Photo Gallery
 |
 |
Code42 Incydr

Additional Info
| Company | Code42 |
| Company size | 500 - 999 employees |
| World Region | North America |
| Website | https://www.code42.com/ |
NOMINATION HIGHLIGHTS
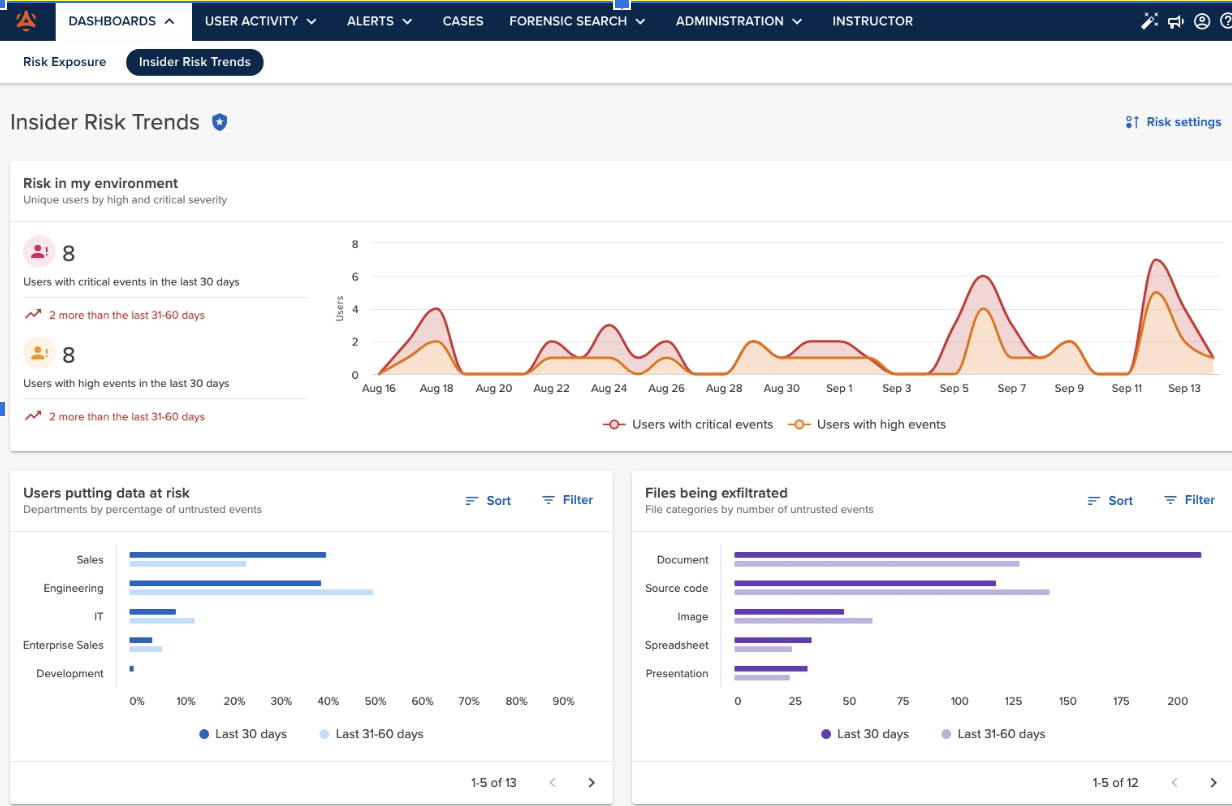
The move to cloud, collaboration and remote work has sped the pace of organizations, accelerating and amplifying data exposure and exfiltration. Workers use personal devices, applications and storage, and 80% use collaboration tools, causing data to be more exposed and subject to exfiltration. This growth in data exposure and exfiltration is Insider Risk. Today, a third of insiders take IP when they leave a company, costing up to 20% of annual revenue.
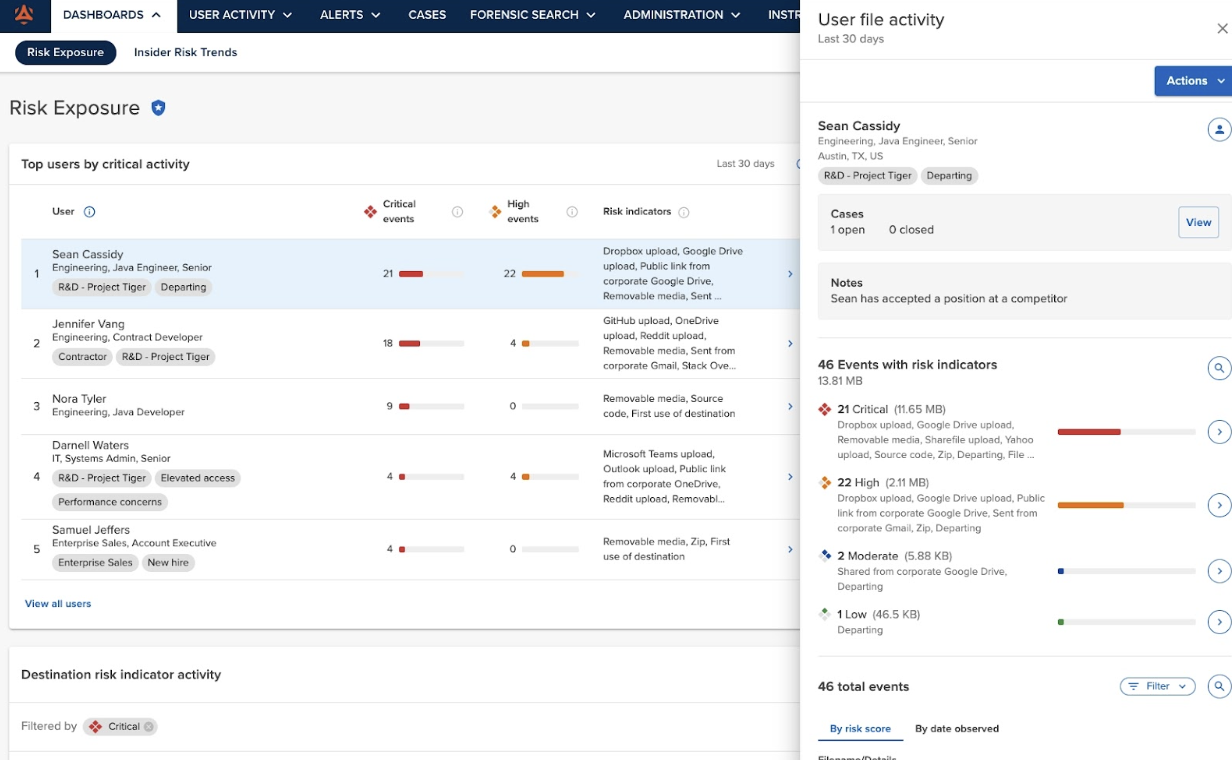
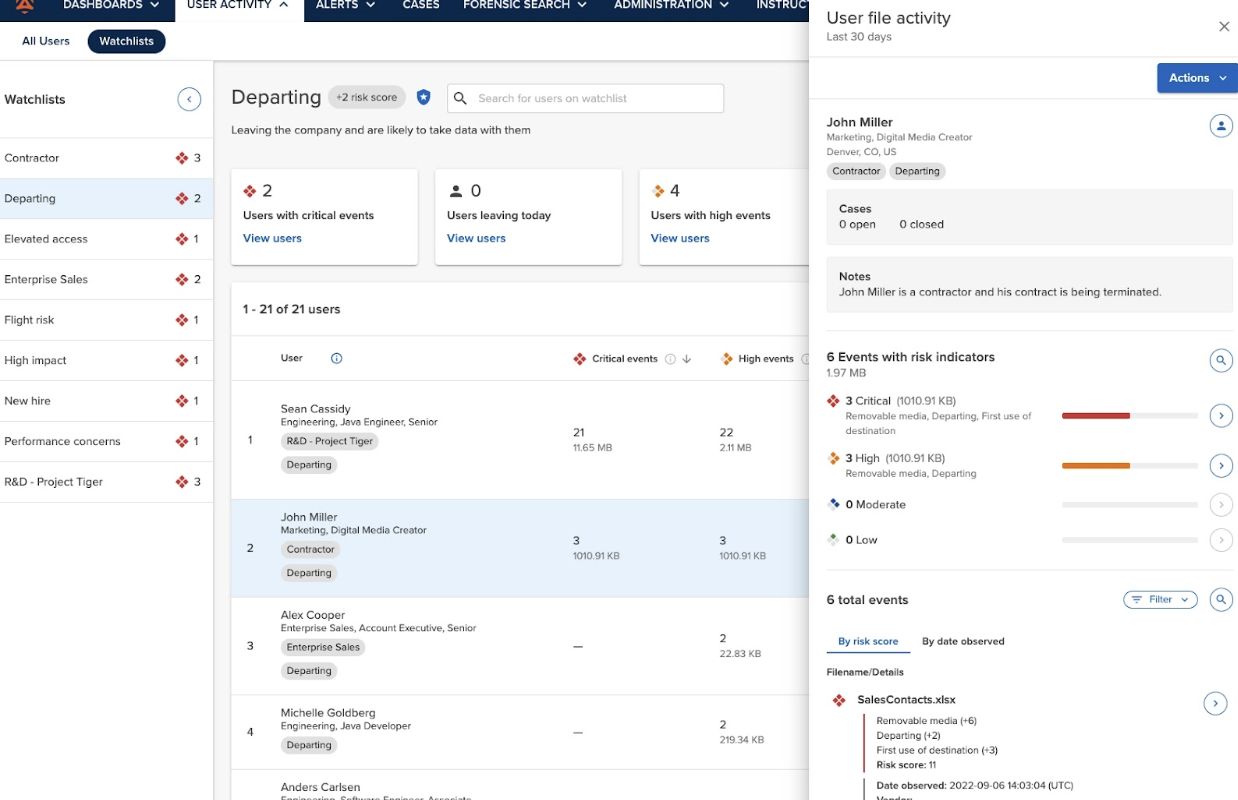
Code42 Incydr is an Insider Risk Management solution that allows security teams to detect, investigate and respond to employee-driven data exposure and exfiltration from computer, cloud and email systems. With Incydr, security teams can mitigate file exposure and exfiltration risks without disrupting employee collaboration. It correlates signals from files, vectors and users to accurately detect Insider Risk Indicators (IRIs) and expedite response. An endpoint agent and direct cloud system integrations provide company-wide and per-user understandings of data risk.
With Incydr, organizations gain valuable insights to understand their risk. They can see how files are moved and shared across their entire organization – without the need for policies, proxies or plugins. Incydr automatically detects when files move outside a trusted environment, allowing teams to detect when files are sent to personal accounts, untrusted destinations and unmanaged devices.
Since Code42 launched Incydr to the market late in 2020, its software developers have worked at an unprecedented breakneck pace issuing 79 releases to production per day to introduce groundbreaking enhancements to the product. Notably, in 2022, Code42 launched an integration between Incydr and its micro-learning solution, Instructor, to accelerate and scale in-the-moment response to risky employee behaviors. Together, Incydr and Instructor enable security teams to effectively manage the dynamic nature of Insider Risk – which includes prioritizing and responding appropriately to the risks that matter the most.
How we are different
- For organizations that rely on traditional data loss prevention strategies, which are incompatible with cloud-based environments and tools, data leaks, loss and theft continue unabated. Organizations need a new approach to data security and Code42 is leading the way with the Incydr IRM SaaS solution. Incydr enables thorough protection from data exposure and file exfiltration that could lead to the loss of intellectual property, source code and trade secrets.
- Traditional DLP and CASB strategies are incompatible with today’s cloud-based environments and tools - data leaks, loss and theft continue unabated. Code42 takes a different approach. Instead of focusing on classifying data, Incydr watches all data. Code42 doesn’t believe in focusing on some users – the “privileged” – because everyone has important data.
- Code42 continues to introduce groundbreaking enhancements that address the biggest challenges organizations are facing. In 2022, Code42 released the following updates for Code42 Incydr:
Integration of Instructor and Incydr, which enables organizations to accelerate and scale in-the-moment responses to risky employee behaviors that could lead to the exposure of sensitive data and IP.
Enhanced IRIs to detect and label file downloads. For example, if an employee were to download a customer list from their employer’s CRM (like Salesforce) and upload it to a personal email account (like Gmail), Incydr would detect the movement and flag the customer list as a CRM document exfiltration.
Enhanced source code exfiltration detection within Incydr to specifically support Git push commands to personal or unsanctioned code repositories.
Support of all major Desktop-as-a-Service (DaaS) and Virtual Desktop Infrastructure (VDI) environments.
Incydr Gov added new data exfiltration detectors for cloud and email systems which allow security teams to monitor unauthorized file movement, spillage and sharing from and within cloud and email systems.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



