Photo Gallery
|

|
Censornet Cloud Security Platform

Additional Info
| Company | Censornet |
| Company size | 10 - 49 employees |
| World Region | Europe |
| Website | https://www.censornet.com |
NOMINATION HIGHLIGHTS
Censornet’s unified security platform provides all the features you’d expect from bigger brand point-products all accessed through a single cloud-based dashboard. Perfect protection against not only the nefarious cyber criminals trying to hold you to ransom through hacking and social engineering, but also limits your exposure risk to data leaks from accidental insider threat.
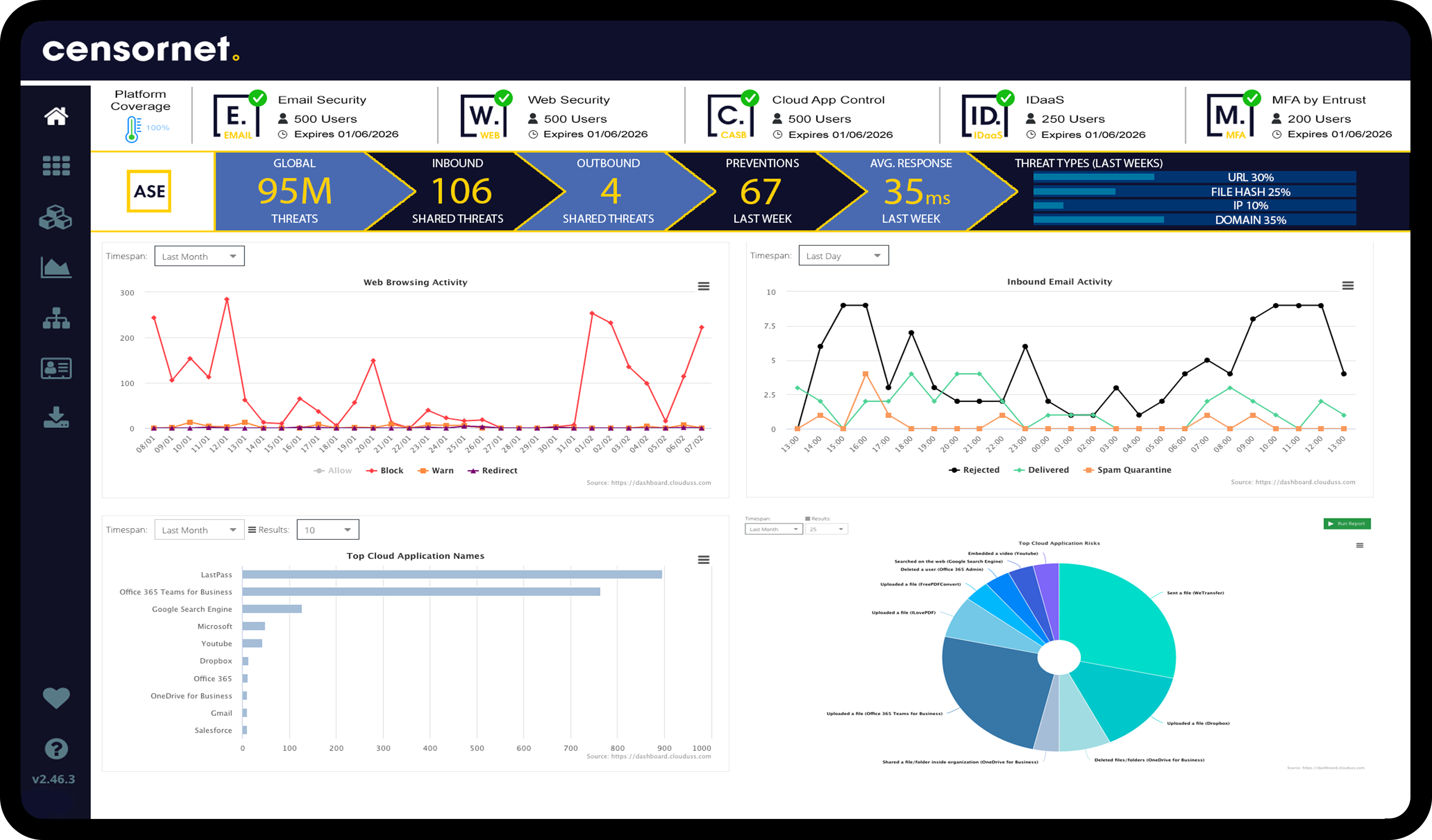
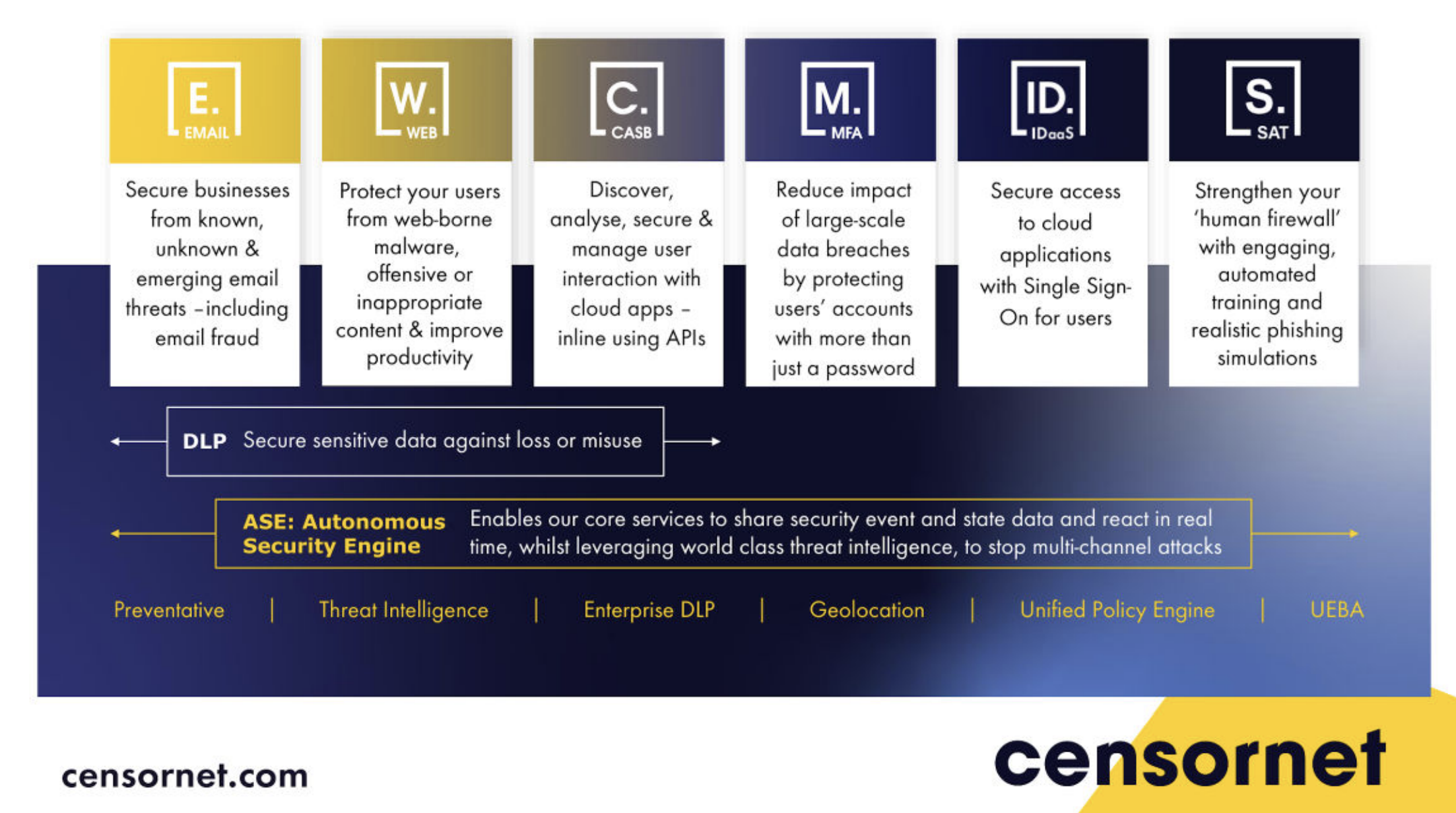
The platform includes modules all centred around user risk posture, from Identity and Authentication Security, multi-mode Email Security with sophisticated tools to stop BEC attacks and phishing, to Web and Cloud Application Security, Data Loss Prevention and Security Awareness Training. But it’s not all about the protection features, the UI is designed for ease of use and richness of intel so the reporting and analytics pages allow the admins to see at-a-glance any potential risky activity, or get to a forensic level of detail in just a couple of clicks.
The unique Cloud Application Control module carefully balances security with user friction, by analysing SaaS applications and categorising each individual action a user could take within a service. This means you don’t have to deploy a binary allow/block rule for unsanctioned apps – you can still allow access for collaboration but control those activities that put you at higher risk of data loss, such as file uploads.
The consolidated and integrated platform requires no hardware appliances or complex infrastructure configuration and with a zero-proxy ethos there is no impact on user experience. This goes a long way in supporting our UK mid-market clients in reducing their operational burden due to multiple interfaces, complex workflows and policy settings, but also helps save cost whilst maintaining a strong risk posture.
Key Capabilities / Features
1. Proxyless architecture maximised security across all devices without the need for costly and complex hardware infrastructure and VPN's.
2. A single dashboard across the entire attack surface simplifies management and reduces operational burden. Time to value is measured in days and weeks, not months as the platform is designed to be deployed in under an hour.
3. End-user AND partner oriented interfaces - whilst the platform is designed to protect organisations and users, it has been designed from the ground up with MSP's and resellers in mind. With full portal branding, custom templates, and an API-driven interface for true multi-tenant usage many service providers can add value to their own clients without the large technology investment.
4. Log streaming features and XDR frameworks mean that the platform can communicate in realtime to 3rd party SOC's, SIEM systems and other agents.
5. Highly granular controls to reduce user friction whilst maintaining a strong posture.
6. Visual Rule Builder delivers a seamless drag-and-drop interface across all modules meaning new license entitlements can be added and become familiar in minutes. Templates and baseline rules are provided out-of-the-box to suit most organisations and can be easily tailored.
How we are different
Combining protection across the entire attack surface, alongside training delivered through a single cloud-based portal delivers significant cost and operational savings to an organisation. Modules within the platform can communicate with each other through our ASE (Autonomous Security Engine) meaning that threat object intel can be communicated across all channels at machine-speed adding enhanced protection against malicious or accidental data breaches or weaponised domains and URL's.
The platform is designed perfectly for the mid-market sector where resources are stretched thin and budgets are modest. The architecture requires no proxies so there is minimal disruption through installation, and the user experience is not negatively impacted. Integrating an enterprise-grade DLP module, but maintaining the same drag-and-drop policy builder as the other modules means that whatever channel the user communicates over, whether it be Email, Websites, or SaaS Applications they can be assured that the files and documents they share are scanned to protect against the accidental leaking of sensitive data.
Balancing usability is key, and therefore our Cloud Application Control module goes a step further than most - by analysing every service in the catalogue and each individual action a user could carry out. This level of granularity means you can still maintain tight control of data egress without causing user friction, increased support tickets, or the inevitable workarounds that people apply to go about their digital day-jobs.


