Photo Gallery
 |
 |
BlueTalon Data-Centric Security Platform


Additional Info
| Company | BlueTalon |
| Company size | 30 employees |
| Website | http://www.bluetalon.com |
NOMINATION HIGHLIGHTS
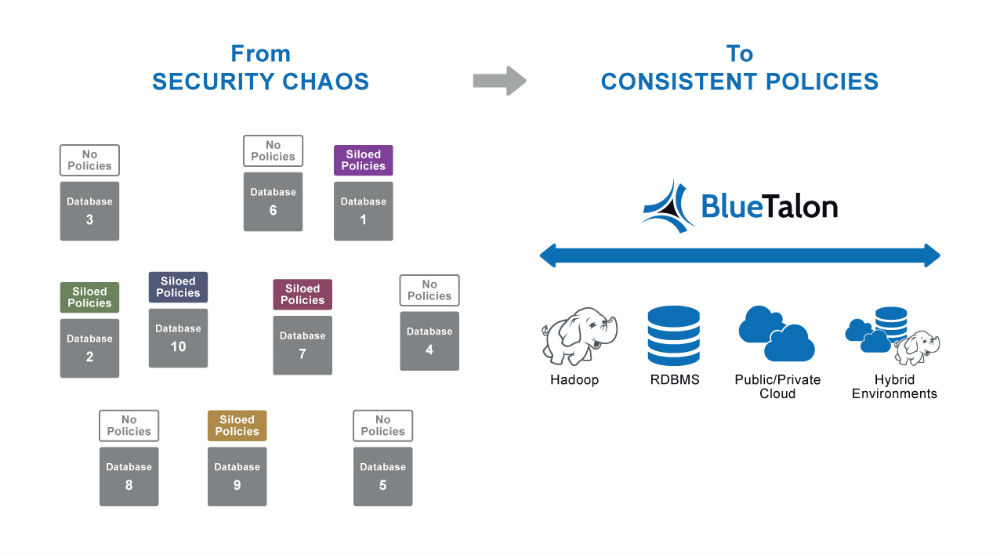
The BlueTalon Data-Centric Security platform enables leading enterprises to deploy precise, consistent, and dynamic user access controls across Hadoop, RDBMS and Big Data environments whether on-premises or in the cloud. Policies are enforced dynamically on all data requests based on user, session and data attributes.
Security staff can eliminate over-provisioning and give users access to the data they need to do their job, not a byte more which automatically minimizes the impact of data breaches due to compromised user credentials.
A complete audit trail of all data requests is also created to support auditing for compliance and to pinpoint and even block abnormal data requests.
How we are different
With this product, BlueTalon introduces a new architecture for data security that is better adapted to today's security challenge at large corporations where the volume of data reaches petabytes and data environments are hybrid and made of Hadoop, RDBMS, NoSQL repositories deployed both on-premises and in the cloud.
Unique benefits include:
(1) Consistency of security policies: Security policies can be written once and deployed on multiple repositories regardless of what they are and where they are located. This eliminates security policy chaos.
(2) Most precise policies, filtering and data de-identification: BlueTalon can operate at any level (table, column, row, cell, partial cell, folder, file, sub-file) to address the most stringent business needs for data protection.
(3) Dynamic data masking: BlueTalon eliminates the need for data duplication when de-identifying data enabling data security to scale to petabyte of data without any performance impact.
With BlueTalon, businesses can safely pursue their new data initiatives and accelerate their digital transformation.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



