Photo Gallery
|
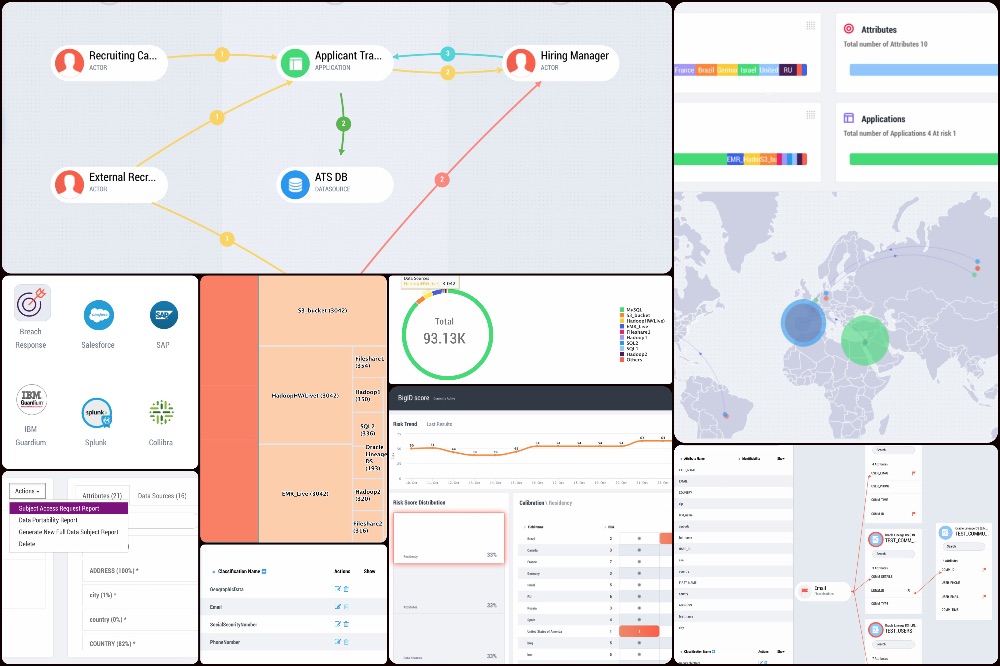
BigID Data Insights

Additional Info
| Company | BigID |
| Company size | 10 - 49 employees |
| Website | bigid.com |
NOMINATION HIGHLIGHTS
BigID is the first identity-aware data protection and privacy solution that can find, inventory and map user data across an enterprise. Because of the solution’s unique ability to identify and catalog data by person or data subject BigID has a unique ability to deliver on several GDPR requirements.
Data Subject Rights
GDPR enshrines individual rights to their data. For enterprises, this means a requirement to find, inventory and report on a person’s data for purposes of an access request, portability request, rectification request or erasure request. BigID provides companies an out of the box solution for managing SAR requests from origination through discovery to reporting. This includes capabilities for customers to embed this functionality in their Web and mobile sights.
Article 30 Record Keeping
GDPR requires organizations to document data collection and processing. Today this is done through interviews, spreadsheets, and Visio. BigID automates the data capture, visualization and DPA reporting including the capture of business information like purpose-of-use.
Consent
BigID’s correlation engine can cross-correlate existing consent logs with data stores to provide organizations a virtual archive of consent by data subject for GDPR reporting or more effective management of consent across company touch points.
Breach Notification
BigID provides companies an ability to compare dark data to internal data to identify whether the data originated in the company, identify impacted users and importantly understand the residency of impacted customers/employees t speed notification requirements.
No other solution on the market currently provides the same breadth of GDPR compliance capabilities based on actual data.
How we are different
- identity, not data-type centric which is critical for satisfying people-centric privacy regulations
- out of the box support for the most urgent and vexing GDPR requirements such as DPIA, Subject Access Rights, Article 30 Record Keeping, Consent, Breach Notification and Pseudonymization
- simple to set-up, can scale across billions of identities, can span data center, cloud, can scan any data store from structured to unstructured to Big Data to cloud to applications like SAP


