Photo Gallery
|
|
 |
CipherTrust Cloud Key Manager from Thales
Additional Info
| Company | Thales |
| Company size | 10,000 or more employees |
| Website | http://www.thalesesecurity.com |
NOMINATION HIGHLIGHTS
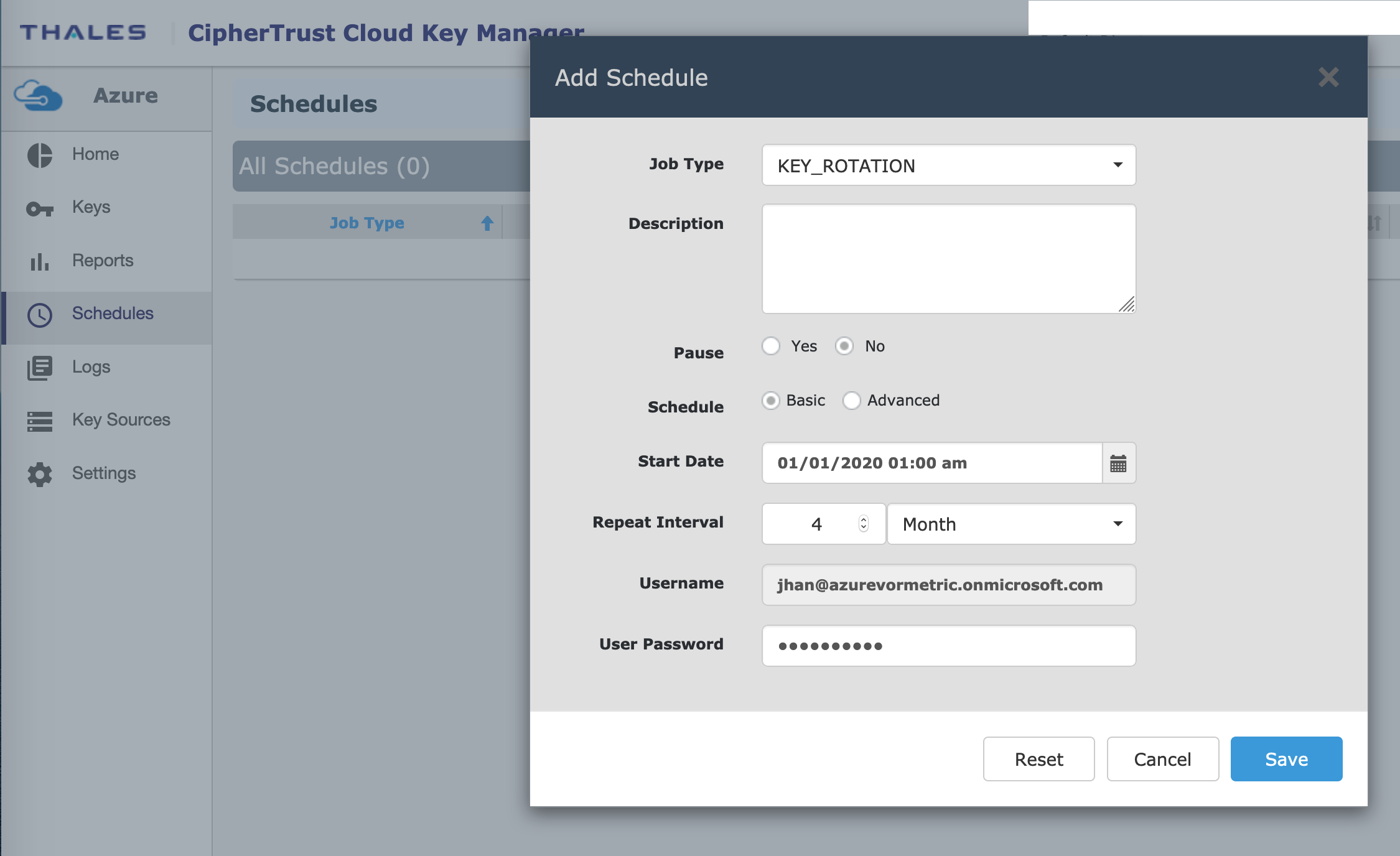
There is a nexus of trends creating complexity across IT and SecOps teams. First is the migration of sensitive data to multi-cloud environments and the increased need for encryption to protect this data. The use of encryption is also on the rise and when properly aligned with key management, delivers powerful controls on data that help organizations both secure their data and attain compliance. Cloud provider encryption is typically used in conjunction with Bring Your Own Key (BYOK) capabilities so that customers can maintain control of their data. However, as the number of cloud vendors and volumes of data migrate to the cloud, so does the complexity to manage and report on all the keys. Thales’s CipherTrust Cloud Key Manager alleviates the complexity of BYOK lifecycle management by abstracting the unique complexities of BYOK across providers to 1) provide FIPS-compliant keys; 2) automate common tasks including some not easily offered by cloud providers; and, 3) delivering clear security reports for auditors.
The product enhances IT efficiency by providing automatic key rotation based on schedules or upon key expiration, centralizing key management across multiple clouds including keys created in cloud provider consoles, and prevents data loss by retaining keys in the key source for use in the event of accidental deletion in the cloud console.
The product enhances security by utilizing key sources certified up to FIPS 140-2 Level 3, and by enabling enhanced separation of duties by separating cloud key management from cloud consoles.
Furthermore, compliance is enhanced by centrally aggregating logging and providing reporting for key life cycle state changes across multiple clouds. Built-in reports also enable administrators to provide comprehensive information to compliance staff. Finally, activity logging to SIEMs can enable threshold-based detection of unexpected behavior indicative of a security breach.
How we are different
• Thales can confidently state that there is no product in the market today that directly competes with CipherTrust Cloud Key Manager.
• When compared to products that support “Cloud BYOK” APIs, there are a few hardware security module (HSM) vendors that provide limited support for cloud provider BYOK. HSM BYOK does not compete directly with CipherTrust Cloud Key Manager as such solutions 1) lack both GUI and RESTful APIs for managing multiple keys at scale; 2) lack automation features provided by CipherTrust Cloud Key Manager such as automated key rotation; and, 3) lack the ability to manage keys created in cloud consoles.
• There are several emerging “Cloud Key Management as a Service” providers, who offer solutions for SaaS-based secure keys, accessible via PKCS#11 or KMIP. These solutions enable customers to obtain a key from a relative secure and high-entropy key source as an alternative to an on-premises HSM. However, these solutions lack 1) integration with “Cloud BYOK”, 2) key life cycle management functions such as key rotation, and 3) the ability to manage keys created in cloud consoles.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



