Closing Backdoors and the Surgical Remediation of Cyber Risks
Recognized in the Category:
Photo Gallery
|
|
Closing Backdoors and the Surgical Remediation of Cyber Risks

Additional Info
| Company | Araali Networks |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://araalinetworks.com |
NOMINATION HIGHLIGHTS
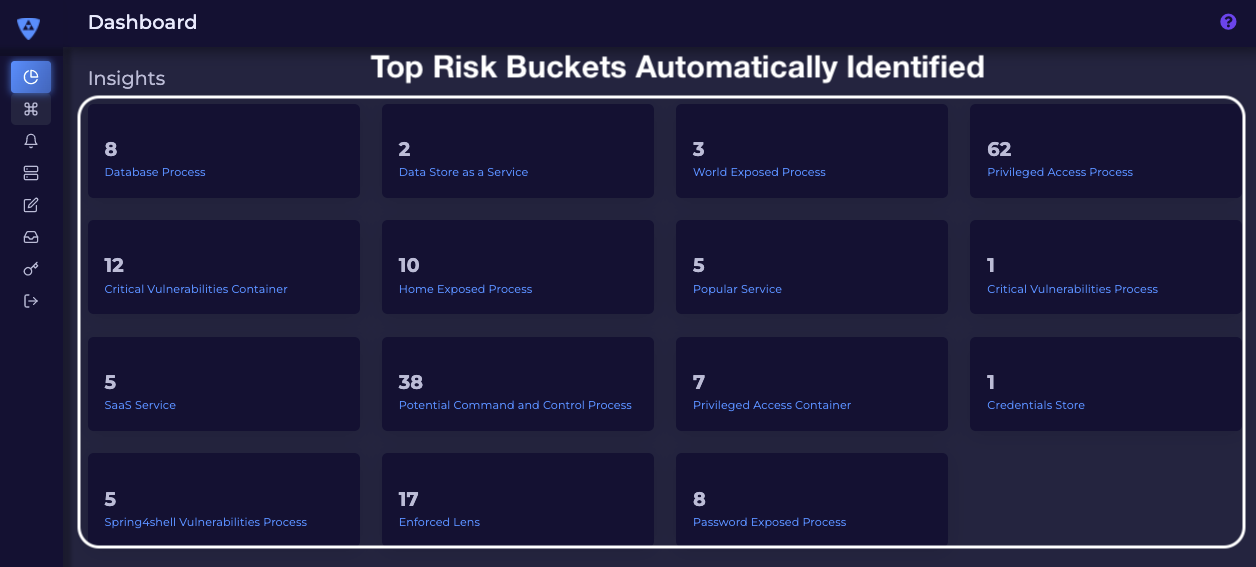
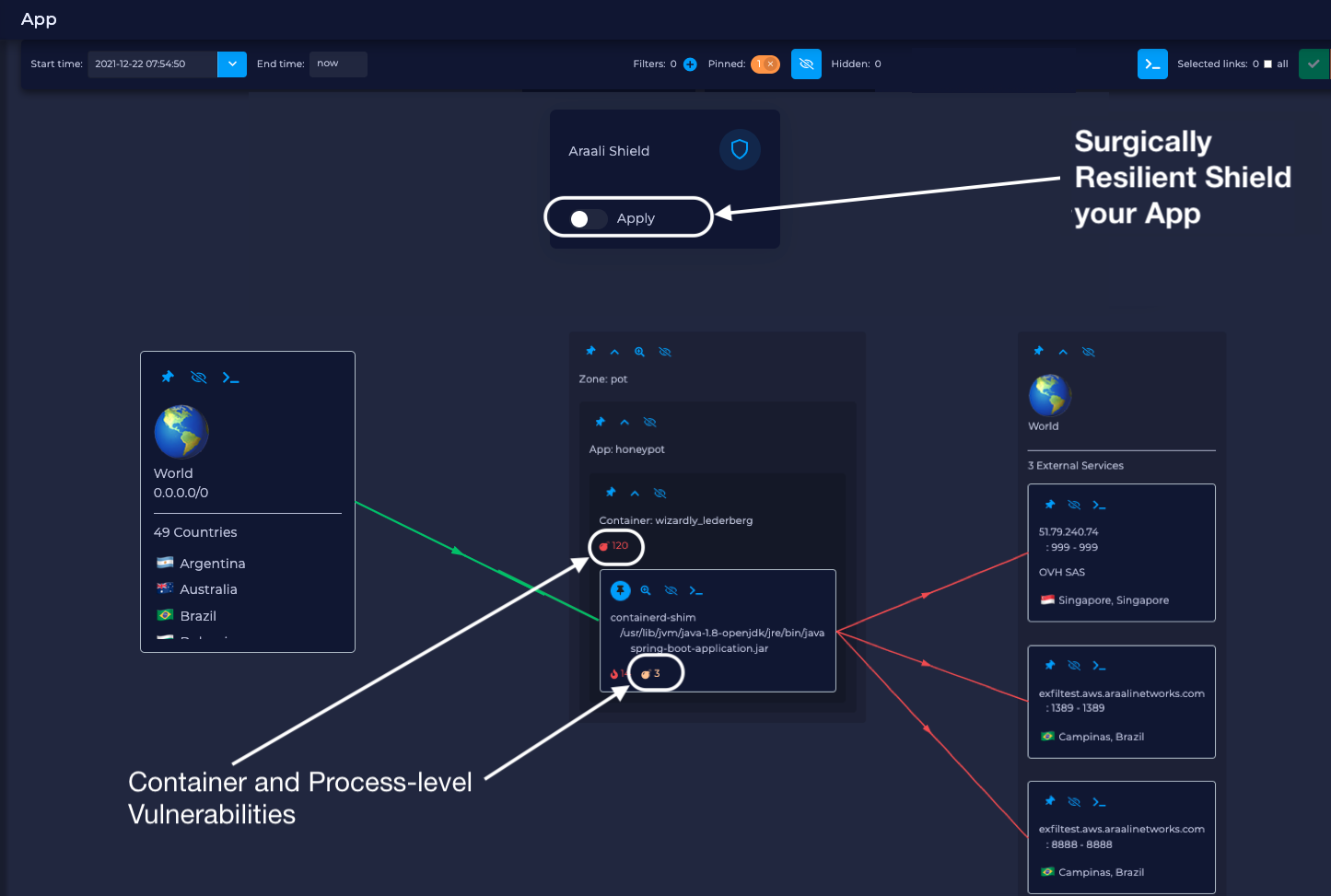
Araali is a cloud security product that helps proactively mitigate top cybersecurity risks. With Araali you can bring your own self-configuring controls to any cloud such that it automatically enables a passwordless least privilege environment for apps. This helps customers strictly enforce internal access controls with explicit trust, proactively shield any remote code execution type vulnerability for any app, and detect advanced threats establishing backdoors to an environment.
Given that the cloud does not provide the safety of the traditional perimeter, has an enormous pace/scale and an ease of misconfiguration, security teams rely on Araali to mitigate risk by taking a two-prong approach:
1. Using allowlist for applications that only permits good behavior (which is difficult to do because of the dynamic nature of cloud-based apps and the inability of network-based tools in this environment). Araali solves this by automatically assigning identity to every app, continuously authorizing connections, and deterministically monitoring app behavior to prevent supply chain attacks, zero-day exploits, misconfigurations, ransomware, and data breaches.
2. A focus on “protect-surface,” which includes databases, vulnerable apps, and internet-exposed apps, versus trying to protect everything.
Some of the many use cases include:
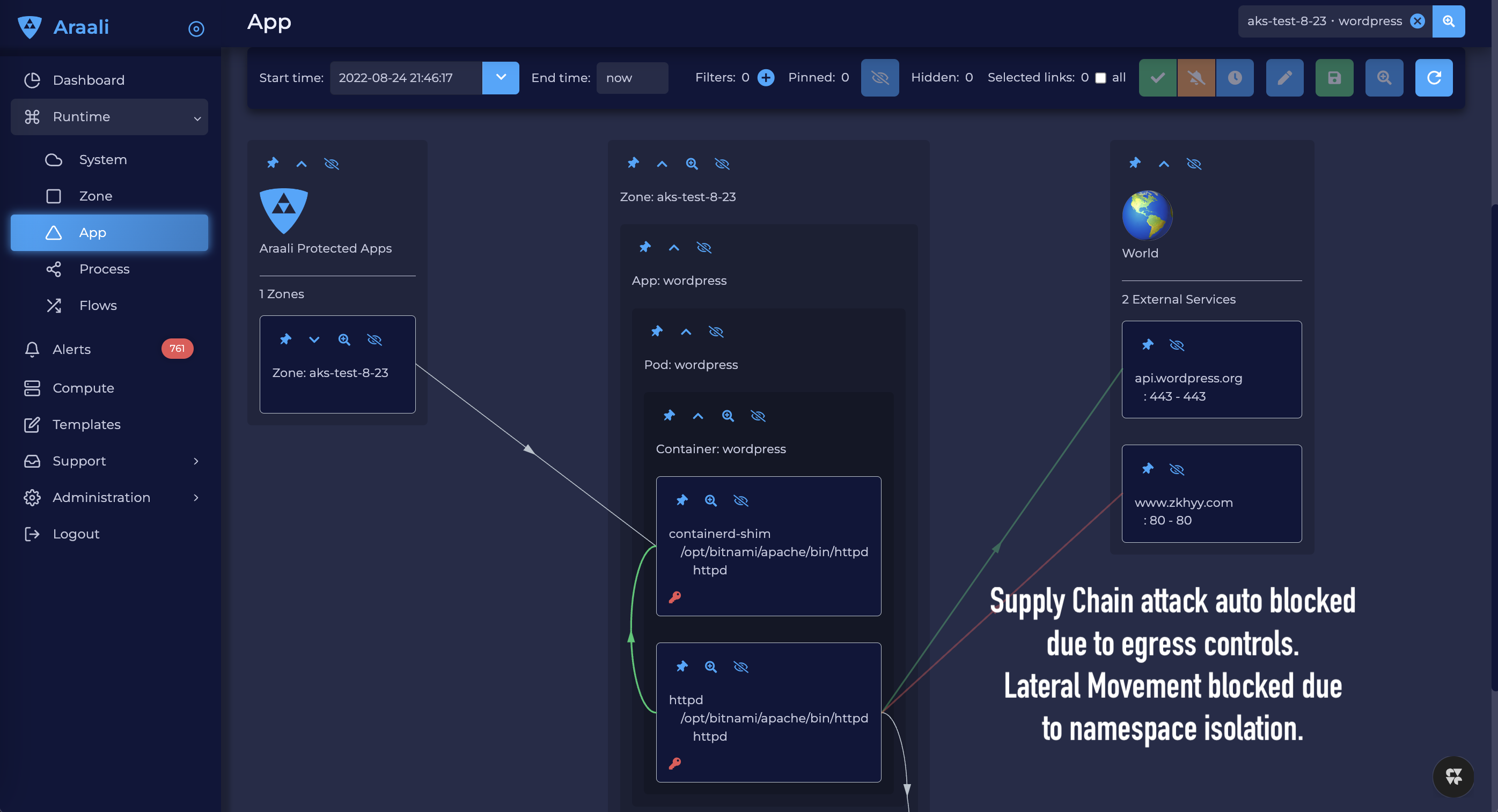
* Monitoring and Preventing Supply Chain Attacks
* Preventing Zero-Day Exploits
* Flagging misconfigurations – over privileges, accidental internet exposure, open unused ports, and too much implicit trust.
* Protection against Ransomware – Araali can easily prevent ransomware by:
* Shielding vulnerabilities from getting exploited
* Preventing lateral movement
* Preventing egress connection to C2 servers. For a successful attack, all three need to happen.
* Protecting Crown Jewels and Data Breach – only whitelisted processes with the right authorization to talk to the database. This prevents bad actors or malware from talking to the database.
The low footprint, easy policy management, and light touch make it easy to manage and deliver a significantly low TCO
How we are different
Araali uses a very novel approach to holistically solve security challenges across the cloud. Specifically, three of its differentiators are:
1) A Focused outcome: Araali not only prioritizes cyber risk through the elimination of backdoors, continuous monitoring and insights about the protection surface, but also allows users to remediate those risks surgically. It deploys with a single command, uses super optimized eBPF-based enforcers, that provides enterprise-grade security with performance.
2) Technology: It uses a patented technology to create an identity-based graph of runtime in a deterministic way. This reduces false positives.
Identity and deterministic traits allow Araali to create a stable baseline of application communication. This allows Araali to easily spot behavior drift, a hallmark of modern attacks.
3) Easy operations and lower TCO, ideal for lean teams, No performance penalty, No Business disruption


