Photo Gallery
 |
 |
Bracket Computing


Additional Info
| Company | Bracket Computing was founded with a big goal: To empower enterprise IT with a single set of security controls to stop the spread of malware, malicious insiders and mistakes without impacting the speed and agility of the self-service cloud. |
| Company size | 50 - 99 employees |
| Website | https://brkt.com |
NOMINATION HIGHLIGHTS
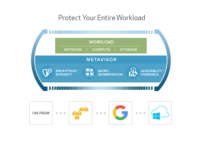
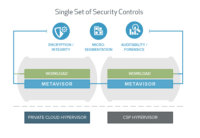
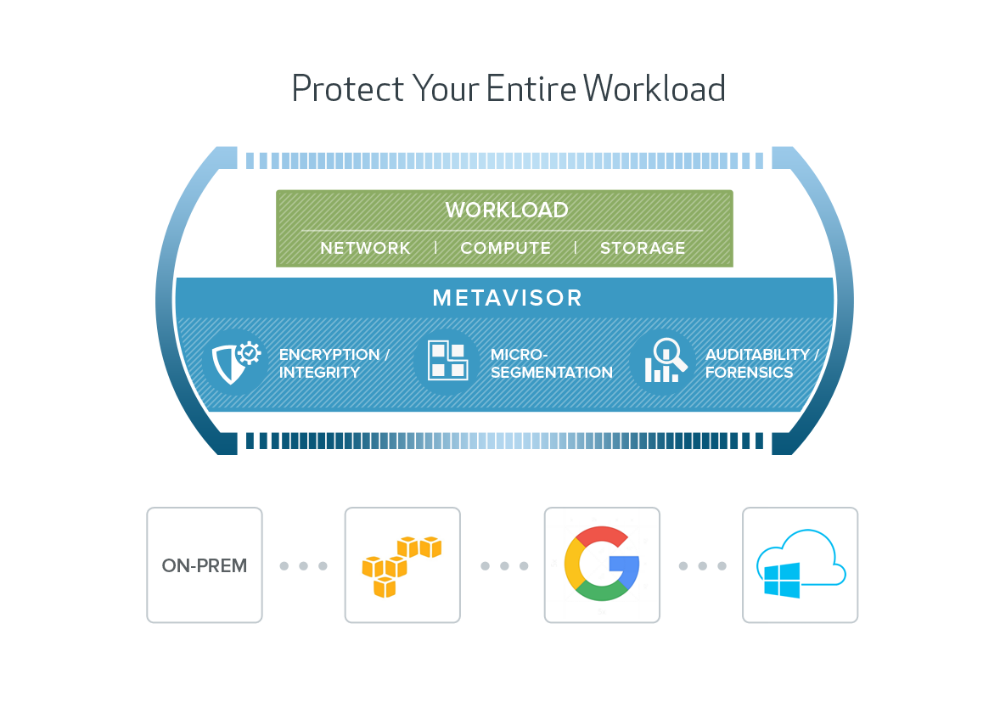
The Bracket Computing Cell is security software that provides Full Workload Isolation, extending encryption, integrity and micro-segmentation, beyond just the network to include a workload’s storage and compute resources. It’s provable security, with all the visibility, forensics and auditability you need built in as a steady state. Designed as a single set of advanced IT controls, the Cell works everywhere you do—across on-premise VMware clouds, as well as Amazon Web Services, Microsoft Azure, and Google Cloud Platform. At the heart of the Cell sits the Metavisor™, an advanced virtualization technology that allows protection services to be inserted and audited transparently, with no impact to developers or data center operations teams. Now enterprises can ensure separation of duties and compliance in a self-service world.
The Metavisor is an advanced virtualization technology that allows the insertion of protection services, without any modifications to the guest OS or applications. Running between the guest OS and the cloud hypervisor, the Metavisor is transparent and immutable to the guest OS. Designed for production workloads, the Metavisor’s position in the stack allows it to combine the granularity of a host-based security solution while providing separate network, storage, and compute-based controls that cannot be turned off.
How we are different
1. Unlike other solutions, which rely on development and operations teams to deploy security agents or virtual appliances, the Computing Cell’s advanced virtualization technology enables central IT to retain control over security policies independent of—and without impact on—other teams. This approach yields security that cannot be turned off, even with root access, and has the added benefit of reducing the agent clog created by other approaches.
2. Conventional, network-based security solutions, which rely on managing agents or virtual appliances across heterogeneous controls, incur significant operational overhead and complexity. With the Computing Cell, enterprises get a single set of security controls that work consistently across clouds, enabling IT to overcome security and compliance challenges.
3. Other security solutions typically deliver security for just one part of a workload: The network, storage, or compute. But protecting just one component leaves others unprotected - for example, network security mechanisms risk leaving sensitive data that is copied or moved on the dynamic cloud unprotected. The Computing Cell secures the full workload (network, compute, and storage) with always-on encryption of data at rest and in motion, micro-segmentation, and forensics and auditability capabilities.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



