Photo Gallery

|

|
Censornet Cloud Application Control

Additional Info
| Company | Censornet |
| Company size | 10 - 49 employees |
| World Region | Europe |
| Website | https://www.censornet.com |
NOMINATION HIGHLIGHTS
The Censornet Cloud App Control module is the most popular component within our integrated cloud security platform and a significant enhancement over traditional Web Security products, meaning that SME’s can benefit from sophisticated control and protection for modern cloud-based SaaS applications with all the rich context, telemetry and reporting that is required for complete visibility of application usage, ShadowIT, and the sprawl of potentially risky apps – eliminating any blind spots that may otherwise contribute to potential data breaches.
As part of a wider platform that encompasses Email, Web and Identity Security, Data Loss Prevention, and Human Risk Management we can help deliver protection across the entire attack surface from a single pane of glass portal. This architecture improves security by design as the core modules can communicate at machine speed – our ASE technology (Autonomous Security Engine) acts to orchestrate the sharing of threat intel, object attributes and other state and context data using AI to ensure that cross-channel attacks are prevented in real-time without security staff having to intervene.
Key Capabilities / Features
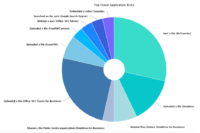
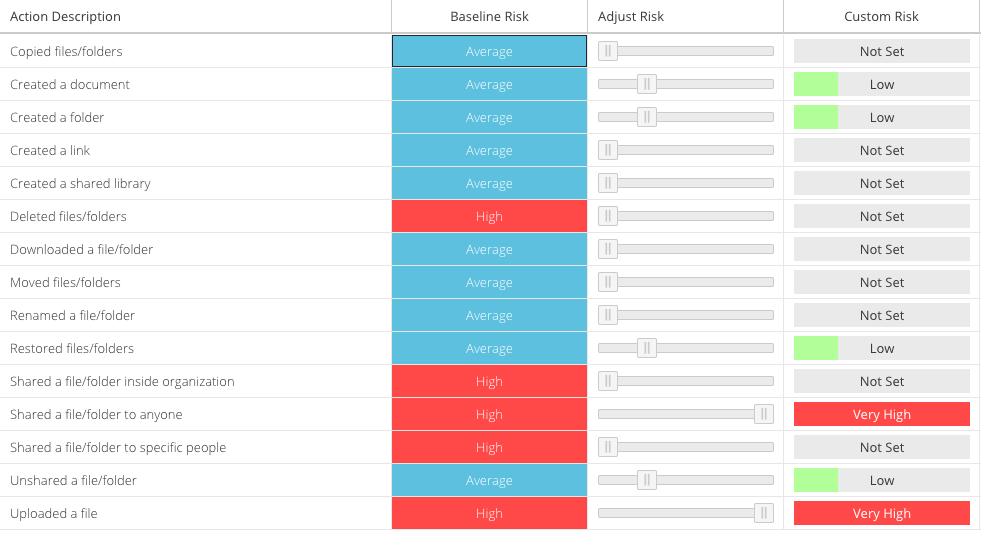
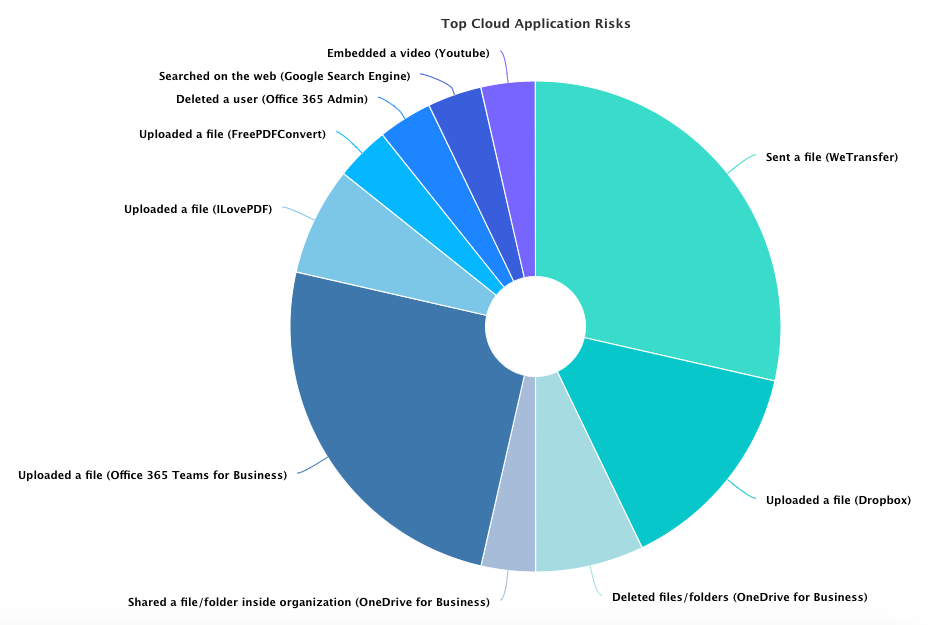
The Censornet Cloud Application Control module has a catalogue of over 1500 of the most popular B2B SaaS apps and 5000+ individual actions that could be performed giving the IT admins highly granular control and monitoring of risk within the user-base. With an autonomous classifier engine and team of engineers, new applications are added to the catalouge on a regular cadence, and even less popular or custom apps can be scanned on demand and added for complete control.
An in-depth reporting and analytics engine delivers interactive reports and dashboards that allow the admins to create and present high-level risk posture reports all the way down to detailed forensic-level insights for incident response and threat intel. Most cloud applications are accessed through a web browser so our technology allows us to capture, inspect and control app requests and responses even when encrypted, however our API connectors also enable native app control and Security Posture Management of AWS/Entra/GCP on top of configuration management of SaaS apps.
With usability at the forefront of our ethos, customers receive pre-defined templates out of the box that cover 80-90% of most customer needs, however should they require custom policies (per user/group/device etc.) this is enabled through our simple Visual Rule Builder that enables powerful rules to be created through a simple drag-and-drop interface.
How we are different
1. The underlying Censornet DirectProtect(TM) Architecture is a zero-proxy solution, requiring no hardware infrastructure or complex configuration - whilst managed in the cloud, enforcement is done on the device, minimising user friction and latency. With hybrid deployment models depending on the device or use-case, and pre-defined policy templates our average time to onboard and go-live is approx. 1 week, delivering incredible Time-to-Value.
2. Our unique Intent and Risk-based methodology means that we can analyse, categorise and control over 1500 applications and 5000 individual actions within those SaaS apps, including modern AI tools. This delivers highly granular control over what users can access and individual tasks they can carry out, maintaining a strong security posture and protection against data loss, yet not impacting the user experience or causing support tickets by using a binary block/allow framework.
3. Our focus is for the small and mid-sized enterprise, delivering many features and technologies normally limited to large Enterprise budgets. Our ethos is to deliver a first-class customer experience (we have a net retention rate in excess of 115%, and have been recognised for Client Support). We do this by ensuring that the appropriate policies can be implemented, deployed and managed quickly and easily without the operational burden that comes with complexity in many of our competitor's products.

Support this Nomination
Share on social media to help this nomination reach the wider cybersecurity community. All qualified nominations are automatically eligible for the Community Choice Award, a separate engagement-based recognition.
All category awards entered by nominees are evaluated independently by our expert judging panel through a structured, merit-based evaluation and are not influenced by community engagement.

