Photo Gallery
 |
 |
BreachLock Attack Surface Management (ASM)

Additional Info
| Company | BreachLock |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | breachlock.com |
NOMINATION HIGHLIGHTS
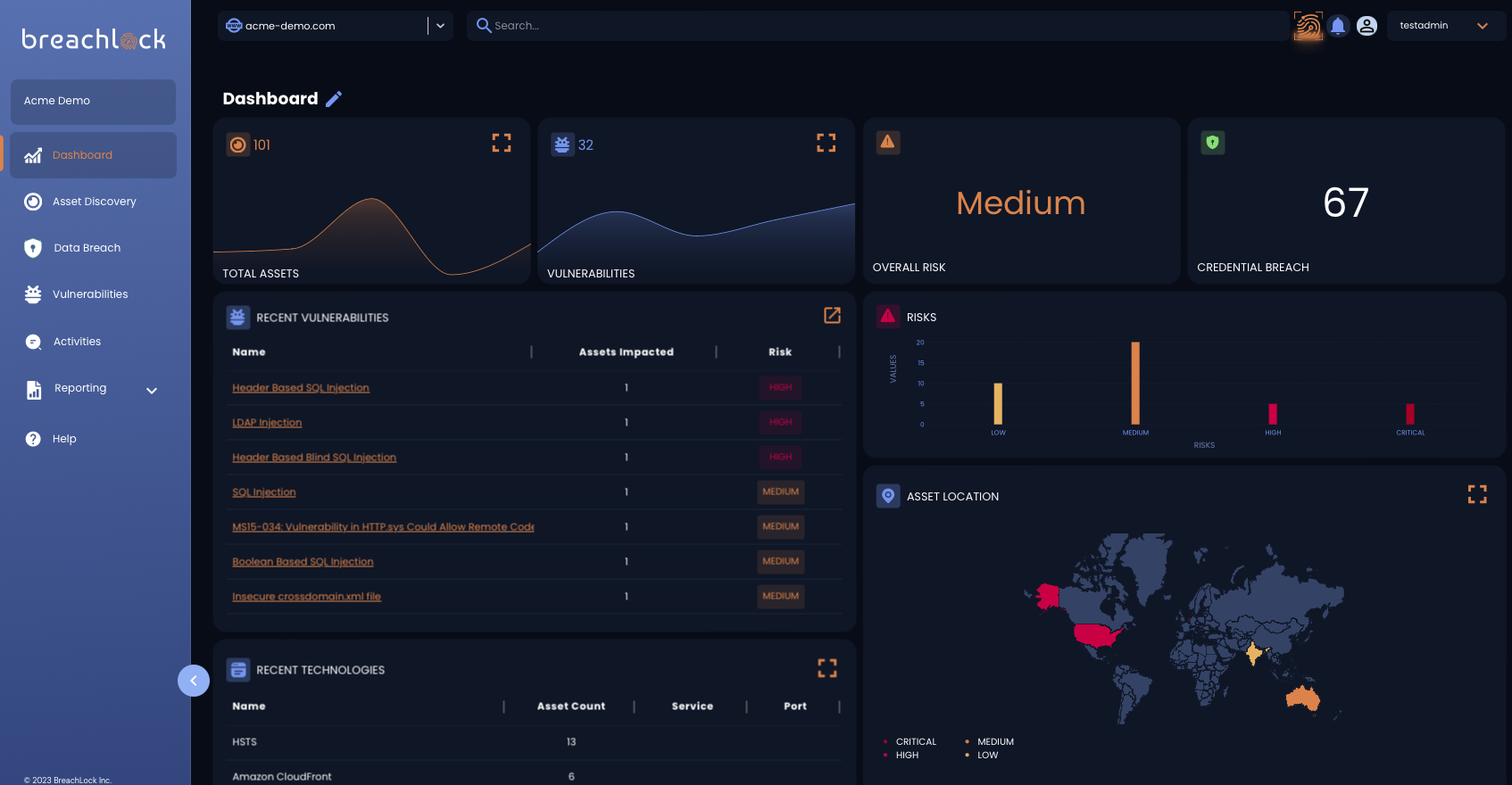
BreachLock Attack Surface Management (ASM) for internal and external attack surfaces identifies and prioritizes risks and exposures at their most critical attacker entry points based on actual risk, providing a strategic starting point for more granular pentesting and red teaming initiatives. By leveraging risk-based prioritization, BreachLock’s clients save time and resources, focusing efforts precisely where needed, thanks to real-time, accurate risk assessments.
BreachLock offers a more advanced and nuanced approach to ASM, delivering enriched contextual insights beyond a simple attacker’s view. Through the BreachLock Platform and AI-powered technology, we analyze vast data amounts in real time to identify complex patterns and anomalies within the most exploitable points of interest by an attacker to accelerate the effectiveness of your ASM testing and outcomes. BreachLock ASM proves a strategic starting point for more granular pentesting and red teaming initiatives.
BreachLock provides clients with a comprehensive understanding of their assets’ attractiveness to attackers, their exploitability, likely attack paths, and necessary refinements during reconnaissance.
BreachLock’s ASM process begins with asset discovery, cataloging exposed digital assets, including third-party-owned ones like those from cloud providers or partners, asset classification by risk tolerance, sensitivity, and business importance, followed by a thorough risk assessment considering vulnerabilities, threats, and attacker tactics. Prioritization and risk scoring enable focused remediation efforts guided by actual risk severity and potential impact on operations and the bottom line. Actionable recommendations accompany newly discovered vulnerabilities, providing a clear path to mitigation.
BreachLock’s human-delivered, AI-powered, and automated solutions for Attack Surface Management, Penetration Testing as a Service (PTaaS), and Automated Pentesting and Red Teaming enable enterprises to continuously discover, prioritize, and mitigate exposures with real-time, evidence-backed results.
Key Capabilities / Features
BreachLock ASM offers continuous identification and prioritization of assets at critical attacker entry points across both internal and external attack surfaces. Our solution scans internal infrastructure, including workstations, servers, network infrastructure, and endpoints, as well as assets accessible from the public internet, such as web applications, cloud services, and domain names, to identify potential security threats.
Our analysts investigate potential incidents to determine whether if they are true positives containing sensitive information. We deliver AI-driven contextual insights around each vulnerability with evidence-based reports.
BreachLock's Attack Surface Management solution begins asset discovery, identifying and cataloging all exposed/internet-facing digital assets, including those owned by third parties such as cloud service providers, supply chain vendors, contractors, or partners. Assets are classified according to risk tolerance, sensitivity, and importance to business continuity. Following this, BreachLock analyzes potential risks by assessing vulnerabilities, threats, and attacker TTPs (tactics, techniques, and procedures) pertaining to the assets. Based on insights from the risk assessment, the BreachLock prioritizes vulnerabilities and exposures for remediation – known and unknown – based on their risk scores determined by the severity and potential impact on the organization’s operations and the bottom line, as well as OSINT, CVSS, and known breach data. The BreachLock Platform provides real-time results of risk exposure, delivering AI-driven insights and actionable intelligence to accelerate remediation.
BreachLock ASM proves a strategic starting point for more granular pentesting and red teaming initiatives.
How we are different
• BreachLock's standardized, built-in framework enables predictable and accurate results in real-time, every time to establish genuine benchmarks and measure the progress of your security posture over time.
• BreachLock's AI technology identifies complex patterns and anomalies, providing enriched contextual insights beyond the attacker’s view. BreachLock provides context around the attractiveness of our clients’ assets to attackers, their level of exploitability, likely attack paths, and refinements necessary during reconnaissance.
• Having conducted thousands of penetration tests, ASM scans, and automated testing across different operating systems, customers, and industries, our data contains expansive threat intelligence and remediation best practices to make real-time inferences and intelligent decisions regarding your security ecosystem.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



