Photo Gallery

|
|
Booz Allen’s Threat Hunting

Additional Info
| Company | Booz Allen Hamilton |
| Company size | 10,000 or more employees |
| Website | BoozAllen.com |
NOMINATION HIGHLIGHTS
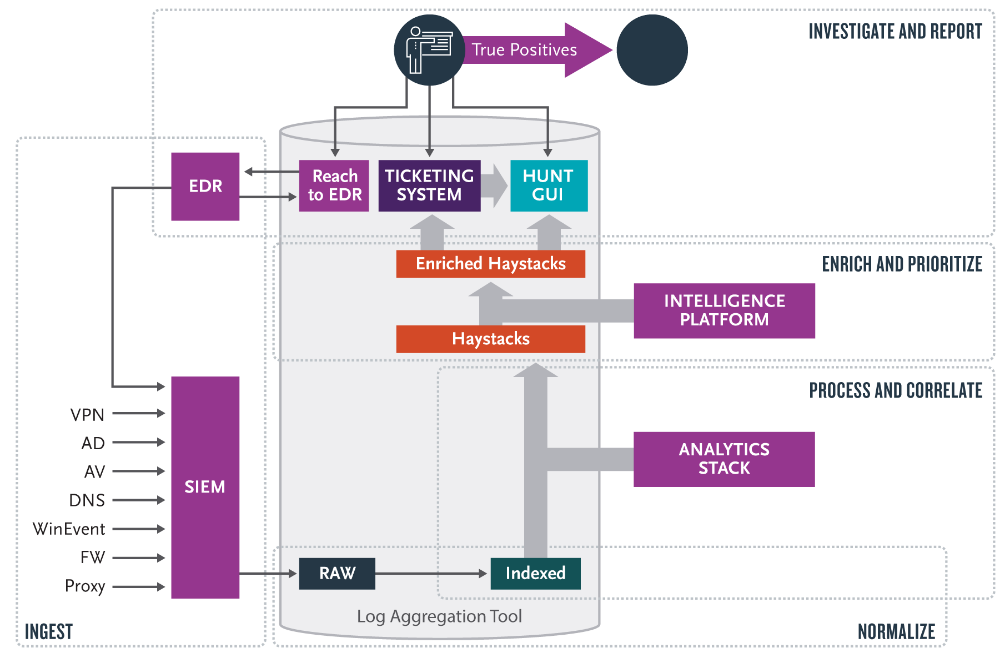
Booz Allen’s pre-eminent technology-enabled service for Threat Hunting (TH) was developed and honed over decades of analytical support to the U.S. Intelligence Community. At the forefront of data science and cybersecurity, we maximize a clients’ previous investment in endpoint detection and response (EDR) and network sensor technology. Without additional proprietary on-premise devices or endpoint agents, our threat hunters utilize a scalable TH platform to ingests, correlate, and enrich data from the top EDR and network defense vendors. We proved our innovation through discovery/disclosure of advanced threats previously unknown across industry and U.S. Government.
Advanced persistent threat actors (APTs) are smart, fast, and engage in long-term campaigns to compromise networks. APTs are skilled at defeating rule-based cybersecurity defenses by upgrading malicious tools, techniques, and procedures – gaining access into a network and then maintaining a hidden presence. Hunting is often considered a post-incident activity, however, our TH is a proactive, cyclical process employed to find APTs who fall below the alert threshold of traditional security information and event management (SIEM) platforms, or for which there are no alerts.
Our holistic approach leverages sophisticated tools/tradecraft, such as hypothesis-based threat analytics, artificial intelligence, and cyber threat intelligence. This tradecraft is backed by a flexible and scalable microservices-based data processing architecture, deployable both in the cloud and on-premise. This automation allows us to generate, triage, and prioritize hundreds of high-confidence datasets that provide multiple overlapping windows into potential threat activity. By pairing these tools with our highly-skilled analysts, we have created a scalable and repeatable process that reduces APT dwell time and provides our clients with the knowledge necessary to strengthen network defenses and mitigate adversary activity. Coupling TH and analytics hones focus on the adversary, which helped us to identify a threat’s spyware executing code across our client’s operation systems (Windows, Linux, OSX).
How we are different
• Our threat hunting is driven by our expanding Hunt Analytic Library, with 500+ analytics covering threat activity across more than 75% of the ATT&CK framework. We ingest up-to-the-minute cyber threat intelligence, and learn from hands-on purple teams (pitting our world-class red team experts against our top-notch threat hunters).
• We leverage artificial intelligence to provide sophisticated enrichment, triage, and prioritization of massive data sets to ensure that our hunters are looking at the anomalies and data haystacks where threats are most likely to be hiding. We not only find the outside actors, but our threat hunting identifies insider threats – including a skilled system administrator conducting malicious activity.
• Our hunters are backed by a massively scalable data processing architecture that can process, enrich, analyze, and tag billions of records a day. Our cyclical, analytics-driven process allows our hunters to consistently find the anomalies and breadcrumbs in terabytes of data that lead to discovery of advanced threats. Among other confidential success stories, in 2018, our TH proactively identified a dormant adversary seeking proprietary information through a client’s email servers – a threat actor who circumvented detection from all SIEMs and the company’s security operations center.


