Photo Gallery
 |

 |
Breeze Security

Additional Info
| Company | Breeze Security |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://www.breeze-sec.com/ |
NOMINATION HIGHLIGHTS
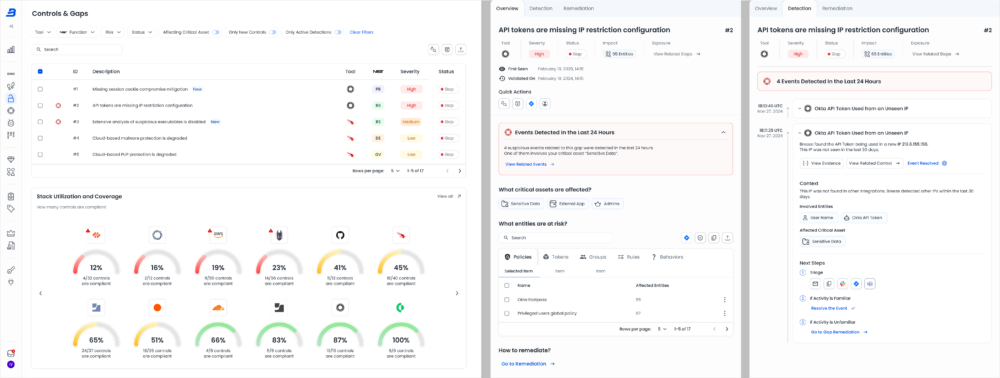
Breeze unifies the security stack to protect organizations’ most critical assets against multidimensional threats. Instead of focusing on a single domain, such as identities, network security, endpoints, or cloud workloads, Breeze integrates and analyzes all threat vectors. This enables security teams to take the most effective remediation actions using their existing security stack. Whether it’s data loss prevention, NHI and token threats, insider threats, or ransomware, Breeze ensures comprehensive coverage.
Today’s attackers do not limit themselves to one dimension, yet most security tools still operate in silos, leaving gaps, blind spots, and inefficiencies in remediation. Security in isolation doesn’t work—it’s time for a new approach. Breeze connects via API with read-only access to an organization’s defensive controls, such as EDR, IAM, MDM, CSPM, and WAF, as well as critical assets like cloud environments, databases, CRM, and document management systems. By deeply analyzing the attack surface and the organization’s ability to block attacks, Breeze maps security gaps and weaknesses, prioritizes threats based on real-world threat intelligence, and identifies attackers targeting similar organizations.
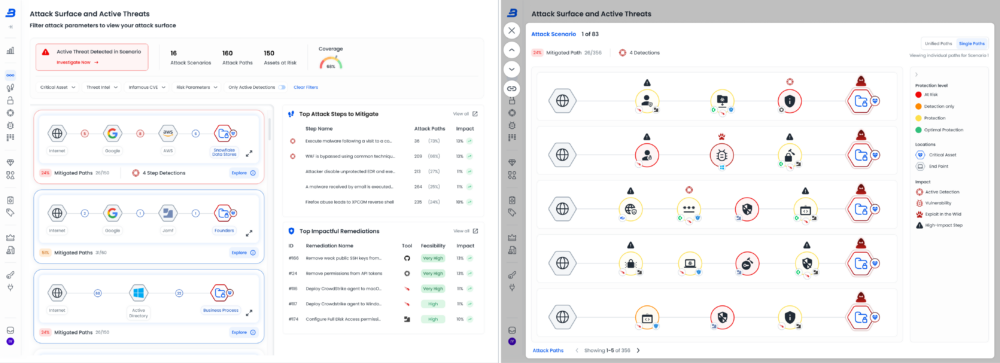
Breeze’s attack graph analysis exposes exploitable attack paths and eliminates them using existing security controls and remediations. But the platform doesn’t stop there. While security gaps remain open, Breeze continuously monitors for attack signals in near real-time, detecting adversaries attempting to exploit vulnerabilities before damage occurs.
Attackers no longer operate in one dimension, so defenders shouldn’t either. Breeze is the only platform designed to combat threats across multiple layers, connecting insights, prioritizing real risks, and dynamically neutralizing attack paths.
Key Capabilities / Features
Breeze provides three key capabilities that elevate cyber resilience and expedite threat mitigation:
1. Holistic Attack Scenario Analysis
We map out potential attacker pathways to pinpoint a single remediation choke point capable of blocking multiple attack steps at once. This maximizes the efficiency and impact of security investments.
2. Proactive Threat Detection and Misconfiguration Identification
By analyzing logs, network data, and system behavior, we uncover misconfigurations and detect malicious actions occurring between existing defenses. Threats are intercepted before they can escalate toward critical assets.
3. Personalized Remediation Playbooks
Using data-driven insights, our platform generates customized remediation strategies tailored to each environment. These playbooks reduce mean time to recovery while keeping engineers in full control of incident response.
Together, these capabilities deliver faster, more effective protection without disrupting existing workflows.
How we are different
• Breeze thoroughly analyze potential attack scenarios to identify the single remediation action that can block the highest number of attack steps, maximizing the overall impact of each mitigation effort.
• Beyond highlighting misconfigurations, Breeze also detect and intercept adversarial maneuvers that occur between existing defenses, ensuring attackers are halted before they reach the most critical assets.
• Breeze provides customized remediation playbooks informed by both log data and behavioral insights, dramatically reducing mean time to recovery while ensuring engineers maintain full control over response actions.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



