Photo Gallery
 |
 |
Axiad Cloud

Additional Info
| Company | Axiad |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | http://www.axiad.com |
NOMINATION HIGHLIGHTS
The White House OMB, NIST, and CISA have all come out with strong support of becoming more phishing resistant in the last 12 months. Cyber insurance providers are also placing greater emphasis on becoming more phishing aware, with many reporting that a key to lower insurance rates is taking proactive measures to address the wide range of phishing tools and techniques that are currently in practice.
Unfortunately, the vast majority of legacy multi-factor-authentication (MFA) tools do not provide phishing resistance – e.g., two common methods to bypass MFA are SIM swapping attacks and man-in-the-middle attacks. Further, many of today’s Identity and Access Management (IAM) tools widely used on the market do not have phishing resistance built in – many use legacy MFA approaches mentioned above that can be compromised by modern tactics.
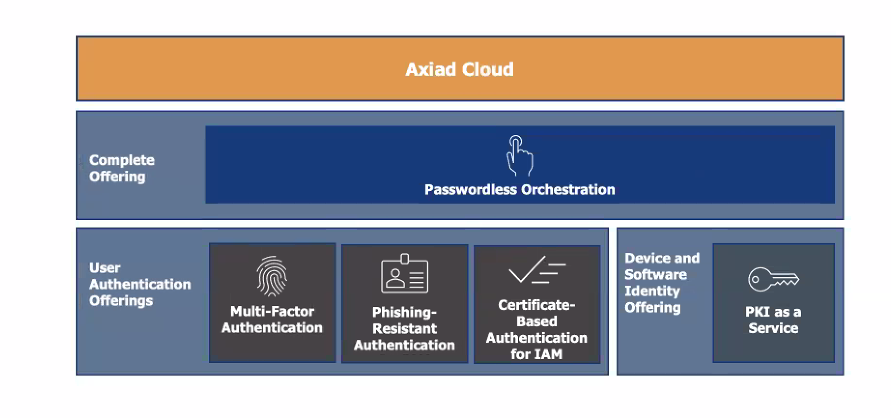
Axiad’s Phishing-Resistant MFA provides consolidated, consistent, and efficient passwordless and phishing-resistant MFA for end users. It supports the broadest range of enterprise-grade phishing-resistant methods, from FIDO and PIV, and certificate-based authentication (CBA) to government-grade, phishing-resistant Authenticator Assurance Level 3 (AAL3) hardware authenticators.
One key example of Axiad’s phishing resistance prowess is its CBA for IAM offering. This turnkey SaaS offering supports a wide range of smart cards and hardware devices (such as YubiKey) without requiring a Trusted Platform Module (TPM). This combination of packaging and flexibility overcomes the organizational barriers to adoption. It supports Microsoft’s initiative to make it easy for Azure users to implement phishing-resistant MFA and also ensures a seamless migration from legacy infrastructure to the cloud.
Axiad Cloud is trusted by government agencies and Fortune 500 companies across highly regulated industries such as financial services and healthcare, as well as aerospace & defense, oil & energy, retail, manufacturing and more, with deployments as large as 140,000 users.
How we are different
• Flexible: Many organizations may require PIV, CBA and FIDO due to varying use cases. Axiad Cloud helps organizations shift from a fragmented to a holistic to approach to phishing resistance by supporting PIV, CBA and FIDO in the same platform. Axiad also recently was appointed to the FIDO Board to help solidify best practices around FIDO2 for future generations of phishing resistance as well.
• Interoperable: A majority of organizations (70% according to a fall 2022 survey conducted by Axiad) have three or more Identity and Access Management (IAM) systems in place, which security teams rely on for authentication and do not wish to rip-and-replace. Axiad’s CBA for IAM can be integrated with an existing IAM system(s) as an add-on feature – delivering a more secure, phishing-resistant form of multi-factor authentication while supplementing what organizations already have in place.
• Efficient: Replaces use of multiple tools for rollout, management, and support of authenticators and credentials. Supports a range of certificate request and delivery workflows. Airlock provides help desk automation by eliminating temporary passwords, automating administration, and enabling self-service credential management. MyCircle empowers self-service by enabling the workforce to issue department-level credential resets, thereby avoiding temporary passwords and increasing efficiency for IT and end users.
.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



