Photo Gallery
|
Centrify Identity Services Platform

Additional Info
| Company | Centrify |
| Company size | 100 - 499 employees |
| Website | https://www.centrify.com/ |
NOMINATION HIGHLIGHTS
According to the latest projections, global cybercrime-related damage costs are expected to exceed $6 trillion annually by 2021, yet 2/3 of companies are being breached 5x or more. 80% of security breaches involved privileged credential misuse. Additionally, as enterprises move towards cloud-computing models, the notion of a robust perimeter is being eliminated.
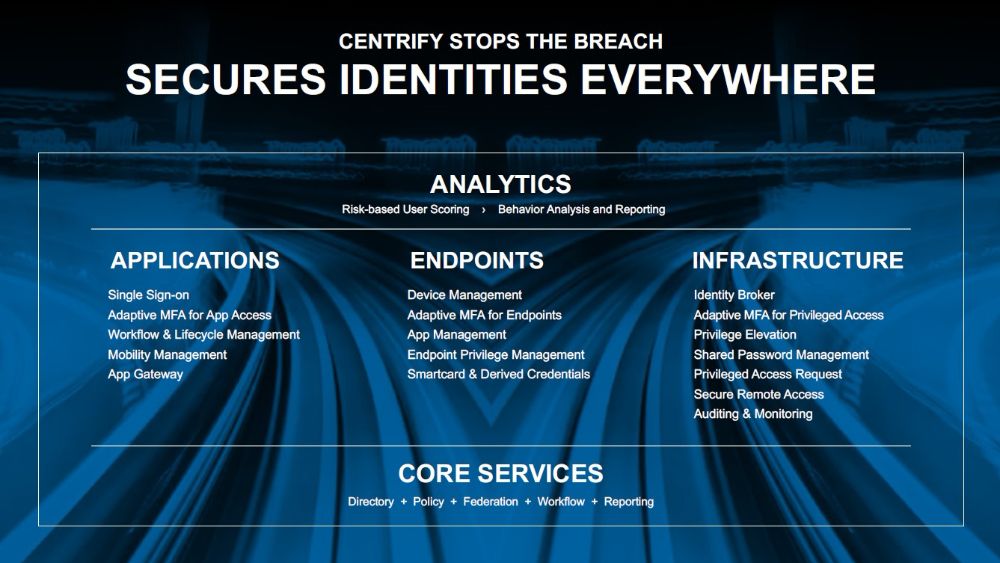
To address this, Centrify enables organizations with a complete Zero Trust security platform to stop breaches through the trifecta of Identity Services for applications, endpoints and infrastructure—both on-premises and in the cloud. The Zero Trust paradigm assumes “bad actors” are already inside your network, follows a “never trust – always verify” methodology and acknowledges the notion of a robust network perimeter no longer exists. Centrify customers are replacing older, network centric approaches to security with access grounded in identity that is critical for today’s hybrid enterprise. By taking a unique approach to controlling both end user and privileged access in the hybrid enterprise, Centrify simplifies the implementation of identity best practices and strengthens an organization’s risk posture.
Earlier this year, Centrify enhanced its privileged identity management solution, enabling organizations to move from static, long-lived privilege assignments to a just-in-time model where advanced monitoring detects and alerts in real-time the creation of backdoor accounts that make it easy to bypass a password vault. Centrify also introduced machine-learning to assess risk based on user behavior patterns, and assigns a risk score and enforces an appropriate real-time decision.
Overall, Centrify delivers stronger security, compliance and end user productivity through its common platform of Identity Services such as single sign-on, adaptive multi-factor authentication, risk-based access control, deep mobile and Mac management, comprehensive privileged access security, privileged session monitoring and risk analytics. In addition to reducing risk, Centrify enables customers to lower technology costs and avoid millions in data breach costs.
How we are different
• Centrify’s strategy is to offer a broader, more effective platform for identity rather than a point solution that focuses on a limited facet such as single sign-on (SSO) to cloud applications or vaulting server passwords. Centrify addresses today’s biggest security issues and helps stop breaches in their tracks. As customers and prospects look to consolidate vendors in the security space, Centrify is unique in that it secures access for all users, all applications and infrastructure, from any device. Centrify provides SSO resources across the enterprise coupled with adaptive multi-factor authentication, mobility and device management, privileged identity management, conditional access policies, and analytics in a single, holistic offering.
• Unlike other vendors that only address a subset of users, Centrify is the only vendor to provide an integrated platform that can secure access for a company’s entire identityscape, including end users, partners, customers and privileged users—who are the most critical access management use case today. All of these use cases are converging and customers will need to make their IDaaS decisions in concert with their PIM decisions.
• Centrify is also the only provider recognized by industry analysts as a leader in both PIM and Identity-as-a-Service.


