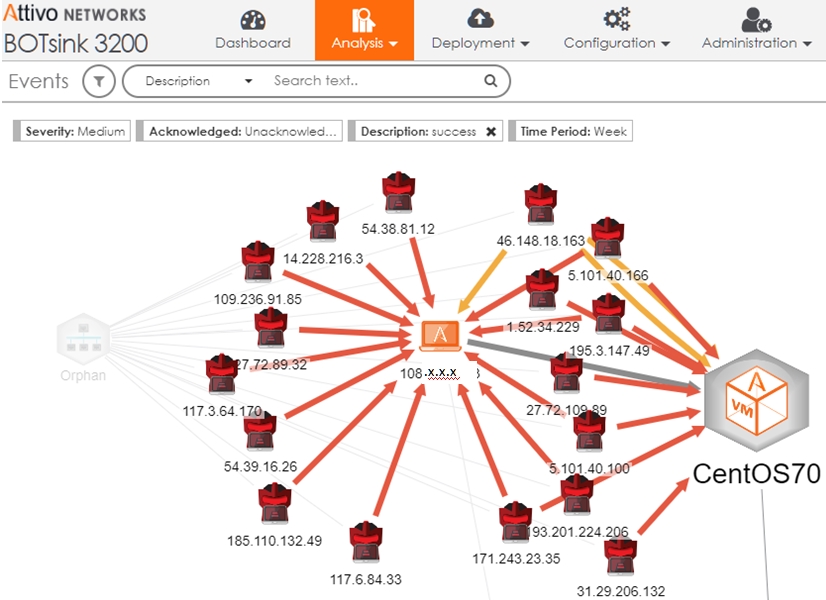
The ThreatDefend ICS solution creates a deception environment composed of network decoys, deception credentials, fake applications, and false data to detect attackers early in the attack cycle as they attempt to conduct reconnaissance, steal credentials, and move laterally in both IT and OT networks. The platform deploys with little operational or management effort and provides a full fabric of deception that blankets the enterprise to detect in-network attackers, provides unparalleled visibility into suspicious or malicious activity, and collect intelligence to improve defenses.
The platform creates decoys that mirror production ICS/SCADA devices. These could be remote sensors, voltage regulators, fuel pumps, or SCADA clients and servers. These decoys deploy in the OT network to provide visibility and early detection of suspicious activity. Alerts do not trigger based on signatures or behavior but on confirmed attacker engagement with a decoy, from something as simple as a network scan to full interaction. The platform also creates deceptive credentials that appear as authentic CI credentials but point to the decoy environment to protect against attackers that steal them to move laterally. The comprehensive deception fabric uniquely protects CI from attackers who have bypassed perimeter defenses and alerts on their presences
How we are different
• Unparalleled visibility and early detection of attack activity that targets CI through a • comprehensive, full fabric deception platform that covers IT and OT networks
• Early and accurate detection of in-network threats that is not dependant on logs, AV or the need to load an agent on an endpoint device. It is also not reliant on signatures for detection and instead uses traps that are designed to detect reconnaissance and lateral movement of threats.
• Misdirects attackers away from production OT networks into decoys that collect company-specific intelligence on their activities to better defend the environment. This includes IOCs and TTPs, which can automatically be shared with other prevention solutions.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



