Photo Gallery
 |

 |
Code42 Incydr

Additional Info
| Company | Code42 |
| Company size | 100 - 499 employees |
| Website | http://www.code42.com |
NOMINATION HIGHLIGHTS
Today’s business world has been redefined – workforces are widely distributed and traditional network perimeters have dissolved. Collaboration technologies facilitate worker productivity and innovation. While these transformative market forces have introduced pervasive risks to corporate IP, traditional security solutions often are unable to prevent IP from falling into the wrong hands. Code42’s new IncydrTM SaaS solution is built to mitigate exposure from data exfiltration and directly addresses the gaps in conventional security solutions for insider threats, a factor in 66% of data breaches.
Incydr offers organizations an easier, quicker way to secure their endpoint and cloud data from loss, leak, theft and sabotage. Code42’s Incydr allows organizations to detect and respond to risky file activity caused by those inside the organization. This includes exposure and exfiltration activities across on- and off-network computers, the cloud and email. Incydr is platform agnostic and monitors file events happening on Windows, Mac or Linux, a differentiator compared to conventional data security solutions.
The foundation of Incydr’s ability to speed insider risk detection and response comes from monitoring all file activity regardless of what is considered acceptable or unacceptable by security policy. Incydr logs every file event and enriches it with context on the vector, file and user to determine what represents real risk. This allows Incydr to not only reduce alerts and investigation time, but also remediate risk.
Incydr is smart enough to distinguish between everyday collaboration and the file events that represent real risk. It filters out the noise of legitimate work, like sharing files between trusted domains, to reveal only the threats that could harm businesses.
Incydr correlates rich context across three dimensions – files, vectors and users – to speed insider threat response. It surfaces this information along with additional risk indicators to prioritize the events that require immediate security investigation.
How we are different
With Incydr, Code42 is disrupting the market and delivering a solution that takes a totally new approach to detecting and responding to insider threats to data. Conventional approaches to data protection are restricted to identifying only the file activities and file types that fall outside security policies. While conventional solutions are effective at safeguarding regulated data, such as social security numbers, credit card numbers, driver's license numbers, and data regulated under FERPA, FISMA, ITAR/EAR, HIPAA, GLBA, GDPR, they fall far short of keeping sensitive data – IP, trade secrets, source code, and business documents, such as product designs, customer lists, personnel information and financial projections – from winding up in the wrong hands. Code42 Incydr logs every file event regardless of policy to give security teams a clear picture of the real risk to their data.
Conventional DLP, CASB and UEBA tools take singular views of risk and identify file events by only one dimension – vector or file or user. Incydr correlates rich context across three dimensions – files, vectors and users – which filters out the noise of legitimate work, surfaces real risk that requires investigation and speeds insider threat response.
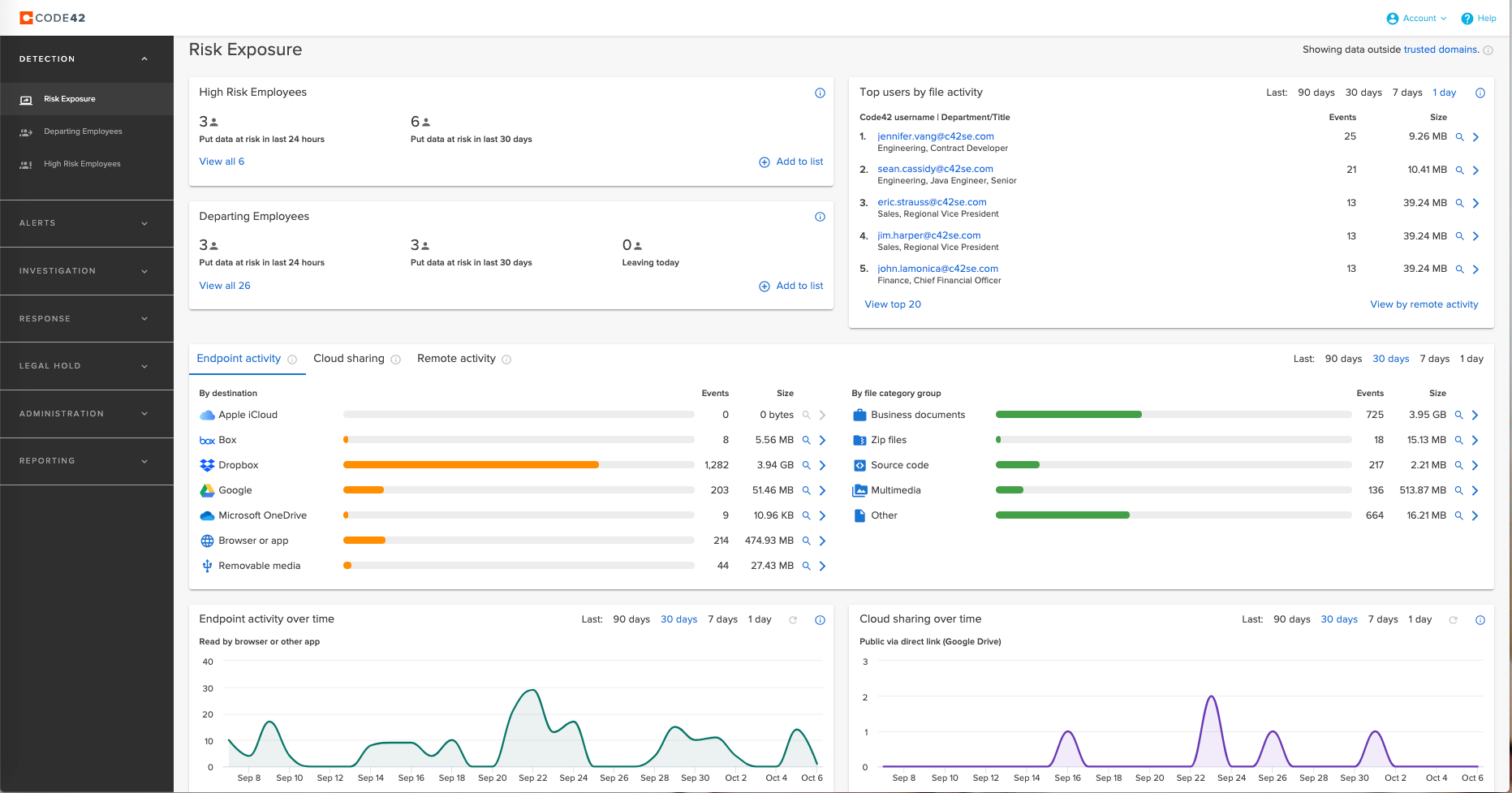
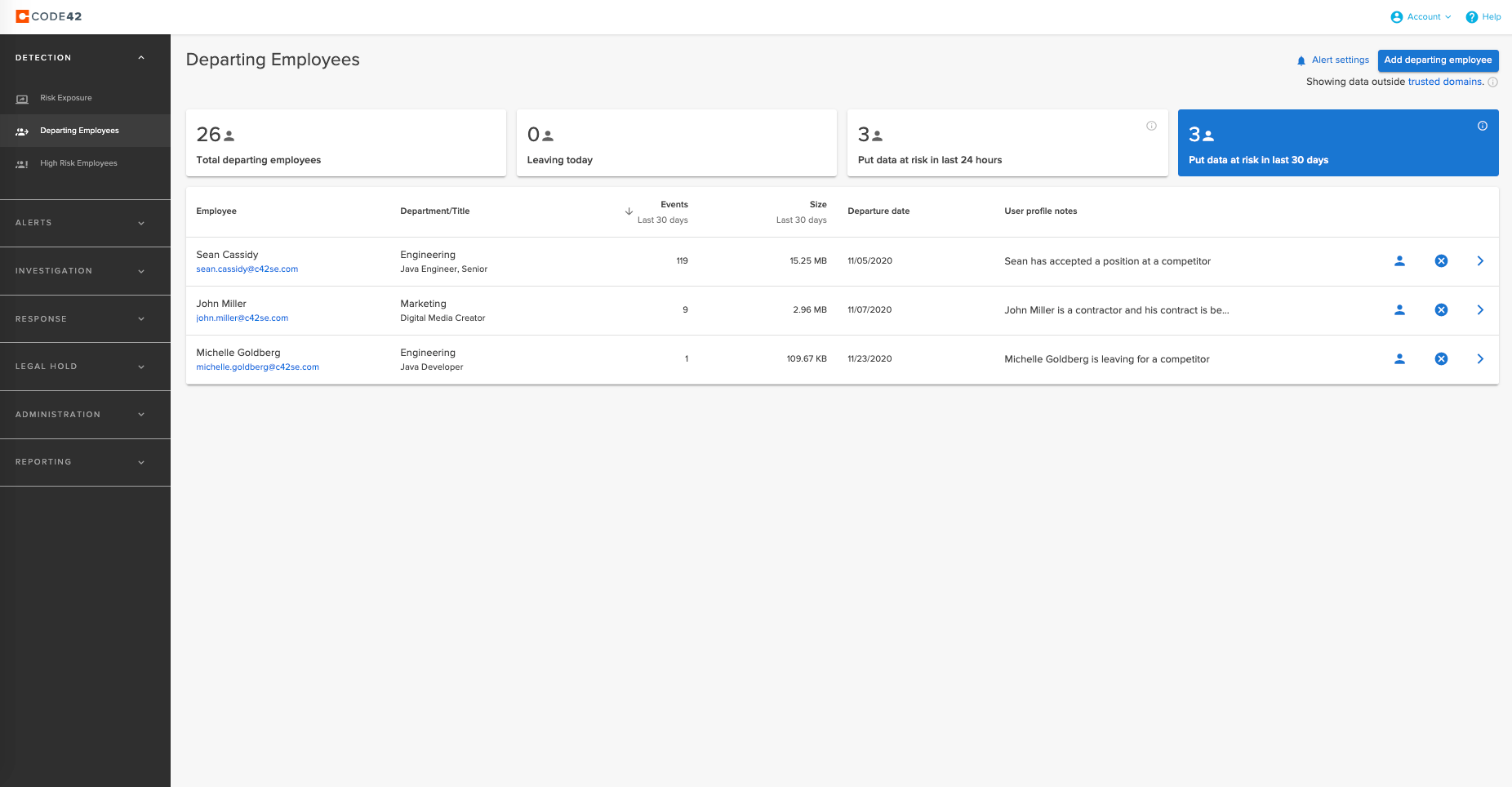
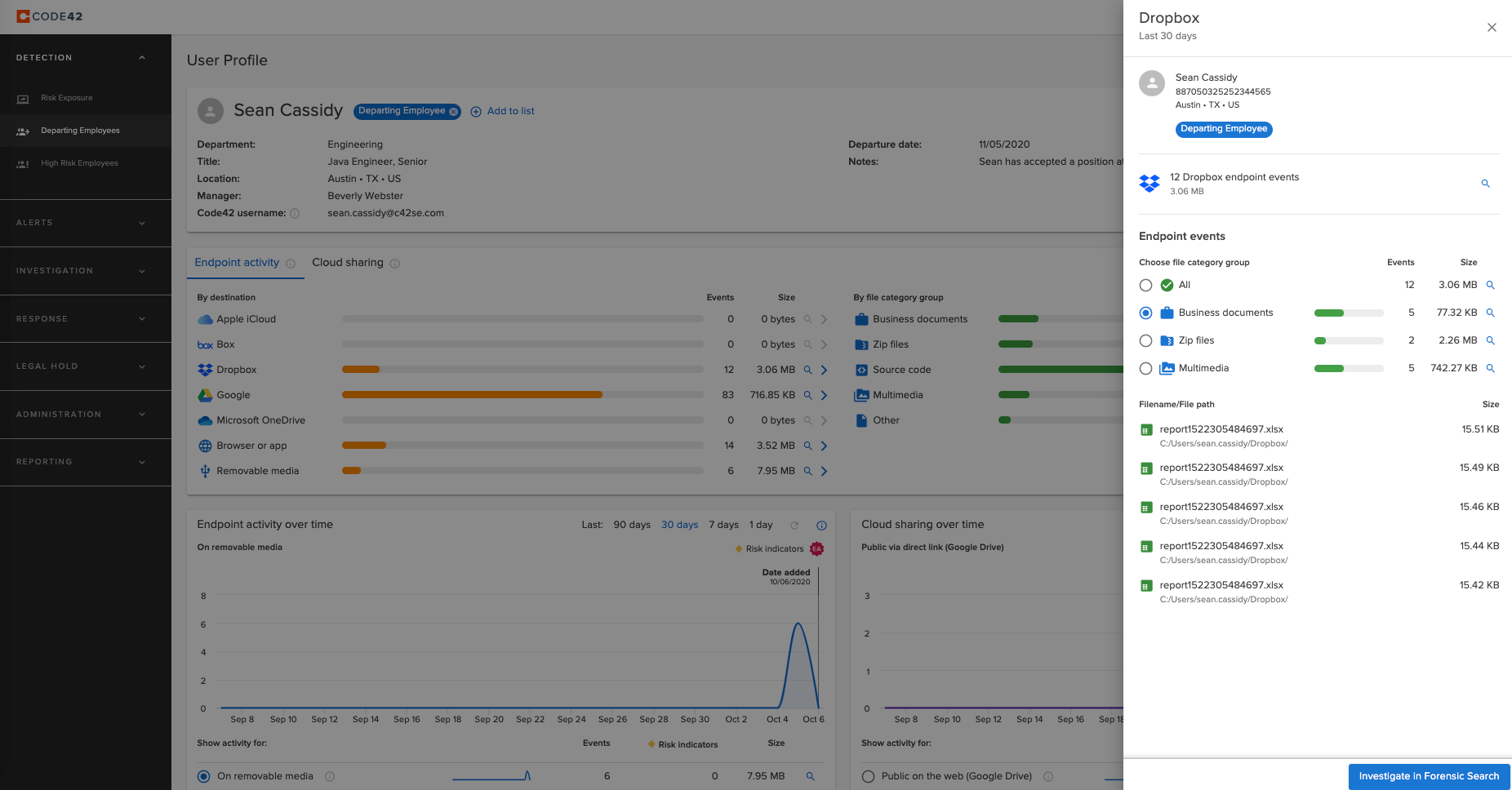
Today remote workers are 85% more likely to exfiltrate data than they were pre-pandemic, Incydr’s remote worker dashboard provides a view of remote employees’ file activity. It gives security teams visibility to file movements when employees are off-network sharing files on authorized and unsanctioned apps. It also provides a dashboard for departing employees, who are most likely to put data at risk, complete with historical file exfiltration activity in 1-, 7-, 30- and 90-day increments. These dashboards provide file visibility and the ability to drill into the actual file within clicks, speeding investigations significantly over competitive solutions.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



