Photo Gallery
|
|
CloudHunter

Additional Info
| Company | Sift Security, Inc. |
| Company size | 10 - 49 employees |
| Website | http://www.cloudhunter.io |
NOMINATION HIGHLIGHTS
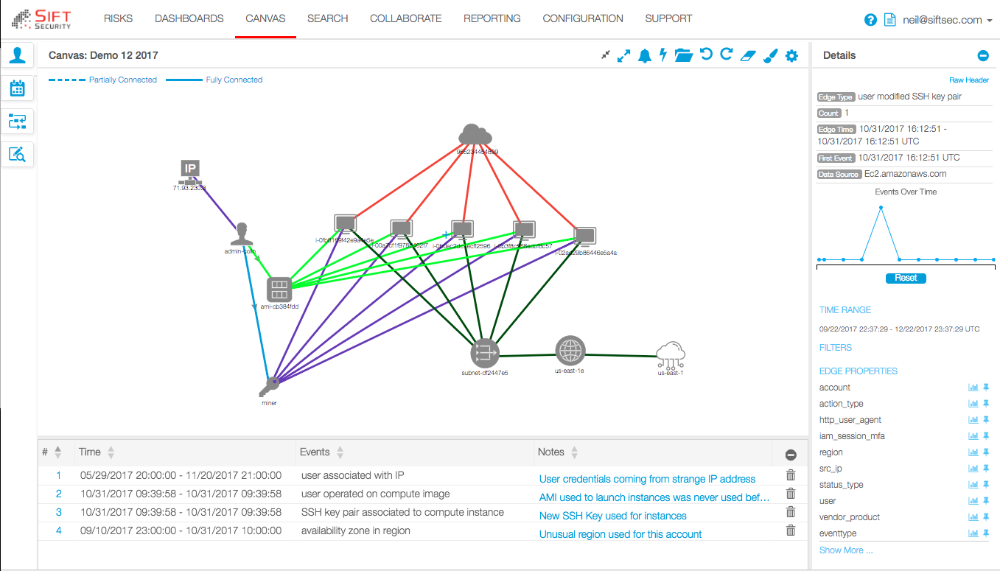
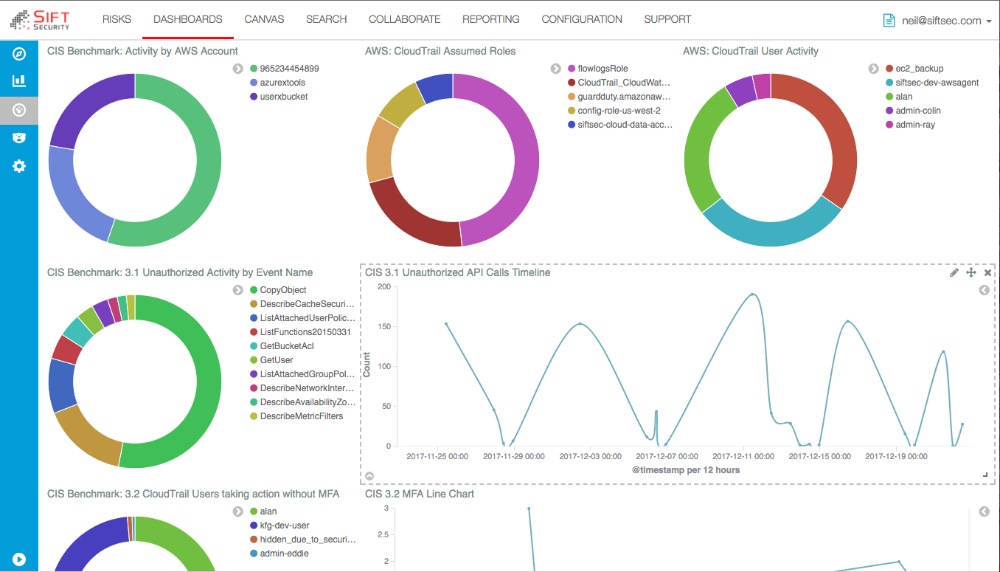
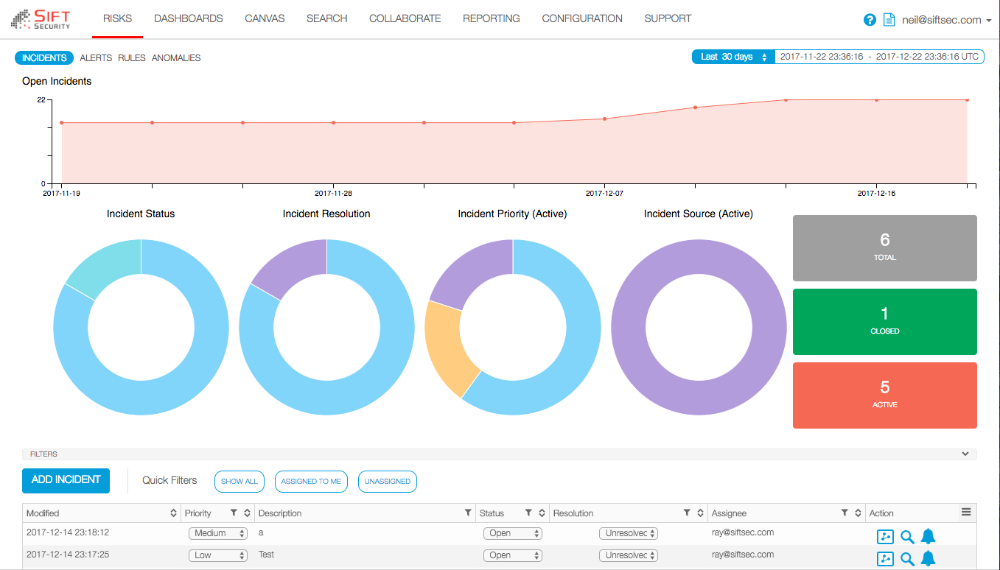
With CloudHunter by Sift Security, you can easily stay in compliance with best practices, as well as quickly detect and respond to risks in your cloud infrastructure. Sift Security uniquely leverages graph analytics & machine learning to supercharge your cloud security team. Don’t waste countless hours searching through logs to identify and respond to incidents. CloudHunter ingests native cloud flow logs and API logs from leading cloud providers, builds relationships those logs, provides meaningful analytics, and alerts you on potential threats. Incident responders can rapidly investigate events in the dynamic cloud infrastructure and seamlessly take action. CloudHunter also provides you with integrated help desk ticketing and reporting, that allows you integrate with your workflow as part of your Security Operations Center (SOC). As a security analyst, you can quickly review and respond to prioritized alerts specific to your cloud environment, including Account compromise, data exfiltration, Bitcoin mining, and more.
How we are different
1. Sift Security's cloud security experts have curated the most valuable data from your cloud logs, and created high value detection use cases and playbooks. As a result, the product can be deployed in minutes and immediately provides valuable insights and a simplified experience for security and devops professionals responsible for maintaining security for cloud infrastructure.
2. Sift Security leverage graph database technology and analytics to naturally correlate cloud data across multiple cloud as well as related data and context. As a result, we enrich alerts to identify higher confidence threats mapped to our trademarked Cloud Attack Chain framework, which enables user to easily sift through the noise of alerts.
3. Sift Security provides flexible API and Automation capabilities, as well as out of the box integrations and automation playbooks. As a result, our customers can easily transition from prioritized alerts to remediation, and the build in playbooks for common, repetitive actions......saving time and frustration.


