Photo Gallery
 |

 |
Black Kite


Additional Info
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | http://www.blackkite.com |
NOMINATION HIGHLIGHTS
At Black Kite, we’re redefining and disrupting traditional vendor risk management with the world’s first global third-party cyber risk intelligence and ratings platform, built from an adversary’s perspective.
We provide intelligence from a technical, financial and compliance perspective: eliminating false positives down to nearly 5%, and ensuring a holistic approach to vendor risk management.
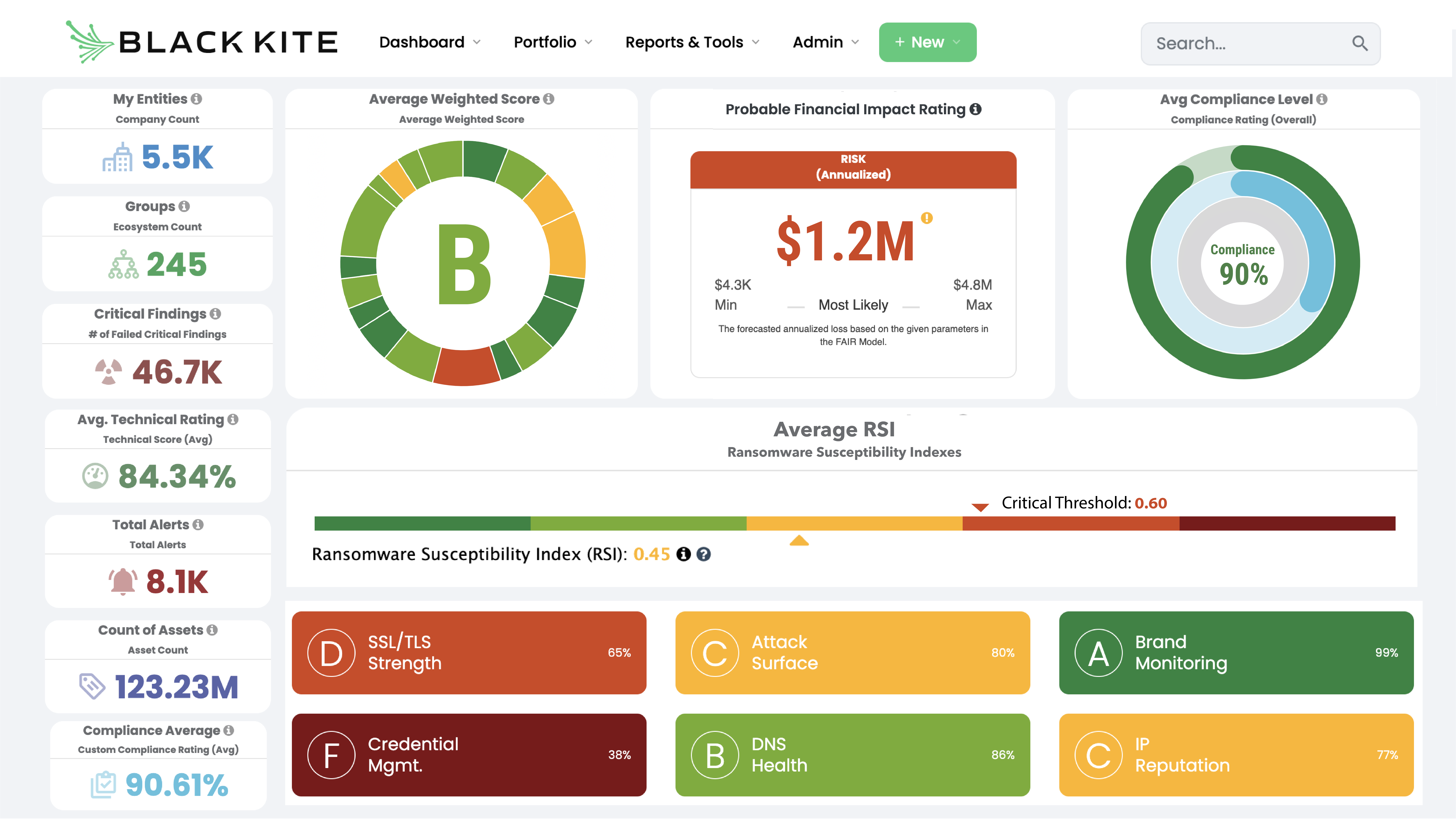
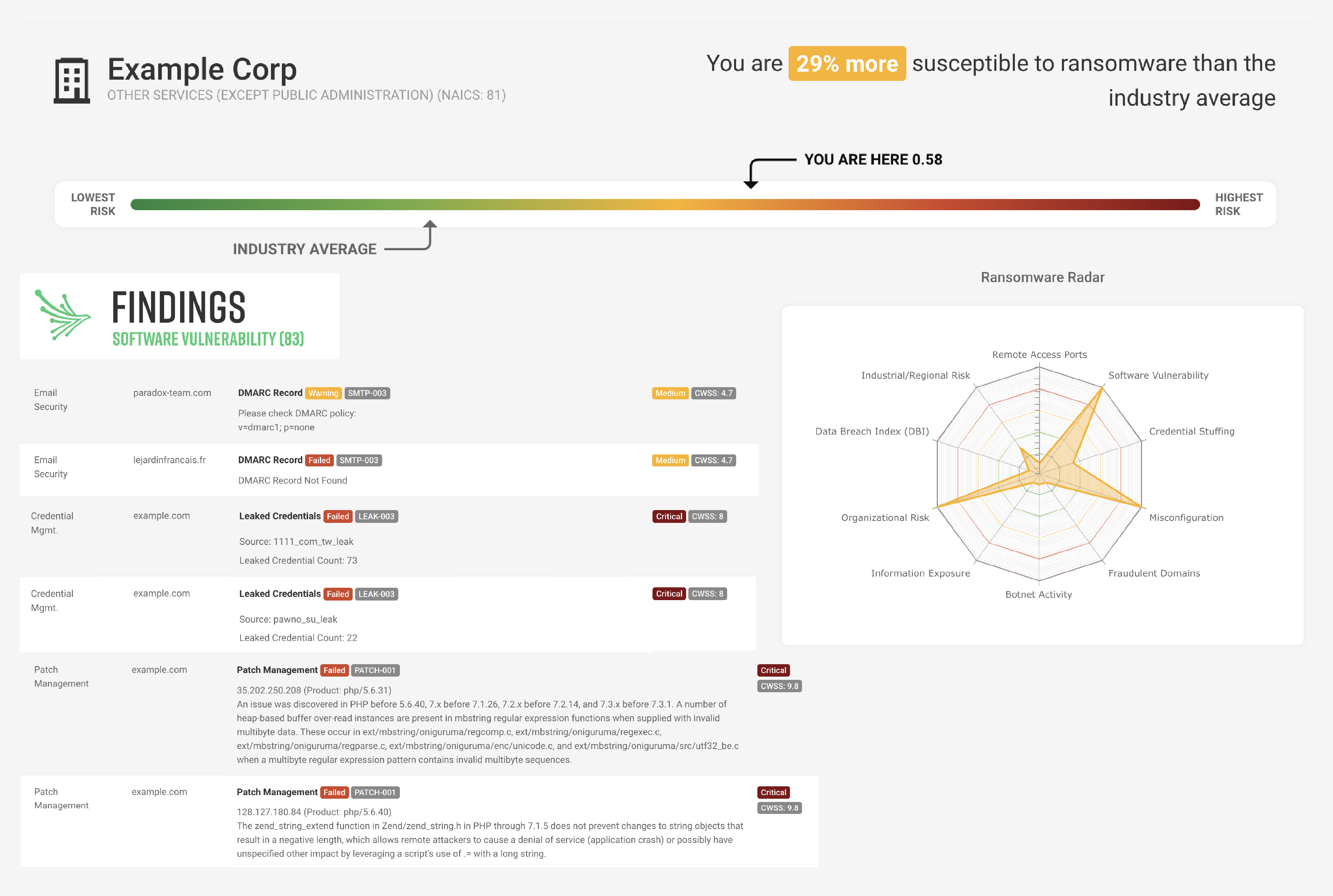
Black Kite is the world’s only fully transparent, standards-based cyber ratings platform, ensuring all users know exactly how their findings are calculated. We map to globally recognized and trusted standards like MITRE and NIST. Our continuously updated global database of risk intelligence provides the confidence to take action, housing data on 34 million companies and counting – 4x that of our competitors. Moreover, every finding we have is correlated to 2 or more data sources, rather than utilized at face value. Black Kite conducts a technical cyber risk rating via easy-to-understand letter grades and defensible data details behind 20+ risk categories and 290 controls. For comparison, the closest competitor offers their users 90 control items.
In addition to an easy-to-understand letter grade rating system, Black Kite is the only SRS tool to quantify risk using Open FAIR™, communicating risk in business terms executives understand. Unlike other cyber rating products, there’s no “secret sauce.” Every third-party cyber risk assessment is standards-based and fully transparent so that all users know exactly how their findings are calculated.
How we are different
1. Standards-based Methodology - (MITRE, NIST, Open FAIR, and other compliance controls) makes it possible to automatically calculate cyber ratings and quantify risk in monetary terms. Competitors use proprietary methods, whereas every finding in the Black Kite platform is standards-based.
2. Data Accuracy - every cyber rating is a weighted average of 20 technical category components, providing unmatched breadth and insight into detected vulnerabilities. Our competition uses a maximum of 10 categories to verify their findings, often missing key signals. Each finding is displayed in a graphical distribution (heat map) to determine the status and severity, as well as cross-correlated with industry standards to further confirm the criticality of each threat.
3. Architecture - By maintaining the largest continuously updated database in the industry, we can provide scalability, automation and reduced costs to operate.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



